In-Depth
Azure Is the New Microsoft
A company built on the world's most popular OS and productivity software has changed radically in just a few years. The cloud has changed everything for the Redmond giant, and not a moment too soon.
The shift of IT to the cloud is now well underway. In a way, it parallels the rise of virtualization in datacenters: Once, the question was "Why should we virtualize our servers?" Now, that question no longer exists, as virtualization is as common a part of the industry as servers themselves.
It's becoming the same for the cloud, where the mindset is no longer, "Let's try some cloud workloads." Instead, CIOs, CTOs and admins are asked to justify why they should not be using a cloud service for a business function.
Given this new reality, the first step is untangling the various cloud vendors and finding the best fit for an organization's cloud strategy. There are just a few major players in the public cloud space, and Microsoft is right in the middle of it all.
But it wasn't until fairly recently. As the Microsoft Ignite conference approaches, the company faces a time of huge transition from a focus on the consumer to its business-aligned public cloud platform. It's a transition that needed to happen, when you consider industry trends:
- Windows client is declining as a business, due to the overall PC market slump, with smartphones and tablets growing at its expense.
- Xbox has a smaller market share than PlayStation, and has never directly made any money for Microsoft.
- The Surface brand is innovative and the cool devices are copied by other manufacturers, but it's never going to be a large chunk of Microsoft's revenue.
- Windows Phone/Windows Mobile is dead.
This means that Microsoft for consumers is, overall, a dying market. The only growth area is Office 365 consumer subscriptions, which enables users to access Office functionality on mobile devices.
The Players
Enter Microsoft Azure. Microsoft has rapidly built out its platform and is attracting a lot of business. Of course, it's not the only one; it's not even the biggest one. Let's take a brief look at the competition.
It starts with Amazon Web Services (AWS), currently the reigning champion in terms of size. AWS is very good at speaking to startups and developers, but it has a long way to go to match Microsoft's 25-plus-year heritage of trust within enterprises.
There's also the Google Cloud Platform (GCP). But Google Inc. is essentially an advertising company, with even less credibility in enterprises.
Azure remains solidly behind AWS and solidly ahead of GCP when it comes to public cloud. But with Azure matching or in some cases exceeding the offerings of AWS and Google, my prediction is that many enterprises will turn to Microsoft for guidance.
A key differentiator for Azure is that it's the only one with a solution for both on-premises software and cloud services for the long cloud hybrid journey. Azure Stack offers a selection of the services in public Azure, and is also likely to be a success with many businesses that need truly compatible options to run their code.
Azure is currently available in 38 regions around the world, with two more regions in South Africa (the first hyperscale provider in Africa), two in France and two in Australia that are coming online soon. Let's take a long look at Azure, what it offers, and why it's a strong choice for any business looking to rise to the clouds.
Backup and Disaster Recovery
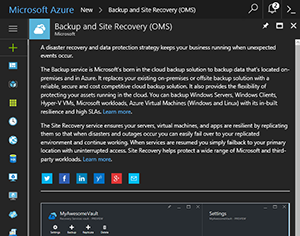
Many businesses, large and small alike, start with backup and disaster recovery (DR) for their current on-premises infrastructure. If you only have a handful of (Windows) servers, look at Azure Backup (bit.ly/2wR4S05), also known as the MARS agent (see Figure 1). This essentially replaces Windows Server Backup with a tool that backs up your data to Azure, up to three times a day. A recent addition is the ability to protect System State on the server.
 [Click on image for larger view.]
Figure 1. Azure Backup and Site Recovery.
[Click on image for larger view.]
Figure 1. Azure Backup and Site Recovery.
For larger deployments and Linux servers, look at Microsoft Azure Backup Server (MABS). This is a "pay-per-protected instance" version of System Center Data Protection Manager (DPM) 2016. You set this up on-premises, and it allows backup of supported workloads (Windows, Linux, SQL Server, Exchange, SharePoint, Hyper-V), first to on-premises disk for quick restores, then to the cloud.
