The Forgotten Art of vSphere Datastore Permissions
I was recently in a discussion with a group of vSphere administrators about a
particular lab environment, and we were upset that some of the Tier-1 storage
was being used for workloads that weren't quite appropriate for the use case.
Lab environment or not, many vSphere administrators have extended some
permissions to persons outside their group. A good example in my professional
experience was assigning permissions to application administrators for key
features such as remote console and the power button functions of supported VMs.
This saved me work and let them serve their application better, even if I
thought it was maybe a bit finicky.
When it comes to provisioning VMs from a storage perspective, it's a race to the
most precious resource in the data center. I'd go so far as to say that the new
"server under the desk" phenomenon -- an age-old problem taking on a new shape
-- is now VMs residing where they shouldn't. To protect the most critical
vSphere resource (the VM storage), I recently revisited the
datastore permissions construct to solve the problem of ensuring that the wrong VMs
don't end up in that precious Tier-1 storage.
Datastore permissions aren't absolute -- they
apply to the vCenter Server application and below. They don't apply to the
storage fabric. But for the bulk of what we do, this solves the problem of
keeping the right VMs in the right places. The vSphere permissions for the
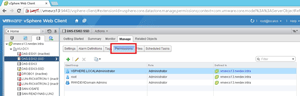
datastores are set on the "Manage" tab of the vSphere Web Client, as shown in
Figure 1.
 [Click on image for larger view.]
Figure 1. Access to a given datastore can be set in the vSphere Web Client.
[Click on image for larger view.]
Figure 1. Access to a given datastore can be set in the vSphere Web Client.
The figure shows that I'm applying specific users and groups for access to an
SSD drive. For those holdouts who refuse to use the vSphere Web Client, the
Windows Client can address datastore permissions. The permissions tab will do
the trick there.
Datastores aren't the only permissions-based
vCenter objects, as you may know. Others include folders, resource pools, vApps
and so on. Do you use the permissions model (and any corresponding roles) for
any complex implementations? If so, how have you built your permissions? Do you
use this outside of vCloud Automation Center (vCAC)? Share your strategies
below.
Posted by Rick Vanover on 08/19/2014 at 1:38 PM