How-To
Preventing Configuration Drift for AWS Resources, Part 1: Creating Rules
As organizations accumulate more and more AWS objects, Brien Posey explains, those objects can become increasingly difficult to manage at scale, so he provides help.
As organizations accumulate more and more AWS objects, those objects can become increasingly difficult to manage at scale. AWS Config is designed to help with this problem by providing you with an always-up-to-date inventory of your AWS resources while also giving you the ability to detect and remediate configuration changes that cause your AWS objects to become non-compliant with rules that you establish.
You can access AWS Config by selecting it from the list of AWS services (it's located in the Management and Governance section). When the console opens, will be prompted to set up the service. However, Amazon provides a one-click setup option, which you can see in Figure 1, and this option makes the setup process completely painless.
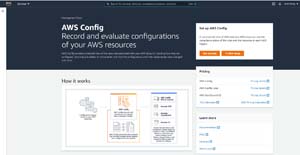 [Click on image for larger view.] Figure 1: If this is the first time you have used AWS Config, there is a one-click setup option.
[Click on image for larger view.] Figure 1: If this is the first time you have used AWS Config, there is a one-click setup option.
Once AWS Config has been set up, you will see a summary of your AWS resources, as shown in Figure 2 (click the View Dashboard button if the inventory does not automatically appear). It is worth noting that like most other AWS services, AWS Config is regional, meaning that it is only aware of resources within the currently selected region. If you switch to a different region within which you have not previously used AWS Config, you will be prompted to complete the setup process once again.
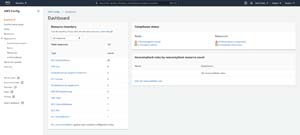 [Click on image for larger view.] Figure 2: AWS Config provides you with a list of the resources that you are using.
[Click on image for larger view.] Figure 2: AWS Config provides you with a list of the resources that you are using.
The inventory summary shown in the figure above can be useful for tracking the growth of your AWS deployment and for avoiding surprise bills related to forgotten AWS objects. AWS Config's main purpose however, is to help admins to maintain object configurations that adhere to the organization's security and compliance requirements.
In order for AWS to verify that your cloud resources adhere to your organization's compliance requirements, you will need to create a series of rules. These rules define what it means for a particular resource type to be in compliance. Hence, if a rule check fails, then the resource that is tied to the failure can be said to be out of compliance.
To create a compliance rule, select the Rules tab and then click on the Add Rules button. This will cause AWS to open the Specify Rule Type screen, which you can see in Figure 3.
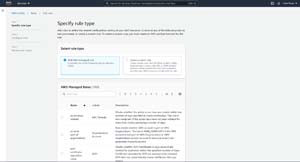 [Click on image for larger view.] Figure 3: The Specify Rule Type screen lets you choose the type of rule that you want to create.
[Click on image for larger view.] Figure 3: The Specify Rule Type screen lets you choose the type of rule that you want to create.
The Specify Rule screen allows you to choose between using an AWS managed rule and creating your own custom rule. The AWS managed rules are essentially just template rules that Amazon provides for your use. These AWS managed rules are based on Amazon's established best practices.
Using AWS managed rules can make your life easier since you won't have to create rules from scratch. Even so, there are hundreds of AWS managed rules to choose from and figuring out which rule to use can be a challenge. However, Amazon does provide a search box that you can use to locate a particular rule. If you don't know exactly what you are looking for, then you can always search based on a service name to find managed rules that apply to a given service. For example, you might enter EC2 to find rules related to EC2 instances. Once you choose the managed rule that you want to use, click Next and you will be taken to the Configure Rule screen., which you can see in Figure 4.
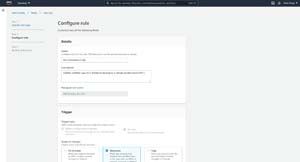 [Click on image for larger view.] Figure 4: The Configure Rule screen allows you to configure the rule's behavior.
[Click on image for larger view.] Figure 4: The Configure Rule screen allows you to configure the rule's behavior.
The first thing that you will need to do on the Configure Rule screen is to enter a name and a description for the rule that you are creating.
If you are creating a custom rule, you will need to define a trigger type, which means specifying whether the rule will be evaluated in response to a configuration change or if the evaluation will occur on a scheduled basis. In the case of managed rules, the trigger type is automatically set to evaluate the rule in response to configuration changes.
Next, you will need to specify what type of change will cause the rule to be evaluated. You can evaluate the rule in response to any change at all, a change involving a resource, or a modification to a resource's tags. Although each of these options has its place, it is especially common to evaluate rules following changes to resources.
If you do base a rule trigger on configuration changes made to resources, then you will need to specify a resource category and resource type. A resource category is simply a high-level category. Some of the categories include AWS resources, TrendMicro resources and FireEye resources. The resource type is a specific configuration item related to the selected resource category. Some of the EC2 related resource categories for example, include AWS EC2 Host, AWS EC2 Instance and AWS EC2 InternetGateway.
The nice thing about using managed rules is that you don't have to worry about selecting resource categories or resource types. Amazon has already done that for you. What you do have to do, however, is to populate the parameter on which the rule should be based. If, for example, you are creating a rule to check to see that an EC2 instance is part of the correct VPC, then you will want to set the VPCID key to the name of the VPC that the instances should belong to. You can see an example of this in Figure 5.
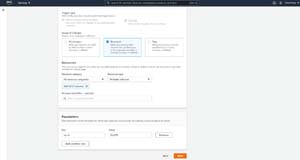 [Click on image for larger view.] Figure 5: You will need to specify the parameters that will be evaluated.
[Click on image for larger view.] Figure 5: You will need to specify the parameters that will be evaluated.
Simply click Next, and you will be taken to a screen that gives you the opportunity to review the rule that is about to be created, as shown in Figure 6. Click the Add Rule button to create the rule.
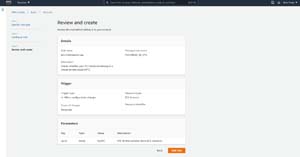 [Click on image for larger view.] Figure 6: The Review and Create screen gives you the opportunity to review the rule before it is created.
[Click on image for larger view.] Figure 6: The Review and Create screen gives you the opportunity to review the rule before it is created.
Now that I have shown you how to create configuration rules, I want to show you how the rules work and what you can do if you find resources to be out of compliance. I will be discussing all that and more in Part 2.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.