How-To
Azure Networking: Ignite 2019 Edition
Microsoft's global network connecting datacenters that house Azure, Office 365, Bing, Xbox etc. is the second largest network in the world (after the internet). At the Ignite conference Microsoft introduced several new and improved services for those using Azure, this article will cover these enhancements.
We'll look at internet connectivity and analysis of that traffic, connecting securely to Azure using satellites, Virtual WAN, ExpressRoute and Site to Site VPN improvements, IPv6 enhancements, the new Firewall Manager and Application Gateway / Front Door along with Web Application Firewall improvements.
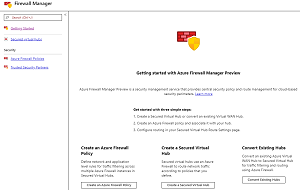 [Click on image for larger view.] Figure 1: Azure Firewall Manager
[Click on image for larger view.] Figure 1: Azure Firewall Manager
Peering Service & Internet Analyzer
Large public cloud providers have different approaches to how users connect to their cloud datacenters. GCP and Azure prefers to get traffic onto their own backbone network as soon as possible, whereas AWS relies more heavily on the internet to handle user traffic according to this ThousandEyes's report.
Microsoft is going to improve this even further with Azure Peering Service, intended to ensure that there's only one ISP between your locations and an Azure Point of Presence (POP or Edge site -- there are 160 of these). You sign up with an ISP that's part of the service and they'll have optimized connectivity to Office 365, Dynamics 365 and Azure. Optionally you can enable user latency measurements, BGP route monitoring and alerts for BGP leaks / hijacks.
Internet Analyzer is another preview service that lets you measure and compare the end user experience for your applications (a small JavaScript client is deployed in your application), handy for checking on CDN / Front Door implementation results and for comparing on-premises and cloud deployments to prepare for migrations.
Satellite Connectivity
ExpressRoute is a great option for larger businesses relying heavily on Azure, instead of connecting with VPN links over the internet you have your own private, dedicated link (see below). But there are locations on the planet where it's not easy to get a connection or maybe you're on a ship that's moving. ExpressRoute via satellite may be a solution for your business, offered with Viasat, SES and Intelsat.
Virtual WAN
Azure is a player in Software Defined WAN (SD-WAN) through Virtual WAN, released last year. Fairly new is the integration with ExpressRoute, Point to Site (P2S) VPN connectivity and the ability to pick paths from a branch to another location. In preview is integration with Azure Firewall (see below) and Hub/Any-to-any connectivity. The latter connects branches to Azure, branches to each other, ExpressRoute and S2S VPN connected locations to each other, P2S VPN users to sites and vNets to vNets. If you think this is just about slightly improved connectivity and you're better off sticking with your current telecom provider's three-year lock-in contract for your WAN I highly recommend this session from Ignite. The global corporate network of the future is agile, software based and rides cloud backbones wherever possible.
ExpressRoute
Over the last year ExpressRoute has been improved with FastPath (bypassing the Virtual Network Gateway in Azure, thus providing better throughput and latency) and the addition of more locations and telecom partners. ExpressRoute Local is an interesting new SKU (new connections only) for sites close to Azure datacenters. For speeds of 1Gbps and up you'll get a connection to that local region that has no egress data transfer charges, useful if you're looking for a way to migrate large amounts of data to the cloud.
Bidirectional Forwarding Detection (BFD) improves the speed at which link failures are detected and failover happens. ExpressRoute Direct gives you dual 10 or 100 Gpbs connectivity directly to Azure and now support MACsec, encrypting ALL traffic between you and Azure with keys that you manage.
Site to Site and Point to Site VPN
The scale has been improved for VPN with up to 10 Gbps to Azure and up to 10,000 P2S connected users with the new Gateway SKUs. P2S now offers Azure Active Directory authentication (including MFA / Conditional Access) in preview and the VPN client now uses the OpenVPN protocol.
Troubleshooting is also going to become a bit easier with VPN gateway packet capture in PCAP / ETW format, you can filter based on source subnet or port, destination subnet or port or protocol as well as TCP flags (SYN, ACK, FIN, URG, PSH, RST).
IPv6
IPv6 is a bit like “the year of Linux on the desktop” -- not happening. But as more and more devices are connected the reality of IPv4 address depletion is setting in and so IPv6 in vNets is now available. NSG rules, User Defined Routes (UDR), vNet peering and DDOS protection all fully support IPv6 addresses and if you use IPv6 you can have native connectivity from on-premises to your Azure vNets. You can add support to an existing vNet to try it out and if it doesn't work you can disable it again. The basic and standard load balancer supports IPv6 health probes and its rules can be configured with IPv6 addresses. If you're a Cisco shop you can use the Cisco Cloud Services Router (CSR) 1000V to manage dual stack v4/v6 connectivity.
The coverage isn't complete however, support for IPv6 in ExpressRoute and VPN Gateway is still forthcoming (promised for 2020) as is support for containers and PaaS services such as Storage and SQL.
Firewall Manager
In Azure we've always had Network Security Group (NSG), a free software firewall to control traffic to and from VMs and other services. In larger environments NSGs can become hard to manage as there's no central place to enforce policy and update rules. Last year we got Azure Firewall, a PaaS service firewall with centralized control, capable of managing a hub and spoke architecture easily. But if you had multiple Firewalls in different regions they had to be managed separately, the new Firewall Manager lets you manage all Firewall from a single place. You can define rules in one region and use them in any other region and you can have a central Firewall policy that manages Firewalls in a hierarchy where firewalls down the line can have their own set of rules (as long as they don't try to allow traffic that's blocked centrally).
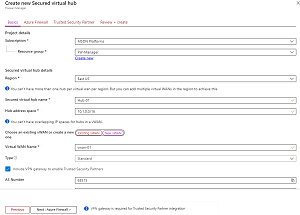 [Click on image for larger view.] Figure 2: Creating a Secured Virtual Hub
[Click on image for larger view.] Figure 2: Creating a Secured Virtual Hub
Firewall and Virtual WAN also ties in with Secured Virtual Hubs, a new way to do a managed central vNet that doesn't require you to do User Defined Routing (UDR) to manage traffic flow. It also ties in with Security as a Service (SECaaS) providers, letting you add third party services (zscaler and iboss today with Check Point coming) into your network for security management. On the roadmap is support for managing NSGs through Firewall Manager.
Front Door, Application Gateway & WAF
If you need an application delivery service in a single region use Application Gateway, version 2 now works as an ingress controller for Azure Kubernetes Services (AKS) with Letsencrypt certificate support (free), integrates with Key Vault for centralized management of SSL certificates and coming soon there will be a wildcard listener so you don't have to create a new listener for each subdomain. Version 2 is also considerably faster to deploy (less than 5 minutes compared to 15 minutes+) and to update rules faster (less than 40 seconds). Front end certificates are stored in Key Vault and certificate rotation is handled automatically for you.
If on the other hand you need global application delivery use Front Door. It integrates SSL termination and DDoS protection.
Both these services also provide a Web Application Firewall (WAF) which gives you OWASP rule sets (2.2.9, 3.0 and 3.1) and in preview is support for Microsoft Threat Intelligence (including the ability to manage both good and bad bots with a BotManager RuleSet) and site / URI path specific WAF policies.
Conclusion
We covered Private Link last month and it's arguably the biggest change for Azure networking this year, combined with the new features and enhancements we've looked at in this article cloud architects and businesses have more choices than ever when designing Azure deployments.