How-To
Securing Remote Work Setups in the Age of COVID-19
Assuming that many VCRM readers are finding themselves responsible for managing the IT infrastructure of remote staff as well as their own setups, Paul Schackenburg shares some practical steps to improve the security of this "new normal," based on his experience in helping clients transition to remote work.
Last month I provided some tips based on my long experience in working from home, since then the U.S. and many other parts of the world have been feeling the effects of COVID-19 a lot stronger.
This article will give you some practical steps you can take to improve the security of this "new normal," based on my experience in helping my clients transition to working from home. I'm assuming many readers are in the situation of managing the IT infrastructure of working from home staff as well as themselves working from home.
Back to Basics
Communication is key for managing everyone's expectations. Make sure the IT team sends out emails, Teams or Slack announcements, holds video conferences or uses other ways of letting everyone know where the IT systems are at. As I stated in last month's column, IT is definitely at the center of keeping businesses working during this pandemic and this is the time to show everyone that technology is the foundation for keeping businesses running. Then you need to remind everyone that the bad guys are using this situation to attack businesses of all sizes.
Communication goes the other way too; make sure your users have easy ways to communicate back to you about security issues as well as be able to forward suspicious emails.
Because many new and different procedures have been implemented in a hurry there's a greater risk that cleverly worded phishing emails will be opened or that Business Email Compromise (BEC) will succeed. BEC is where attackers have managed to get a foothold in your organization, perhaps into someone's email system. By watching normal email traffic they can set up a tailored email, for instance from the CEO to the CFO asking for money to be wired somewhere to close a deal. Or bank account details for a supplier can be changed (to the attacker's details). These types of attacks are much more likely to succeed in the current situation and your best protection is user awareness through security training.
If your users are connecting from personal computers (or work computers that you now can't easily manage) make sure users update their browser to the latest version (and don't use Internet Explorer). While you're at it make sure they update Windows, other application software and do the same on their phone. Yes, this is a big ask for non-technical users, but you simply can't allow the lack of physical presence to result in out-of-date software.
Since it's likely that other family members (including curious teenagers) will be around, teach your users to use the Windows Key + L to lock their screens when they leave their PC for a break, and use a PIN for their smartphones/tablets.
If your users are storing business data on their local PCs (as they process it) make sure you disseminate instructions (as well as external hard drives or cloud backup accounts) on how to back up this data and their systems.
Connectivity
Many businesses still use VPN technology for Work from Home (WFH) scenarios, particularly where a lot of company data still exists on-premises. But these VPN systems may have had to be scaled up from a small subset of staff that access them regularly to a much larger group of people. Make sure you pay particular attention to logging and reviewing this access as this could be a vector for attack.
On the other hand, if your organization is well on its way towards the cloud, many of your business applications and data lives in the cloud. But the access patterns for these will have changed with most people now accessing these from their homes rather than the office or the road. If you haven't considered using a Cloud Access Security Broker, now would be a good time to implement one. (I am aware that minimizing change is another imperative during these times but a security breach due to lack of awareness of what's going on with your SaaS systems and data will lead to "a lot of change" in very short order).
One CASB that's quite easy to get started with is Microsoft Cloud App Security (MCAS) that's part of Microsoft 365 licensing. Not only will it give you insight into the cloud app usage of your users, it has a catalog of over 16,000 cloud services with a rating of what they offer as far as security, privacy, regulations etc. This will help you deal with Shadow IT and also block SaaS applications that are putting your business at risk. MCAS will also help you apply policies for data classification of files and can block risky sessions. The big strength of MCAS over other CASBs on the market is the integration with Office 365 and other security solutions in Microsoft's portfolio.
