How-To
Deep Dive: What's New in Hyper-V, Part 1
There's lots to like in the new Windows Server 2012, and even more if you look at just the Hyper-V against the competition. Let's start with extensible switch and virtual switch functionality.
Windows Server 2012 brings so many changes to so many areas that it'll take months before we see how it all plays out in the marketplace. One thing is clear, however, with the new Hyper-V: Microsoft is taking on the competition head on. No longer content with being "good enough", they have leapfrogged VMware in several areas.
In this series of articles, we'll look at new and improved features in Hyper-V in Windows Server 2012. First, we'll cover the new extensible switch and enhancements to virtual switch functionality, then we'll look at network virtualization, which is Microsoft's take on software-defined networking.
Later on in the series, because the new Hyper-V offers several new options in datacenter design, we'll look at the new Quality of Service options for networks and how resource metering ties in with this. And we'll also look at the new hardware features in modern NICs and how Hyper-V lights up these in various scenarios. We'll also cover the features that have garnered most headlines -- the massive improvements in scale across all of Hyper-V -- later on, followed by a look at security, Bitlocker and the new Hyper-V replica functionality. This series will also cover improvements in storage, new features in Live Migration, and a comparison of Hyper-V and VSphere 5.1 from a technical standpoint, as well as philosophical approach, to virtualization.
Extending the Envelope
The virtual switch in Hyper-V in Server 2008 R2 did the job, but it was pretty basic and management of it didn't scale easily in large environments. So, in 2012 Microsoft didn't just push the envelope, they extended it. The new switch takes into account private cloud necessities such as tenant isolation, traffic shaping, protection against malicious virtual machines, and easier troubleshooting, as well as centralized configuration.
There are two APIs for third-party developers to use in "talking to" the extensible switch: NDIS 6.0 filter drivers and Windows Filtering Platform callout drivers. The benefit for developers is that these APIs are already familiar if they're making drivers, firewalls or network capture tools for Windows. There are several different types of extensions:
- Capture extensions, also known as Network Packet Inspection extensions (NDIS), which can be used to view network packets on a particular link or port without altering the data. This type of extension can see packets as they first enter the switch, as well as when they leave the switch, and thus identify alterations other extensions may have performed during the data transfer. An example of this type of extension is sFlow by Inmon. The free sFlow Trend can be used to display the data.
- Network packet filter extensions (NDIS) can create, modify and filter packets going through the switch for security reasons. An example of this type of extension is Security Manager from 5Nine, currently the only extension listed on the official Windows Server Catalog as certified for Windows Server 2012. It comes in three different flavors, and is essentially an agentless firewall, anti-virus and anti-malware, as well as IDS, for your virtualized environment.
- Network Forwarding extensions (NDIS) can be used to alter the default forwarding behavior of the switch and there can only be one of these installed on a vSwitch. Examples include OpenFlow support through UNIVERGE PF1000 (PF stands for Programmable Flow) by NEC and the Cisco Nexus 1000v switch. Cisco also brings support for its Virtual Machine Fabric Extender (VM-FEX) to Hyper-V, with SR-IOV. If you're running the Cisco switch, be aware that there are some features that can be configured in both the native switch and the 1000v. In most cases use the 1000v; more information can be found here.
- Intrusion Detection or Firewall extensions (WFP) has similarities with the Network packet filter extensions and some extensions may use both APIs.
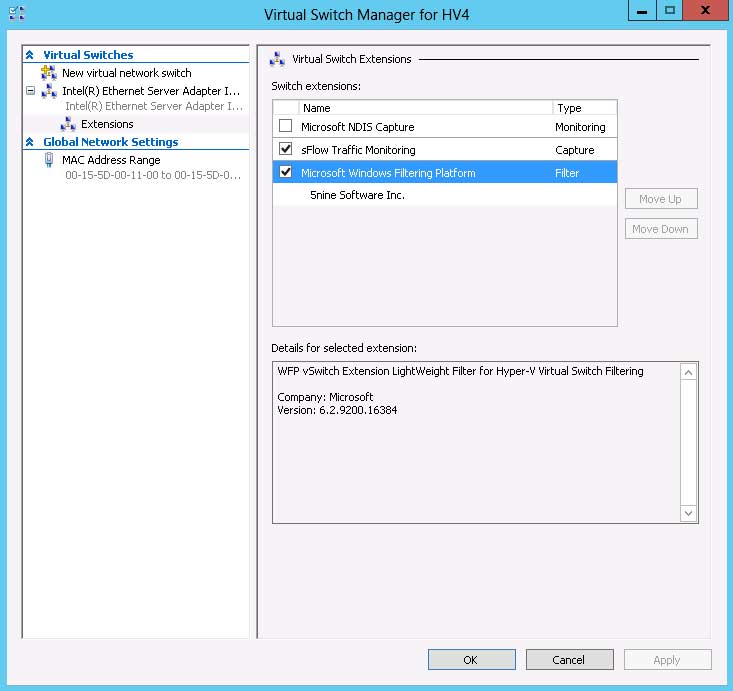 |
Figure 1. Here, both the Inmon Sflow free extension, along with the firewall and antimalware extension from 5Nine, are installed in a switch. (Click image to view larger version.) |
vSwitch Enhancements
As with almost every other part of Windows Server 2012, the virtual switch can now be controlled using PowerShell, with nouns such as VMSwitch, VMNetworkAdapter, and VMNetworkAdapterVlan. For a complete list of cmdlets for Hyper-V look here.
