CTOpinion
Security Rewind: The '90s Called -- They Want their DMZ Back
Is your security still living in the dark ages?
The 1990s brought us the mainstream Internet, grunge rock, and even Happy Gilmore. Like Queensryche, firewalls promised to be "watching over you," and demilitarized zone (DMZ) networks were as common as people walking streets humming "Silent Lucidity" while listening to their Discman.
The point is that some things from the 90s are timeless. Dropping Happy Gilmore quotes such as "Just tap it in" during a game of pool or round of golf never gets old. DMZs, on the other hand, need to find their place in history alongside the Furby.
Traditional DMZs and network firewalls once served a critical purpose, but those approaches have struggled to keep pace with today's security threat landscape that traverses clouds, datacenters and a variety of endpoint devices. In addition, firewall rule complexity (and sprawl?) has taken on a life of its own. For example, when meeting with the CTOs of many large enterprises, I often hear something like this:
"We have many firewall rules that exist that we have no idea what they do. We are afraid to delete them because we don't know what they might break!"
If that's not bad enough, the average large enterprise takes anywhere from two weeks to two months to provision network and security services for new applications. That alone is a key reason that many private clouds have not been able to meet the agility demands of consumers of IT services (like their public cloud peers?).
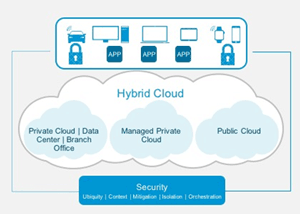
As shown in Figure 1, the world that we must protect and secure is multi-cloud, multi-device, and highly fluid and dynamic. As a result, static network and security solutions that were ideal two decades ago simply aren't practical today.
 [Click on image for larger view.]
Figure 1. Your security infrastructure has to do a lot more these days. (Courtesy Chris Wolf).
[Click on image for larger view.]
Figure 1. Your security infrastructure has to do a lot more these days. (Courtesy Chris Wolf).
VMware
Applications and content are hosted nearly anywhere. To meet today's demands, modern security frameworks must be centered around five key attributes:
- Ubiquity. Security controls must be everywhere.
- Context. All security products have visibility into applications and content via open integration frameworks.
- Mitigation. Threats are mitigated via coordination across a variety of security solutions.
- Isolation. Controls are protected.
- Orchestration. Controls and state definition are automated across multiple clouds and consumption devices.
These attributes can only work across multiple clouds when those services are virtualized and exposed via software controls. Otherwise you're left cobbling together the same ‘ol static physical models that have proven to be ineffective today.
Network virtualization has rapidly matured and can give you significant immediate benefits, including:
- Automated network and security provisioning, reducing provisioning cycles to minutes
- Security based on the name of an application container as opposed to being based on an IP address, allowing security policies to remain consistent even if the network context changes (across clouds, data centers, or branch offices, for example).
- Micro-segmentation. This is the ability to effectively create per-application DMZs (every app can have a dedicated external stateful firewall).
- Enforcing least privilege. This means only giving applications access to exclusively what's needed.
- End-to-end encryption for data in motion and at rest, from a mobile application to a server application, with the capability to integrate with all of your preferred security solutions.
- Consistent network configurations that require no modifications even as workloads traverse clouds or datacenters.
Naturally, you may never be able to wholesale replace your entire legacy infrastructure, and I would never try to convince you that's even something you should consider. A variety of top security vendors provide excellent solutions to help bridge the old and the new.
Many industry vendors are spending considerable time on machine learning to mitigate potential threats using a variety of pattern recognition algorithms. Other end-user organizations are even using traditional server virtualization and containers as the baseline for rethinking their approach to application state entirely. For example, I recently worked with an organization that leverages virtualization to keep an application instance alive for the duration of a single transaction. Their reasoning for the architecture is that even if the application container is compromised, the compromised container is destroyed within a matter of seconds.
That has caused the IT team to rethink everything from logging and audit to change management and more. This isn't some lab project, either; the solution is processing millions of transactions a day. The bottom line is that when you lead with software-based solutions, practically anything is possible.
The Security Times, They Are A-Changin'If you're like many readers of this magazine, you've already flexed your virtualization muscles across both compute and storage. Today's agility demands and ever-complex threat landscape should give you more than enough motivation to turn your attention to network virtualization and security.
Pure software-defined networking (SDN) and virtualized security solutions are software-based, allowing you to get them in your lab and begin learning with often a very small investment. You can get a quick agility win for the lab and software developers, while also learning to operate in a new network and security model. Then look to pick one production app to pilot. Once you complete the first successful production pilot, you'll find that you have momentum to modernize the network and security models of new greenfield applications and begin to modernize existing brownfield apps and services.
It's 2016 and we need security for the times, not fanny packs. The road to modernizing decades-old security models won't be easy, and to some the new song will sound more like a bittersweet symphony. However, you can't wait another decade for a perfect solution and hit a switch. You oughta know.
(Visit the VMware Corporate Blog, Radius, for more viewpoints on "Software-Defined Shifts: Networking and Security.")
About the Author
Chris Wolf is VMware's CTO, Global Field and Industry.