News
Researchers Reveal SDN Security Vulnerability, Propose Solution
Three Italian researchers have published a paper highlighting a security vulnerability in software-defined networking (SDN) that isn't intrinsic to legacy networks. It's not a showstopper, though, and they propose a solution to protect against it.
"It" is a new attack they call Know Your Enemy (KYE), through which the bad guys could potentially collect information about a network, such as security tool configuration data that could, for example, reveal attack detection thresholds for network security scanning tools. Or the collected information could be more general in nature, such as quality-of-service or network virtualization policies.
"While the programmability of SDN allows for fast prototyping and high adaptability to different scenarios, it also opens new venues for attacks," says the paper, titled Know Your Enemy: Stealth Configuration-Information Gathering in SDN. Published last week, it was authored by Mauro Conti, University of Padova, Fabio De Gaspari and Luigi V. Mancini, both at Sapienza University.
"Indeed, while the decision-making process is centralized in the control plane, the enforcement of the decision is distributed throughout all switches, which follow the rules pushed by the control plane," the paper continues. "We show that, by exploiting this distributed policy-enforcement mechanism, an attacker can gather intelligence about the control logic of the network in a stealthy fashion."
For a successful KYE attack, the paper says, the instigator needs only to learn which rules are installed for a single switch, revealed in what's called a flow table side-channel.
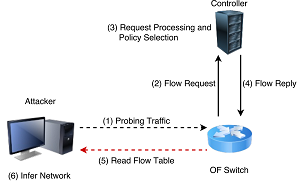 [Click on image for larger view.] The KYE Attack (source: Know Your Enemy:
Stealth Configuration-Information Gathering in SDN)
[Click on image for larger view.] The KYE Attack (source: Know Your Enemy:
Stealth Configuration-Information Gathering in SDN)
"By analyzing the conditions under which a rule is pushed, and the type of such rule, an attacker can infer sensitive information regarding the configuration of the network," the paper says. "The final result is that through a single switch, the attacker can gather information which, in a classical network, would have required access to numerous distinct devices, such as firewalls, intrusion detection/prevention systems, etc. The information gathered can subsequently be exploited to mount different attacks, tailored to the target network, without being detected."
The researchers said the comprehensive details of how an attacker could obtain side-channel flow table data of a switch were beyond the scope of their research, but noted several possibilities, including connecting to a passive listening port on an entry switch, sniffing control traffic, exploiting an OS back door and physically reading a flow table with the use of a physical device.
To combat the KYE threat, the researchers propose a countermeasure they called "flow obfuscation," which takes advantage of one of the primary benefits of SDN, programmability, a key tenet of the SDN approach that opens up the attack vector in the first place.
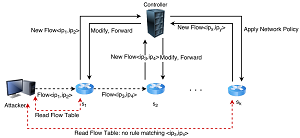 [Click on image for larger view.] The KYE Attack Countermeasure (source: Know Your Enemy:
Stealth Configuration-Information Gathering in SDN)
[Click on image for larger view.] The KYE Attack Countermeasure (source: Know Your Enemy:
Stealth Configuration-Information Gathering in SDN)
"The goal of this countermeasure is to prevent the attacker from learning which network flow causes the installation of a given flow rule; indeed, since the attacker can control up to n switches, when k > n he will never be able to obtain the complete knowledge required for a successful KYE attack," the paper says.
In their 13-page report, the researchers note certain limitations of the KYE attack, which they said could be automated through the use of machine learning techniques. They also acknowledged some drawbacks associated with their flow obfuscation countermeasure, but maintained "Our solution offers provable security guarantees that can be tailored to the needs of the specific network under consideration."
They also indicated their research paper breaks new ground.
"SDN has become a popular research topic in recent years, especially in relation to security," the paper says. "Despite significant research efforts, to the best of our knowledge this is the first work to analyze the vulnerabilities caused by the distributed enforcement of rules in SDN."
About the Author
David Ramel is an editor and writer at Converge 360.