News
Cloud Honeypots Shed Light on 'Shocking' Exposed Service Attacks
Misconfigured and exposed cloud storage buckets are a well-known cybersecurity vulnerability, but new research sheds light on less-publicized exposed service attacks, thanks to a network of honeypots that attracted the threat actors.
The research was conducted by the Unit 42 Threat Intelligence team at Palo Alto Networks, which last summer created a global honeypot infrastructure of 320 nodes in order to better understand the attacks against exposed services in public clouds. They then deployed multiple instances of remote desktop protocol (RDP), secure shell protocol (SSH), server message block (SMB) and Postgres database in the honeypot infrastructure, finding that 80 percent of the honeypots were compromised within 24 hours and all were compromised within a week.
"The speed of vulnerability management is usually measured in days or months," Palo Alto said in a Nov. 22 post. "The fact that attackers could find and compromise our honeypots in minutes was shocking. This research demonstrates the risk of insecurely exposed services."
The research measured mean time-to-first-compromise, mean time-between-compromise, number of attacker IPs observed in a honeypot, number of days an attacker IP was observed and many other metrics.
"An insecurely exposed service is one of the most commonly seen misconfigurations in cloud environments," Palo Alto said. "These services are discoverable on the internet and can pose a significant risk to cloud workloads in the same infrastructure. Notorious ransomware groups such as REvil and Mespinoza are known to exploit exposed services to gain initial access to victims' environments."
Regarding those attack metrics, there was actually quite a bit of difference in how quickly the various services were compromised for the first time, with SSHD being hit in a mean time of 184 minutes, while the mean time for the first Samba (SMB) service compromises was 2,485 minutes:
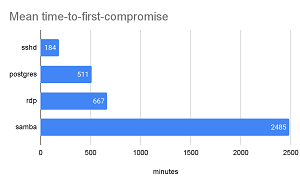 [Click on image for larger view.] Mean Time-to-First-Compromise (source: Palo Alto Networks).
[Click on image for larger view.] Mean Time-to-First-Compromise (source: Palo Alto Networks).
Researchers also discovered other differences among attacks on the services, with Palo Alto highlighting these findings:
- SSH was the most attacked application. The number of attackers and compromising events was much higher than for the other three applications.
- The most attacked SSH honeypot was compromised 169 times in a single day.
- On average, each SSH honeypot was compromised 26 times daily.
- One threat actor compromised 96 percent of our 80 Postgres honeypots globally within 30 seconds.
- 85 percent of the attacker IPs were observed only on a single day. This number indicates that Layer 3 IP-based firewalls are ineffective as attackers rarely reuse the same IPs to launch attacks. A list of malicious IPs created today will likely become outdated tomorrow.
While exposed storage buckets may have gotten more publicity, the company said that the exposed service problem was exacerbated by the agility of today's cloud infrastructure management, which can quicken the creation and replication of such misconfigurations.
To fight the bad actors, Palo Alto suggested several strategies that leverage cloud-native approaches with various products, unsurprisingly including the company's own wares:
"The research highlights the risk and severity of such misconfigurations," Palo Alto said in conclusion. "When a vulnerable service is exposed to the internet, opportunistic attackers can find and attack it in just a few minutes. As most of these internet-facing services are connected to some other cloud workloads, any breached service can potentially lead to the compromise of the entire cloud environment."
About the Author
David Ramel is an editor and writer at Converge 360.