News
Data Security Expert: Open Storage Buckets Will Be No. 1 Breach Threat
Expressing amazement that SQL injection is still a top data security threat, expert Karen Lopez predicted that the longstanding problem will be overtaken by users planting data on open storage buckets like AWS S3 and Azure Data Blob.
"SQL injection -- I think that's what's going to rapidly approach and replace that as [a top] data protection issue is going to be people who store my data in an open bucket, say an S3 bucket or an Azure Data Blob somewhere and it's not protected," she said.
"They'd put it there usually for dev or test reasons. They want to share it with an offsite contractor. They want to have access when they get to work on it at home, whatever it is they're thinking at the time. They pop some production data into an open bucket and leave it there -- forget to turn it off -- and think that just because it was just open there for a few minutes, it's fine. No one knew it was there. That's gonna become the No. 1 way that data breaches are discovered."
Lopez, who goes by the moniker @DataChick on Twitter, shared her expertise with an audience of hundreds during a recent online tech summit put on by Virtualization & Cloud Review. She was speaking in her segment -- "Modern Cloud Data Protection Best Practices" -- that was part of the "Cloud Data Protection for 2022 Summit," now available for on-demand viewing.
The senior project manager at InfoAdvisors is amazed that SQL injection is still even a thing.
"So right now, SQL injection is still listed as one of the top ... methods for data breaches," she said. "SQL injection, a problem we've known for data protection for decades, that we have automated tools to check for, that there are services you can use to check for SQL injection in your application code. And yet we still continue to deliver code into production that has these vulnerabilities."
Indeed, the Open Web Application Security Project (OWASP) still lists SQL injection among the OWASP Top 10:2021, clocking in at No. 3 after being No. 1 in 2017 and accounting for two-thirds of all web app attacks from 2017 to 2019.
As the OWASP graphic below shows, "Sensitive Data Exposure" has climbed during that time, reaching No. 2 behind "Broken Access Control." While open storage buckets are different from compromised web apps, the OWASP data gives credence to Lopez's prediction about the growing data protection problem.
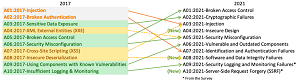 [Click on image for larger view.] OWASP Top 10:2021 (source: OWASP).
[Click on image for larger view.] OWASP Top 10:2021 (source: OWASP).
"We have ways of sharing data -- production data -- that might be used to diagnose a problem, and that people are improperly, and in some cases, illegally using it for dev test data," Lopez continued. "We have ways of protecting against that. If you find that your development process is to put production data in some storage blob somewhere for someone to get to it, that stuff has to stop now. We think that, once those become enough of a problem that cloud providers will start implementing ways of profiling your data to see if there's credit card data, or medical images or something unprotected.
 "If you're currently working at an organization where devs and DBAs are told that the role of the security team is to do security testing, then it's time to stand up and say 'no, it needs to be part of our development environment.' "
"If you're currently working at an organization where devs and DBAs are told that the role of the security team is to do security testing, then it's time to stand up and say 'no, it needs to be part of our development environment.' "
Karen Lopez, Sr. Project Manager and Architect, InfoAdvisors
"I can envision that happening, and who wants your cloud providers snooping around in your data just because you put it in an open blob? All of your data and designing test cases should test data protection and security items. If you're currently working at an organization where devs and DBAs are told that the role of the security team is to do security testing, then it's time to stand up and say 'no, it needs to be part of our development environment.' "
That sounds a lot like DevOps -- or DevSecOps as is the current fad -- and Lopez's co-presenter in the summit, Ian Thornton-Trump, had his own prediction about that.
"I want to talk about the future, and about how I see DevOps merging into DevSecOps, backed up by a cyber-threat intelligence program," said the CISO at Cyjax.
 "I say this, with all due respect to the managed service providers out there, IT is security and security needs to be IT."
"I say this, with all due respect to the managed service providers out there, IT is security and security needs to be IT."
Ian Thornton-Trump, CISO, Cyjax
"This is so, I think, important for reducing the amount of silos in your organization between security responsibility, right, and the actual functioning of the IT department. Because I say this, with all due respect to the managed service providers out there, IT is security and security needs to be IT."
Lopez also discussed DevOps in her presentation. "If you're new into DevOps, and DataOps and all the other Ops that are coming up -- I even saw OpsOps the other day, operations ops, which had me confused -- if you're new to that thinking for coding and deployment, you also need to think about securing your DevOps pipeline and your source control so that you can understand what's going on while you're doing the development."
She also provided some highlights that align with the thoughts she expressed in her presentation:
- undue complexity increases security risks. But data is complex. If you want to engineer out complexity, go out and make the world simpler and come back to me.
- You can't protect data you don't know your organization is collecting and storing.
- Asking people what data is collected is never going to be enough to find all the data.
- Data masking works best when the masking is standardized.
- Attackers are changing their methods, so we need to change our methods of thinking about security.
Of course, Lopez and Thornton-Trump discussed many more data security issues, with Lopez providing this list of best practice thoughts:
 [Click on image for larger view.] Best Practices (source: OWASP).
[Click on image for larger view.] Best Practices (source: OWASP).
As mentioned, the summit is available for on-demand viewing if you want to see those best practices fleshed out with many more expert insights.
Upcoming are more live summits on security, which provide benefits such as real-time Q&A with presenters (not to mention a chance at a prize). Some of those coming up in the next few weeks include:
About the Author
David Ramel is an editor and writer at Converge 360.