If you use System Center, DPM can also use Azure to store backups. That's really the point of any cloud backup: moving away from the slow, error-prone and labor-intensive legacy tape solutions still common in enterprises. Public cloud storage is cheap, off-premises and more reliable than tape.
In the options described here, data is encrypted in flight and in the cloud; only you have the key to decrypt it. You can pick Locally Redundant Storage (LRS), which gives you three copies of your data in a single datacenter, or Geo Redundant Storage (GRS), which provides three extra copies in a different region. Each protected instance can have up to 9,999 recovery points; this means if you do one each day, you can keep your backups for about 27 years.
If, on the other hand, you're looking to eliminate that second site with servers and racks that you have on standby only for business continuity DR (BCDR), you should look at Azure Site Recovery (ASR), bit.ly/2vETUMD. This works for physical servers, as well as VMware or Hyper-V virtual machines (VMs), and continuously replicates these to Azure. Only virtual disks are stored in Azure, so you're only paying for the storage up until the point where you do a test (or real) failover and spin up servers in Azure, at which point you'll be paying normal Infrastructure-as-a-Service (IaaS) VM costs.
The first 31 days of ASR is free on a per-protected-server basis. (Tip: If your goal isn't to keep the server running on-premises, but instead use ASR as a migration tool, the ASR portion won't cost you a cent as long as you can move each server within a month.) Recently, the ability to use ASR to protect workloads already running in Azure IaaS from one region to another was added.
Compute
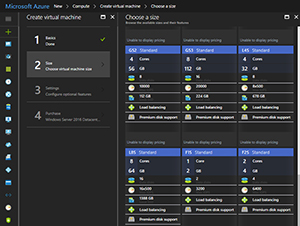
Whether you've migrated VMs from on-premises in a lift-and-shift approach or you're implementing new VMs in the cloud, using Linux or Windows VMs on demand is a great place to start. VMs in Azure come in many sizes and flavors, as shown in Figure 2, so it's important to pick the right size for each workload, because you're paying per minute; prices range from $14 per month to $6,685 per month (if they run 24 hours a day).
 [Click on image for larger view.]
Figure 2. Picking Microsoft Azure virtual machine sizes.
[Click on image for larger view.]
Figure 2. Picking Microsoft Azure virtual machine sizes.
There are general-purpose VMs (A and D series) with SSD-based storage (denoted by an S in the size; "DSv3 series," for example). For CPU-intensive workloads, look at the F series; for VMs with direct access to high-performance GPUs for rendering or deep learning, use the N series. For memory-optimized VMs look at the E, M, D and G series, going all the way up to 2048GB of VM memory. For VMs requiring large and fast storage, look at the L series. Recently Azure introduced a 99.9 percent service-level agreement (SLA) for a single-instance VM to complement the existing 99.95 percent SLA for two or more VMs in the same Availability Set.
Early in 2017, the addition of Managed Disks negated the need to manage storage for groups of VMs; built-in managed backup of your Linux or Windows VMs was also released. Groups of VMs are put into Virtual Networks (VNets), which are in turn divided into subnets. You can connect individual computers to Virtual Networks in Azure using Point to Site (P2S) VPN connectivity, or route entire on-premises sites to Azure using Site to Site (S2S) VPNs. If you require a faster private connection from on-premises with an SLA, look at ExpressRoute, bit.ly/2wqS83m. Recently added is the ability to link VNets from the same or different regions together using VNet peering. For VMs that should be reachable from the Internet, you can use a static IP address.
Please know that you're still responsible for the VM; you'll need to patch the OS inside the VM, keep it secure and protect it with anti-malware. You can also defend the VMs in the VNet using either Network Security Groups (NSG), which is a built in firewall, or using third-party network virtual appliances. If you have the business or regulatory requirement, you can also encrypt the VM as it's running using disk encryption; the back-end storage can also be encrypted using Storage Service Encryption.
Keeping an eye on costs is vital with IaaS (and the cloud in general). Here are a few tips:
Comparing region pricing can be a good strategy, as prices often vary for the same VM size.
