How-To
Security in Focus at Ignite 2020
Paul Schnackenburg details the security-related news coming out of the Microsoft Ignite 2020 event, ranging from Microsoft 365 Defender to Azure Sentinel to Azure Active Directory (AAD) and much more.
Microsoft's virtual Ignite conference took place last week (part 1 that is, part 2 is coming in March 2021) and while there were many new features announced across Microsoft 365, Azure and on-premises, in this article I'll focus on the security enhancements.
There were several new features announced, along with sweeping name changes across nearly the whole portfolio of services and products. If the names were confusing before but you'd just about got your head around them (like I had), now you'll have to get used to the new names instead. On the flip side, at least the new names are descriptive.
All Microsoft statistics quoted in this article are from presentations given at Ignite 2020.
Microsoft 365 Defender
Let's start with Microsoft Defender for Endpoint which used to be known as Microsoft Defender Advanced Threat Protection. No longer a basic antivirus solution, this is a comprehensive Endpoint Protection and Detection (EDR) tool for all your endpoints, with agents for MacOS, Linux, Android (released to General Availability at Ignite), iOS (released in preview at Ignite) and of course Windows.
To deploy this machine learning (both on the endpoint and in the cloud) based EDR tool in Windows you simply run a script to onboard the client, as the bits themselves are already built into the OS. New features include Threat and Vulnerability management for MacOS (already GA for Windows), which identifies vulnerable versions of installed applications, how many devices they're installed on and how frequently they're used and suggests remediation steps.
Protection for mobile devices is particularly pertinent, MacOS has had 133,270 threats this year (this includes viruses, adware, downloaders, trojans etc.), Linux comes in at 129,430 threats and Android has had 3.07 Million. The largest threat on mobile (90%) is phishing either via email, SMS or another messaging app, Defender for Endpoint provides protection against this on both Android and iOS.
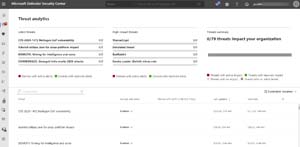 [Click on image for larger view.] Microsoft Defender for Endpoint Portal
[Click on image for larger view.] Microsoft Defender for Endpoint Portal
The public preview of Defender Application Guard for Office is very interesting, this is extending an existing technology from the Edge browser to Word, Excel and PowerPoint. Once enabled, when you access an untrusted document it'll open in a Hyper-V based isolated container, minimizing risk to the host OS from malicious macros or code.
The second service in this family is Microsoft Defender for Office 365, formerly known as Office 365 Advanced Threat Protection which is an extra layer of protection above Exchange Online Protection (EOP). If a user is sent an email attachment that Office has never seen before and the normal EOP AV scans (three different engines) don't flag it as malicious the attachment is opened in a VM and its behavior is analyzed. Meanwhile the user receives the email with a message that the attachment is being scanned. If the attachment is benign it's delivered, otherwise it's blocked. This service also scans URL links in documents, emails and in Teams communications at the time of click to ensure that the user isn't being tricked into visiting a malicious webpage.
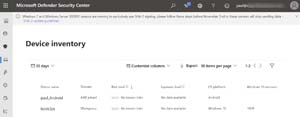 [Click on image for larger view.]Windows 10 and Android devices in Defender for Endpoint
[Click on image for larger view.]Windows 10 and Android devices in Defender for Endpoint
Third in this group is Microsoft Defender for Identity (previously known as Azure Advanced Threat Protection -- a confusing name as it's got nothing to do with Azure). It protects your on-premises Active Directory. Sensors installed on your Domain Controllers (or on member servers) gathers network packet data and event logs and using machine learning builds up knowledge of normal patterns of user account and device account behavior. It warns you when an attacker is in your network as they attempt to perform reconnaissance, move laterally from machine to machine and elevate privileges to eventually achieve domain dominance, all activities that leave traces.
These tools are also closely integrated and surface their alerts and incident information in the central console Microsoft 365 Defender which used to be known as Microsoft Threat Protection.
Azure Active Directory (AAD)
This is the world largest identity directory with over 200,000 tenant organizations, 345 Million active monthly users and 30 Billion authentication requests per day. In August 2020 alone there were 9 Million high risk sign-in attempts and 2 Million compromised accounts and 5.8 Billion attacker driven sign ins.