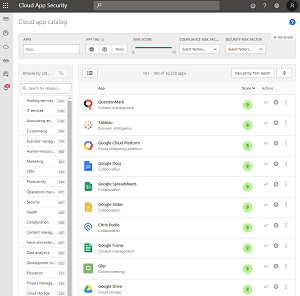 [Click on image for larger view.] Cloud App Security SaaS Catalog
[Click on image for larger view.] Cloud App Security SaaS Catalog
If you don't have a SIEM in place consider implementing one. The main challenge with security (such as the VPN attack vector mentioned above) is that if you don't have centralized monitoring and log aggregation you don't have visibility, effectively blindfolding your defenders. I have found Azure Sentinel quite easy to get started with and it provides monitoring of Office 365 with a single click. AWS CloudTrail log monitoring is also easy to set up in Sentinel and is free until the end of June 2020. Because Sentinel is cloud based it's quite quick to get up and running and the pricing is competitive with other solutions on the market. It's also got a strong community providing different plug-ins and playbooks to enhance Sentinel.
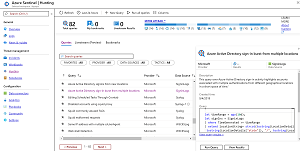 [Click on image for larger view.] Azure Sentinel Workspace
[Click on image for larger view.] Azure Sentinel Workspace
Make sure you have means to access user's PCs at home for helpdesk scenarios or to assess security issues they may bring to your attention. If you don't have anything in place, Windows 10 has a built-in feature called Quick Assist that lets you connect and see their screen.
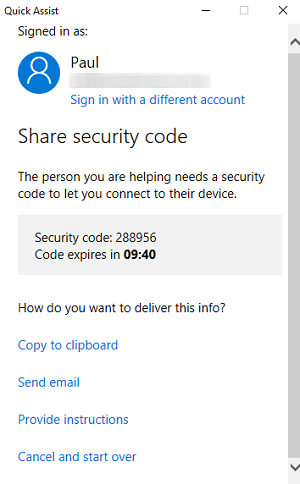 [Click on image for larger view.] Quick Assist in Action
[Click on image for larger view.] Quick Assist in Action
There's also the built-in Steps Recorder where a user can step through an issue they have and send you a recording of the steps in a ZIP file.
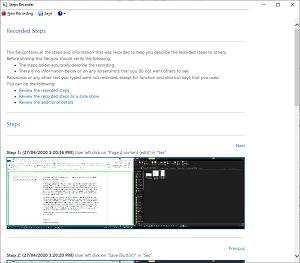 [Click on image for larger view.] Windows Steps Recorder in Action
[Click on image for larger view.] Windows Steps Recorder in Action
Identity Is the New Firewall
Purchase a company license of 1Password, Lastpass or another password manager and make sure everyone installs it and knows how to use it. The need to manage passwords is even more critical currently and reusing the same, easy-to-remember password across sites is an invitation to be "pwned." Having a password manager generate random passwords for each different site ensures that a compromise in one doesn't spread, as well as making it very hard to phish (if I don't know the password because my password manager enters it for me I'm unlikely to hand it over to someone based on an email). A good site to use to educate users about data breaches and the risk of reusing passwords is Have I been Pwned.
Azure AD Password Protection can nudge your users (including those whose account reside in AD on premises) to pick better passwords. If your organization has some of the dearer SKUs of Office/Microsoft 365 consider using the attack simulator, it can be used to run password spray or brute force attacks against your users' passwords, as well as send simulated phishing emails to help educate users about the risks.
Even better is to eliminate passwords as the weakest link by enabling Multi Factor Authentication (MFA), sometimes called Two Factor Authentication (2FA). This means that in addition to having the username and password you also need a device (normally a smartphone but it can also be USB key or similar device) to login to a service. MFA is free in Office 365 for instance (with very little adoption unfortunately) and I've had good success with my security-conscious clients with Duo Security. One particular deployment has a Remote Desktop host running in Azure with users accessing it all day, for their work and I sleep like a baby at night because I know there's no way to get in to that server apart from acknowledging a prompt on a smartphone.
The endgame is of course to get rid of passwords altogether but that's probably not feasible in the current situation.
If your users took their work PCs home, there might be some worry about domain joined computer account passwords if they're not connected back to the corporate network using a VPN and thus can't access Domain Controllers. This recent article should lay to rest most such fears -- the short version is that the client PC password check will "wake up" after the default of 42 days, but if it realizes that it can't access a DC it'll go to sleep until it can.
Conclusion
I hope some of those tips are useful for you and as we all continue to battle through this pandemic I trust you, your loved ones and your business users stay safe both in the physical world and the digital world.