Unless your VM is used 24x7, make sure to stop and deallocate it when it's not needed; use the auto-shutdown feature to schedule this.
Monitor your VMs; if they're using less memory or CPU than you've allocated, resize the VM to a smaller size (which requires a restart).
If you have licensing sorted on-premises, you can bring your own license to Azure through the Hybrid Use Benefit (HUB), saving up to 40 percent for Windows and SQL VMs.
If you need a file share for several VMs to access, use Azure Files instead of a VM; it'll be cheaper and easier.
Be ruthless in reviewing your deployed fleet every month or so. On-premises, you can have orphaned VMs that won't cost you anything extra; in the cloud, you pay for every minute, whether the VM is doing anything or not.
Cloud on Steroids
Running VMs in the cloud is all well and good, but it doesn't really transform the way you do IT; it just moves the hosts elsewhere. For new services, you should definitely look at writing your code for Platform as a Service (PaaS) or even Azure Functions. This gets you off the hook for managing most of the infrastructure.
Because there are so many options here, make sure you research the right tool for the particular app you need. If you're looking for small, stateless apps that are event-driven, look at Azure Functions (bit.ly/2whpelw); for app workflows, Logic Apps (bit.ly/2whLxYm) is the right tool.
App Service (bit.ly/2vXotvq) is an umbrella that covers Web apps, mobile apps and API Apps. You can now have this in extra-secure, isolated instances through App Service Isolated. If your application is bigger, you can use Azure Container Service (ACS) to host Kubernetes, or DC/OS- or Docker Swarm-dedicated clusters.
Another option for container and microservices-based applications is Azure Service Fabric (bit.ly/2vXtLqZ), the underlying orchestrator for the whole of Azure. Azure Container Instances (bit.ly/2vXdBO2) is new, and provides the ability to use both Windows and Linux containers directly, without having to manage any infrastructure. These build on the new Hyper-V containers in Windows Server 2016, along with the recent support for Linux containers on Hyper-V.
You can have custom domain names for your apps, track the usage of your mobile apps with Mobile Engagement (bit.ly/2fZglqm), and protect your Apps with SSL certificates.
If you're into 3-D modeling, a new service (currently in preview) lets you send Blender, 3ds Max and Maya rendering jobs to Azure for processing through Batch (bit.ly/2ijrJhD). At Build 2017, Microsoft announced low-priority VMs for Batch. These are extra-low-cost VMs using spare capacity in a region, suitable when your distributed computing job (or rendering) isn't time-critical, because these VMs might not be available or may be taken away if higher-priority workloads require the capacity.
Azure Automation (bit.ly/2weYlz0) lets you run PowerShell-based workflows on your resources in the cloud, as well as on-premises, through an agent for a single service to automate all of your hybrid cloud.
Security
Security is high on most CIOs lists of concerns, and it's becoming clear that most businesses are in fact more secure when they host workloads in the cloud, if they configure them correctly.
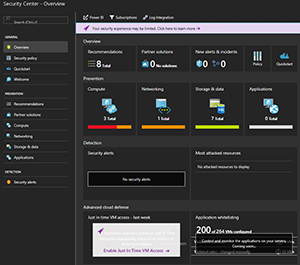
Azure Security Center (bit.ly/2fPvxpT) will help you with both your IaaS and PaaS workloads, letting you set security policies and see the security state of your deployed resources, as well as receive alerts and recommendations for improvements. ASC (Figure 3) also integrates with Microsoft's own back-end security graphs, so when they find an IP address that's generating malicious traffic, you'll be protected.
 [Click on image for larger view.]
Figure 3. Azure Security Center.
[Click on image for larger view.]
Figure 3. Azure Security Center. As your infrastructure in the cloud grows, protecting secrets such as keys and certificates becomes very important, and Azure Key Vault (bit.ly/2wY97XH) will help you here. It can optionally be backed by Hardware Security Modules (HSMs) that are FIPS 140-2 Level 2 compliant.