Conditional Access (CA) policies are a way to granularly govern access to applications and data -- if you're coming from a company managed device in a location you normally login from, username and password is sufficient to access this particular app. On the other hand, if you're logging in from an unusual location, or on a personal device, we'll automatically prompt you for MFA. Azure Identity Protection (IdP) lets you build policies for user risk (has this user's credentials been seen in a recent data breach for example) and sign-in risk (unusual location, unknown device, anonymous IP, impossible travel etc.), these policies can automatically take action based on the risk level, such as forcing the user to perform MFA and then reset their password.
If your company builds applications and use Azure AD B2C to manage identity for them (using Google, Facebook, Microsoft Accounts etc.) you can now use CA policies and IdP for those identities.
There's a new insights feature for CA that shows you were your policies may have gaps, the default mode for a new policy is Report only so you can see what the policy will do before enforcing it and the API for access to CA policies is Generally Available. CA policies in AAD block 80 Million attacks per day. Probably the most interesting release at Ignite are new CA templates and the ability to manage CA policies like code -- more info in this Github repo.
Also new(-ish) is the ability to assign AAD Roles (Global Administrator, Password Administrator etc.) to groups instead of individual users.
Azure Defender
This is the new name for several services in Azure -- Azure Defender for Servers, previously Azure Security Center, Azure Defender for SQL, previously known as Advanced Threat Protection for SQL and Azure Defender for IoT (Azure Security Center for IoT).
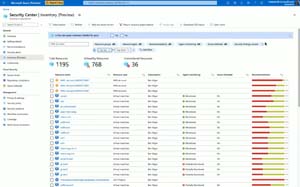 [Click on image for larger view.]Azure Defender AWS resources alongside Azure resources (courtesy of Microsoft)
[Click on image for larger view.]Azure Defender AWS resources alongside Azure resources (courtesy of Microsoft)
Azure Defender for SQL now extends to your servers on-premises and in other clouds and the recent acquisition of CyberX is integrated to provide protection for existing Operational Technology deployments. Based on Azure Arc the insight and protection offered by Azure Defender can be extended to AWS, GCP and other cloud locations. This includes CIS benchmark reporting for both AWS and GCP as well as Secure Score integration. This means that your overall Secure Score for your cloud security posture will take into account the state of your resources in AWS and GCP.
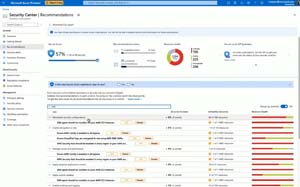 [Click on image for larger view.]Azure Defender combined Secure Score across clouds (courtesy of Microsoft)
[Click on image for larger view.]Azure Defender combined Secure Score across clouds (courtesy of Microsoft)
Azure Sentinel
Microsoft's cloud based SIEM didn't get a rebrand but a few new features such as a smoother way to integrate Threat Intelligence from external sources (TAXII and others) and letting you manually add a Threat Indicator in a new management blade. The CyberX information mentioned above is also surfaced in Sentinel.
 [Click on image for larger view.]Azure Sentinel UEBA alert
[Click on image for larger view.]Azure Sentinel UEBA alert
The biggest new feature however is User and Entity Behavior Analytics (UEBA), building up a database of what's normal activity for user accounts and devices and raising the alarm when anomalous behavior occurs. Watchlists lets you import CSV files of non-security data such as critical assets, terminated employees etc. and use these data in queries.
If you're particularly adventurous you can now build your own Machine Learning models in Sentinel.
Information Protection
The two most interesting reveals for Microsoft Information Protection (MIP) is first; the integration with Symantec DLP, McAfee MVISION, Relativity for Communications Compliance, VMWare Boxer and VMware Workspace One. Second; the new Endpoint DLP solution (the successor to Windows Information Protection, WIP) is now in public preview.
To govern data outside of Office 365 there were already some Microsoft connectors for sources such as Twitter, Facebook, LinkedIn, Instant Bloomberg, Bloomberg Message and ICE Chat. These have now been extended with a new connector for Physical Badging for Linnel and Honeywell building access systems. Telemessage and Globanet now also provides 25 additional connectors for sources such as Slack, Zoom etc.
Conclusion
If you're into compliance management, there are many new features including integration of Advanced eDiscovery into Teams, the new Compliance Manager UI, API access and customer key for encryption in Teams.
There's no doubt that Microsoft is serious about security and offers an extremely strong, integrated solution to monitor and protect your endpoints, servers, on-premises and multi-cloud IT infrastructure along with identities and data. In today's world that's been turned upside down in so many ways, you could definitely do worse than having Microsoft in your corner when the bad guys come for your ICT systems.
For more coverage of Microsoft Ignite 2020 from Virtualization & Cloud Review and sister sites, see: