How-To
Review: Azure Advanced Threat Protection and Advanced Threat Analytics
Paul Schnackenburg takes a look at Azure Advanced Threat Protection and its cousin, Advanced Threat Analytics, which protect against identity-based attacks in organizations that run on Active Directory Domain Services.
If your business runs on Active Directory Domain Services (AD DS) you need to make sure you're protected against identity-based attacks. And nothing does that better than Azure Advanced Threat Protection (AATP) or its cousin, Advanced Threat Analytics (ATA). In this article I'll look at both, how they work and what they can bring to the table to secure your business.
Meet the Family
ATA started out as an acquisition that Microsoft made back in 2014 of the company Aorato. ATA is an on-premises solution that you deploy and manage that keeps an eye on your Domain Controllers (DCs), their event logs and network traffic, spotting anomalies and known attacks. It builds profiles of how user accounts and devices behave over time and uses machine learning (ML) to alert on unusual behavior. The issue with ATA is that deployment and ongoing maintenance is somewhat onerous (who wants to set up and manage servers in today's cloudy world?) and updates only arrive every 3-6 months. If you have Microsoft 365 E3 licensing or EMS E3, ATA is part of the package.
AATP on the other hand is the next version of ATA and is a cloud service where you simply deploy agents on-premises and the server side is hosted by Microsoft in Azure and you use a web console to access your alerts. Updates arrive every two weeks. AATP is part of Microsoft 365 E5 licensing or EMS E5 licensing and is also available as a stand-alone license.
Both products excel at spotting and letting you know about attackers in your network as they do reconnaissance, elevate privileges and move laterally to attack your DCs to achieve the ultimate goal -- domain dominance.
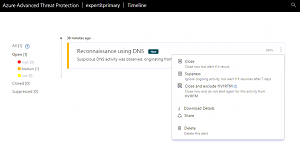 [Click on image for larger view.]
Figure 1. Suspicious Activity Notification
[Click on image for larger view.]
Figure 1. Suspicious Activity Notification
Kill Chain and Attack Vectors
The way hackers attack businesses today is often described as a kill-chain. If you speak to security professionals, they aren't fond of this metaphor as it's a bit too sequential, whereas attackers tend to move in a graph-like fashion. Nevertheless, it's a good tool to help non-IT people understand that "a hack" isn't just a single step, it's a series of steps and that if you can interrupt attackers along those steps you can thwart them. Let's briefly go through the phases of a kill chain.
If you look at most of the high-profile hacks that make the news, nearly all started with some form of identity compromise. This can be achieved with a phishing email or a password spray attack (and many other methods of course). The latter is simply trying common passwords against all your user accounts, a few at a time, so that protections don't necessarily spot the attack. If you don't ban bad passwords, how many users in a company might use "Password1"? The attacker only needs one hit to get a foothold.
Once in, an attacker will start the reconnaissance phase to figure out what kind of access the compromised user has, what groups they're a member of and if any other user's credentials (Kerberos tickets or NTLM hashes) are available on the compromised PC. They'll probably also use DNS to map out the network to understand where servers are located.
They'll then try to compromise further credentials to elevate their privilege (perhaps using a tool such as BloodHound to find the shortest path to administrator credentials) so they gain access to more systems. This is called lateral movement. Eventually they'll find and compromise a domain administrator credential and achieve the domain dominance phase. A potential last phase (depending on the attacker's motives) is exfiltration where sensitive data is copied from your network to the attacker's systems.
The average time (based on Microsoft's numerous Incident Response engagements) to achieve domain dominance is 48 hours. Most business networks have no insight into this activity (it's all there in event logs and network traffic but, no-one will find it unless you have a good tool to analyze and "connect the dots") and on average it takes them six months to realize that they've been compromised.
This is where AATP and ATA come into the picture. During the recon phase they'll detect LDAP reconnaissance, account enumeration, user and IP address enumeration and host/server name enumeration. During the compromise credential phase brute force attempts and suspicious VPN connections will be flagged whereas the lateral movement phase will flag Pass-the-Ticket, Pass-the-Hash and Overpass-the-Hash. These attacks are examples of using credentials to impersonate other users to move to other systems in the environment. The reason these work in a Windows network is because all credentials for any user who has logged on to a system (since reboot) are stored in memory to facilitate single-sign-on, so that you don't have to provide your username and password every time you access another file or SharePoint server, for example. Mimikatz is a popular tool for this phase.
Finally, during the domain dominance phase activities such as Golden ticket attacks, DCShadow, DCSync and Skeleton Key amongst others are brought to your attention.
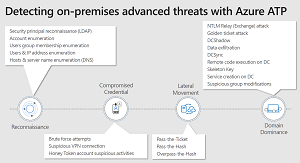 [Click on image for larger view.]
Figure 2. AATP and the Kill Chain (source: Microsoft)
[Click on image for larger view.]
Figure 2. AATP and the Kill Chain (source: Microsoft)
Deployment
Setting up AATP is straightforward, create a tenant (previously known as a workspace), configure it with a an AD user account (only needs to have read access to the directory), download and install the sensor (agent), either on standalone, domain joined servers (for very high security environments) or directly on your DCs.
ATA requires more work and planning (and sizing), and I recommend running the sizing tool to get an idea of the kind of system capacity you'll need.
Recent Improvements
AATP in particular is being improved continuously, and recent additions include deeper integration with other Microsoft security products, most notably Microsoft Cloud App Security (MCAS), which also focuses on identity, but instead of AD accounts, it tracks cloud usage and identities in SaaS services along with integration with Azure AD Identity Protection. This helps address another growing issue, hybrid identity across cloud and on-premises as a vector for attackers to breach a cloud account and then move to on-premises. The MCAS
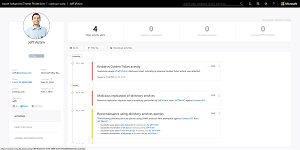 [Click on image for larger view.]
Figure 3. User Account Context Information
[Click on image for larger view.]
Figure 3. User Account Context Information
The investigation priority score is relatively new and helps busy security analysts focus on the most important incidents and risky users first. AATP is also integrating with Secure Score to help you measure your security posture improvements as you implement more hardening in your environment. The new Identity Security posture is very interesting and helps you identify systems and services in your environment that rely on LDAP simple bind, NTLM v1 and Kerberos unconstrained delegation, all common in enterprises with legacy systems and all attractive to attackers as they're old and vulnerable.
AATP is already integrated with Microsoft Defender ATP to bring insights (particularly about running processes on client computers) to the overall view of attacks.
ATA interfaces with your SIEM and your Syslog infrastructure. AATP also talks to your SIEM and Syslog servers. Here's a series of recent webinars if you'd like to learn more about AATP.
Conclusion
I really like AATP (and to a lesser extent ATA, here's the upgrade guide). It's easy to deploy and the insight it provides for many different attacks is actionable and useful. People may contrast AATP with other SIEMs and security products that are more generic, but when it comes specifically to AD attacks, AATP is the best solution. Give the trial a whirl -- you never know what you might find already lurking in your domain.