If your business needs certifications to be able to move workloads to the cloud, it's good to know that Azure leads the pack for ISO and CSA certifications. Protecting your business documents is of course paramount, and Azure Information Protection (bit.ly/2whC83w) can help, encrypting documents and ensuring through templates that only the right people have access to them.
Data
"Data is the new oil" is a saying often attributed to Clive Humby, a U.K. mathematician who says that analyzing data to gain insight is like turning raw oil into useful substances. For most businesses, the prospect of building the necessary infrastructure to ingest, process, analyze and gain insight from large amounts of data is simply too hard.
Azure has several services to help you get up and running, starting with foundational storage technologies such as blobs, files, tables and queues.
For larger data sets there's Azure Data Lake, which includes a Store and Analytics (bit.ly/2vKVWL2). It lets you store petabytes of data, and use R (bit.ly/2fRR0Pc), Python and .NET to transform and process the data, with no infrastructure to manage. You can also use the in-house developed language U-SQL (bit.ly/2vLbj6l), which, as the name suggests, makes it easy for SQL developers to move to Big Data analysis. If, on the other hand, you're used to Hadoop and want full control, you can use HDInsight, which gives you a managed cluster where you can run Spark, Hive, Map Reduce, HBase, Storm, Kafka and R-Server.
If you're looking to deploy Internet of Things (IoT) devices and gather and process data from them, use IoT Suite on the Azure side to store, process and visualize the data, while IoT Hub sets up the secure communication between devices and Azure.
Identity
Many businesses have realized that in this cloud-filled world, identity is the new firewall. Headline breaches are almost always precipitated by a stolen identity. Azure Active Directory (Azure AD) is the cloud-based directory that underlies access to all Azure resources, as well as Office 365. You can link your on-premises Active Directory to Azure AD using Azure AD Connect (bit.ly/2vKOYWq), which will synchronize changes from on-premises to the cloud (and a select few back down if you want).
Apart from allowing you to control access to Azure resources in a granular fashion, you can also use Azure AD as a directory for your own Web and mobile apps through Azure B2C (bit.ly/2vPTQYV), which handles signup and sign-in. On the other hand, Azure B2B (bit.ly/2whugiF) is making it easier to collaborate between organizations without having to futz about with old-style federation relationships.
If you're deploying VMs in Azure that require access to your on-premises AD forest, you can either deploy a VM that's a Domain Controller or use the managed Azure AD Domain Services (bit.ly/2wYxT9Z) for Kerberos authentication. To protect your user's identities, use Azure Multi-Factor Authentication, aka Azure MFA (bit.ly/2uZbkRe).
ARM
The early days of Azure used a service-based model where resources that made up a deployment were inextricably linked, but this has been replaced over the last few years by Azure Resource Manager (ARM). ARM allows you to treat your infrastructure as code and set up JSON-based templates for all deployments, making them more predictable, repeatable and automatable (bit.ly/2xbVnI1). Enterprises can use ARM policies to put guard rails around what, when and in which region particular users (*cough* developers *cough*) can and can't deploy resources (bit.ly/2wYuZlE). Recently, more aliases were added to these policies, making them more flexible (bit.ly/2wYiSoI).
Looking Ahead
Predicting the future in IT is fraught with danger (remember when Steve Ballmer said, "The iPhone has no chance of gaining a significant market share"?). Nevertheless, with Ignite coming up and Azure announcements sure to dominate the conference, I offer my predictions (not based on any pre-release or inside information from Microsoft):
- There will be more links between the technologies Microsoft uses under the hood to protect Azure (and Office 365, Xbox, Hotmail and so on) and services that customers can use to protect their networks, both in the cloud and on-premises.
- Protection against DDoS attacks is already built into Azure, but I predict Microsoft will make this a more visible part of Security Center.
- The one area where AWS and the GCP both have offerings is in reserved instances of IaaS VMs; this means that if you pay up front for a certain capacity, you get a discount. I would hazard a guess that Microsoft will follow suit at some stage and offer this, as well.
If you're an IT pro on the fence about the cloud, it's time to start immersing yourself in Azure (consider a free trial), because the future of IT is definitely cloudy.