News
AWS Offering Highlights Software Defined Perimeter Space
After an uneven start, the software-defined networking (SDN) movement has matured and evolved to include fast-growing initiatives such as software-defined wide-area-networking (SD-WAN) and the security-oriented Software Defined Perimeter (SDP).
As an example, Israeli security firm Safe-T announced the Safe-T Software Defined Perimeter offering on the AWS Marketplace for users of the Amazon Web Services Inc. (AWS) cloud platform.
"More and more organizations are moving towards the cloud to cut costs and increase agility, selecting AWS Marketplace as their cloud infrastructure," said Safe-T exec Eitan Bremler. "With the introduction of our SDP solution on the AWS Marketplace, we can now reach and help more businesses to simply secure their cloud, data, and application access with easy and quick purchase subscriptions to Safe-T's SDP."
SDP has been around for a few years, as evidenced by our 2013 coverage of the Cloud Security Alliance (CSA) launching an initiative aiming to pave the way for organizations to use cloud computing services to protect their infrastructure.
At the time, we reported that a new working group called the Software Defined Perimeter (SDP) project represented a departure for the CSA, which was formed with the mission to improve cloud security. The SDP Working Group, we reported, sought to provide a standard way to use cloud services to protect their infrastructures in the age of bring-your-own-device (BYOD) and employees' own use of cloud services.
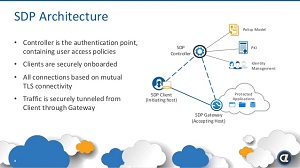 [Click on image for larger view.] SDP Architecture (source: Cryptzone).
[Click on image for larger view.] SDP Architecture (source: Cryptzone).
The movement gained traction, and by 2016 research firm Gartner Inc. issued a report titled "It's Time to Isolate Your Services From the Internet Cesspool."
In introducing that report, Gartner said: "Network designs that expose services and accept unsolicited connections present too much risk. Not meant for a complex and interconnected world, they're now obsolete. Security leaders can reduce risks using software-defined perimeters and other techniques that isolate applications from the Internet."
That same year, we covered the news that the CSA, a nonprofit organization promoting the use of cloud security best practices, announced the formation of a new SDP for Infrastructure as a Service (IaaS) initiative.
According to Wikipedia:
Connectivity in a Software Defined Perimeter is based on a need-to-know model, in which device posture and identity are verified before access to application infrastructure is granted. Application infrastructure is effectively "black" (a DoD term meaning the infrastructure cannot be detected), without visible DNS information or IP addresses. The inventors of these systems claim that a Software Defined Perimeter mitigates the most common network-based attacks, including: server scanning, denial of service, SQL injection, operating system and application vulnerability exploits, man-in-the-middle, cross-site scripting (XSS), cross-site request forgery (CSRF), pass-the-hash, pass-the-ticket, and other attacks by unauthorized users.
Security firm Perimeter 81 says "Implementing SDP allows organizations to restrict network access and provide customized, manageable and secure access to networked systems. Connectivity is based on the need-to-know-model, meaning each device and identity must be verified before being granted access to the network."
The company Cyxtera says an SDP is based on three core pillars:
- Identity-centric -- It's designed around the user identity, not the IP address.
- Zero Trust -- It leverages micro-segmentation to apply the principle of least privilege to the network. It completely reduces the attack surface.
- Built for the cloud -- It is engineered to operate natively in cloud networks and delivers scalable security.
For its part, new AWS SDP provider Safe-T says, in addition to obviating the need for VPN access, its SDP provides capabilities including:
- Firewall is constantly in a deny-all state, no open port (inbound or outbound) is required for access.
- Supports a variety of applications -- HTTP/S, SMTP, SFTP, SSH, APIs, RDH5, WebDAV.
- Bi-directional traffic is handled on outbound connections from the LAN to the outside world.
- Defines new reverse-access rules on-demand.
- Allows client-less access to data, services, networks and APIs.
- Robust partner authentication options.
- Performs SSL decryption in a secure zone.
- Scans all incoming traffic using the organization's security solutions.
- Hides DMZ components which can be hacked and utilized to access the network.
- Detects and reports on the presence of bots and malicious insiders for quick event resolution.
- Provides only direct application/service access, thereby blocking network access.
As the movement grows, expect more SDP offerings to show up on the AWS cloud and other cloud platforms such as Google Cloud Platform (GCP) and Microsoft Azure.
Because, as the Cloud Security Alliance says, "With the adoption of cloud services the threat of network attacks against application infrastructure increases since servers can not be protected with traditional perimeter defense techniques."
About the Author
David Ramel is an editor and writer at Converge 360.