Dan's Take
The 7-Layer Virtualization Model
A deep dive into all forms of virtualization.
- By Dan Kusnetzky
- 10/14/2014
My
Virtualization Review colleague, Tom Fenton, just published a
tongue-in-cheek article that's a wonderful springboard to a deeper and fuller discussion of virtualization as a whole.
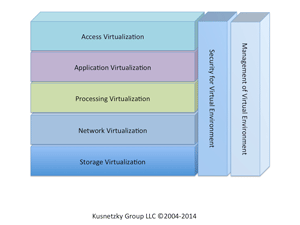
Tom's article humorously discusses how to describe what virtualization is and does to someone -- his Mom, in this case -- who's not all that familiar with technology. It could leave the impression, however, that virtualization is just the use of virtual machine (VM) software. VM software is just one of five things found in the virtual processing layer of my model of virtualization. There are seven layers in this model. The model is described in greater detail in my 2011 O'Reilly Media book, "Virtualization: A Manager's Guide," if you care to read more.
Virtualization is an approach that was developed by the pioneers of computing systems, IBM and Boroughs (now Unisys) back in the ancient days of computing, the 1960s. It involved using unused computing resources to create an artificial, but useful, view of system capabilities. Let's walk through the layers to see what they do:
Virtualization Layer 1: Allows applications to work with remote client devices without change, even though those remote devices were never been thought of or available when the application was written. This is called
access virtualization. XenDesktop from Citrix is an example of products that work in this layer of virtualization.
Virtualization Layer 2: Allows applications written for one OS version or OS to happily execute in another environment; this environment can be a new OS version or an entirely different OS. This is called application virtualization. This type of software would make it possible for an application written for Windows XP to work just fine on Windows 7 or Windows 8. AppZero fits into this layer of virtualization, as does XenApp from Citrix, App-V from Microsoft and VMware ThinApp.
 [Click on image for larger view.]
The Kusnetzky Group Model of Virtualization
Virtualization Layer 3:
[Click on image for larger view.]
The Kusnetzky Group Model of Virtualization
Virtualization Layer 3: Allows one system to support workloads as if it was many systems, or allows one workload to run across many systems as if it was a single computing resource. This is called
processing virtualization. VM software is one of five different types of software that live at this layer. One of today's hottest catch phrases, software-defined datacenter (SDDC), is basically the use of this type of software, combined with a couple of other virtualization layers. Citrix XenServer, Microsoft Hyper-V and VMware vServer are all examples of VM software that lives in this layer of virtualization. Adaptive Computing Moab and IBM Platform Computing LSF are both examples of cluster managers that also live at this layer of virtualization.
Virtualization Layer 4: Allows workloads to access storage without having to know where the data is stored, what type of device is storing the data, or whether the storage is attached directly to the system hosting the workload, to a storage server just down the LAN, or to storage in the cloud. This is called storage virtualization. Another one of today's most talked-about catch phrases, software-defined storage (SDS), is an example of this technology. Open-E DSS, Sanbolic clustered storage, DataCore SANsymphony-V and VMware VSAN are examples of storage virtualization technology.
Virtualization Layer 5: Allows systems to work with other systems safely and securely, without having to care too much about the details of the underlying network. This is called
network virtualization. Yet another current catchphrase, software-defined networking (SDN), is an implementation of network virtualization. Products that offer network virtualization include the Cisco Extensible Network Controller (XNC) and Juniper Contrail.
Virtualization Layer 6: Allows IT administrators and operators to easily monitor and manage virtual environments across boundaries. The boundaries can include the physical location of systems; OSes in use; applications or workloads in use; network topology; storage implementation; and how client systems connect to the applications. This is called management of virtualized environments in the model. This, by the way, is an important part of SDN, SDS and SDDC. A whole host of companies, including AppNeta, BMC, CA, HP and IBM, offer management and monitoring software.
Virtualization Layer 7: Monitors and protects all of the other layers of virtualization so that only authorized use can be made of the resources. Yes, this is called security for virtualized environments in the model. As with management of virtualized environments, this layer is an important part of SDN, SDS and SDDC. Bitdefender, Kaspersky, TrendMicro, McAfee and many others play in this area of the virtualization market.
Thanks, Tom, for making me smile and for giving me an opportunity to delve into one of my favorite topics!
About the Author
Daniel Kusnetzky, a reformed software engineer and product manager, founded Kusnetzky Group LLC in 2006. He's literally written the book on virtualization and often comments on cloud computing, mobility and systems software. He has been a business unit manager at a hardware company and head of corporate marketing and strategy at a software company.