In Windows Server 2008 R2 the switch was limited to a single virtual NIC and so you might end up with many switches needing configuration and management. Now a single vSwitch can be associated with several virtual NICs; the physical NIC can also be shared with the management OS. This makes it easier for instance to carve out portions of a 10 Gb Ethernet link for Live Migration, Storage and management traffic.
Also new is that you can set port ACLs, defined by local or remote addresses in IPv4, IPv6 or MAC address format, to control traffic in and out of VMs. You can also use port ACLs to meter traffic to or from a VM and going to a specified address range.
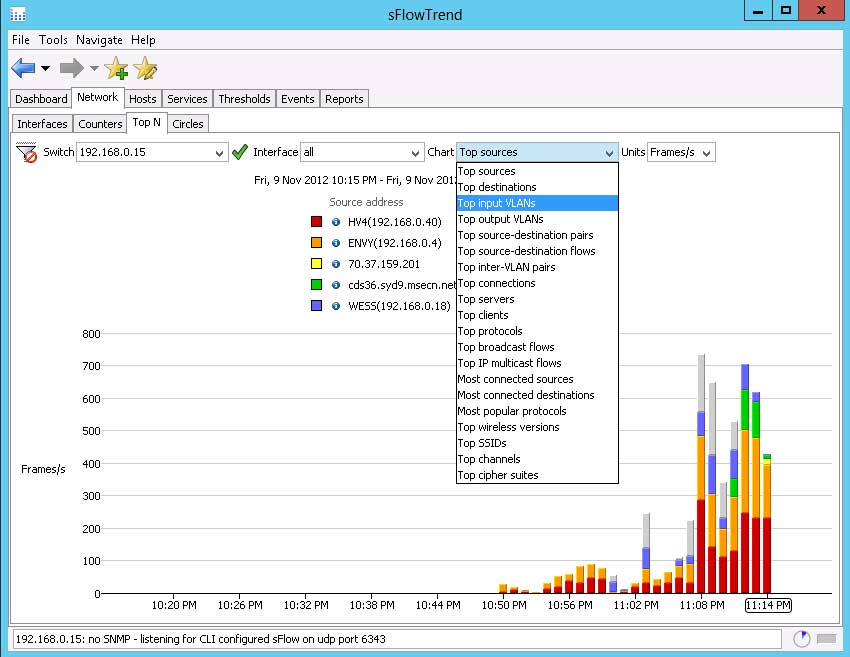 |
Figure 2. The Inmon Sflow monitoring extension and the free SflowTrend console provide very detailed traffic information. (Click image to view larger version.) |
For security reasons, you can now control whether a VM is allowed to spoof its MAC address for outgoing traffic; to stop VMs acting on router advertisements and redirection messages you can enable Router Guard. There's also DHCP Guard that stops DHCP server packets coming from VM unless you've authorized the VM as a DHCP server.
Because of the high CPU overhead of IPsec calculations, this valuable security tool is often never considered in most VM deployments. Hyper-V now makes it possible to use IPsecTO (IPsec Task Offload), where a VM lets the physical NIC in the host manage the calculations. Be aware that this is only supported where the VMs run either Windows Server 2008 R2 or 2012, and the NIC, of course, must support IPsecTO.
In environments where VM isolation is needed and each VM can be isolated from all other VMs, you can use PVLAN (Port Virtual Local Area Network) as long as the physical switches are properly configured with VLAN IDs. The Hyper-V switch also supports VLAN trunk mode, where a VM can "see" traffic from supplied list of VLAN IDs.
Finally, a port can be configured for port monitoring, so commonly used traffic analyzers like Wireshark and Network Monitor or Intrusion Detection Systems can be used to analyze traffic.
That's it for now. Next time, we look at Hyper-V's take on network virtualization.
About the Author
Paul Schnackenburg has been working in IT for nearly 30 years and has been teaching for over 20 years. He runs Expert IT Solutions, an IT consultancy in Australia. Paul focuses on cloud technologies such as Azure and Microsoft 365 and how to secure IT, whether in the cloud or on-premises. He's a frequent speaker at conferences and writes for several sites, including virtualizationreview.com. Find him at @paulschnack on Twitter or on his blog at TellITasITis.com.au.