News
'Ransomware Sommelier' Crowdsources Initial Access Vulnerability List
Finding no one-stop-shop for a list of initial access vulnerabilities used by ransomware attackers, cybersecurity expert and Virtualization & Cloud Review tech event presenter Allan Liska started one on his own and crowdsourced the effort on Twitter.
That social media platform is where the effort was started by Liska, who describes himself as "Ransomware Sommelier" in his handle.
"I could use your (yes you) help," said Liska, an intelligence analyst for Recorded Future, in a Sept. 11 tweet. "I am trying to compile a list of vulnerabilities ransomware groups (or their access brokers) use to gain initial access. Excepting Kaseya, are there any others I am missing from this list? Remember, this is initial access only."
His initial list looked like this:
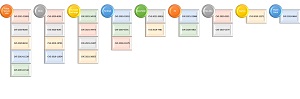 [Click on image for larger view.] The First List (source: Twitter).
[Click on image for larger view.] The First List (source: Twitter).
On Friday (Sept. 17), it looked like this:
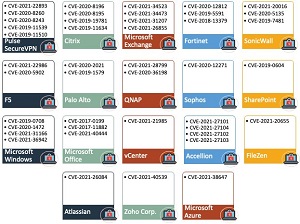 [Click on image for larger view.] The List Six Days Later (source: Twitter).
[Click on image for larger view.] The List Six Days Later (source: Twitter).
"So, we are up to 42 vulnerabilities across 17 technologies (with 1 pending) that ransomware groups exploit for initial access," Liska said in the update. "This is why preaching 'just patch' isn't good enough. I don't know what the answer is, but what we're doing clearly isn't working."
Liska is attempting to help find the answer on several fronts, including as a presenter in editorial webcasts on cybersecurity in general and ransomware in particular that are published by Virtualization & Cloud Review. His most recent such presentation was titled "The Top Ransomware Threats You're Facing Right Now," just one of three sessions in the Aug. 31 "Ransomware & Cloud Data Protection Summit" that is now available on demand.
There, he discussed the ransomware threat in detail, including presenting slides that provide information on common vulnerabilities, or CVEs (Common Vulnerabilities and Exposures). "Open source and related projects are also targets," one slide says. "19 CVEs tied to ransomware exist in in Jenkins, MySQL, OpenStack, TomCat, Elasticsearch, OpenShift, JBoss and Nomad."
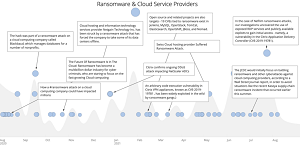 [Click on image for larger view.] Ransomware & Cloud Service Providers
[Click on image for larger view.] Ransomware & Cloud Service Providers
Liska started his Twitter effort less than two weeks after that presentation and was helped by several people. "I sincerely appreciate all of the great suggestions," he said.
When one person asked if there was an actual site that provided such information, Liska responded, "There isn't, which is part of the problem. This came from crowdsourcing because the data comes from so many different sources it can be hard to track."
Thanks to the "Ransomware Sommelier," that tracking might be getting a little easier, it seems.
In addition to Liska's and other on-demand online summits many more ransomware and security summits are coming up in the next few weeks, including:
About the Author
David Ramel is an editor and writer at Converge 360.