XenServer Remote Management with Xsconsole
Administering a virtualized infrastructure is a tactful dance of tools that allow you to get what you need done in a quick and efficient manner. For Citrix XenServer, one way to do that is with the xsconsole interface. The XenCenter client is great for most day-to-day tasks, and xsconsole can be used to configure the hypervisor from a console to the server.
Xsconsole should be familiar to XenServer administrators; it runs on the true server console (see Fig. 1).
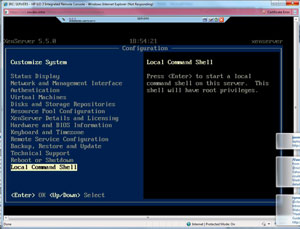 |
| Figure 1. The XenServer host runs a xsconsole on the server. (Click image to view larger
version.) |
For remote administration, xsconsole can be accessed through SSH. SSH is enabled for root login by default for XenServer, and once you are in an SSH session, simply type "xsconsole". Within the SSH-based instance of xsconsole (see Fig. 2), the familiar menu appears that allows server-based administration outside of XenCenter.
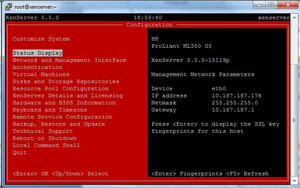 |
| Figure 2. Xconsole can be accessed through SSH. (Click image to view larger
version.) |
Though most implementations would want to have xsconsole running, it can be disabled from automatic startup should you prefer to access it only via an SSH console or interactive console login. You might want to do this to save a trivial amount of server resources, and you can obtain access via SSH or direct console. The following edit is made to the /opt/xenso?urce/libexec?/run-boot-xs?console file by disabling (as indicated by the # sign) the default entry and adding a limited entry in a new line:
#!/bin/bash
TTY=$1
#exec /sbin/mingetty --noissue --autologin root --loginprog=/usr/bin/xsconsole $TTY
exec /sbin/mingetty --noissue --noclear $TTY
With this configuration, the XenServer host will boot up to a simple login screen. This is an unsupported configuration, so use at your own risk: From a security perspective, xsconsole doesn't allow an unauthenticated user to modify environment parameters if they were at the console. But it does display potentially privileged information such as IP addresses and the virtual machine inventory.
Posted by Rick Vanover on 08/05/2009 at 12:47 PM