News
VMware Points Carbon Black Security to Containers, Kubernetes
VMware is expanding its Carbon Black Cloud Workload security offering to include containers and Kubernetes, from development through production.
The company announced the VMware Carbon Black Cloud Container solution with the intention of providing increased visibility while enabling compliance and beefing up security for containerized applications in public clouds and on-premises implementations.
The aim is to infuse security at early development stages through production, as opposed to some schemes where security is added onto a workload as an afterthought.
"The VMware container security module will empower InfoSec and DevOps teams to better collaborate and identify risks earlier in the development cycle with built-in security," the company said in a recent news release. "The expanded offering will provide a new vantage point to allow cross-functional teams to detect and fix vulnerabilities to achieve simple, more secure multi-cloud Kubernetes environments."
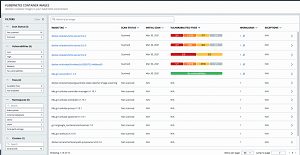 [Click on image for larger view.] Monitoring Kubernetes ContainerImages (source: VMware).
[Click on image for larger view.] Monitoring Kubernetes ContainerImages (source: VMware).
The solution is being rolled out in stages, as VMware container image scanning and CI/CD integration functionality is expected to be available this month, while runtime security for detection and response will be available later in the year.
Those capabilities are part of the entire solution that will include:
- Security Posture Dashboard: Provides a combined view of vulnerabilities and misconfigurations to enable complete visibility into security posture across Kubernetes workload inventory. InfoSec and DevOps teams can gain deep visibility into workload security posture and governance to enable compliance, with the ability to freely explore Kubernetes workload configuration via customized queries.
- Container Image Scanning and Hardening: InfoSec and DevOps teams can scan all container images to identify vulnerabilities and restrict the registries and repositories that are allowed in production. Teams can set minimum standards for security and compliance, generate compliance reports and follow CIS benchmarks and Kubernetes best practices.
- Prioritized Risk Assessment: Vulnerability assessments allow InfoSec and DevOps teams to review images running in production and only approved images are deployed. Security teams can use the prioritized risk assessment to detect and prevent vulnerabilities by scanning Kubernetes manifests and clusters.
- Compliance Policy Automation: Infosec teams can shift-left into the development cycle, streamline compliance reporting, and automate policy creation against industry standards such as NIST, as well as the customer’s organizational requirements. This enables the integrity of Kubernetes configurations through control and visibility of workloads that are deployed to an organization’s clusters. Customizable policies help enforce configuration by blocking or alerting on exceptions.
"IDC predicts that 'By 2025, nearly two-thirds of enterprises will be prolific software producers with code deployed daily, over 90 percent of apps will be cloud-native, and there will be 1.6 times more developers than today,' " the company said in a blog post last week. "As organizations catapult into the digital economy in what seems like an overnight transformation, we see the prediction come to life at an accelerated pace. The need to integrate security throughout the DevOps cycle becomes more urgent as pervasive challenges highlight the widening security gap."
About the Author
David Ramel is an editor and writer at Converge 360.