News
6 'Quick Wins' for Endpoint Security Management (and 6 'Complex Wins')
These days, your infrastructure is no longer self-contained: From remote workers to cloud-based solutions to partner-controlled networks, enterprises now have to rely on Identity & Access Management (IAM), authentication and endpoint protection to keep their organizations secure. But it can get very complex very quickly.
To help organizations deal with that complexity, two cybersecurity experts recently detailed six endpoint protection "quick wins" that everyone can do to help protect themselves, as well as six more complex initiatives.
First, the simple stuff, which equally apply to home computers as well as enterprise-wide implementations:
- Enable full disk encryption
- Hardened golden workstation and server OS images
- Effective Group Policy Objects (GPO) user and computer configuration and security policies
- Endpoint Detection & Response (EDR) deployed
- Firewall enabled
- Protected local privileged accounts
These were explained in detail to an audience of hundreds who tuned in to Fridays' two-part mini-summit titled "Identity Management, Authentication & Endpoint Protection" presented by RedmondMag.com and Virtualization & Cloud Review, today available for on-demand viewing.
Helming the presentation were Ian Thornton-Trump, CISO at Cyjax, and Chris Spinks, head of Cyber Operations at Cyjax.
 [Click on image for larger view.] Quick Wins
[Click on image for larger view.] Quick Wins
Thornton-Trump noted that while the presentation focused on enterprises, these tactics applied to everyone.
"But in terms of quick wins, anybody can do this to their home computers, right?" Thornton-Trump asked.
"Not just can: must!" replied Spinks. "I think a lot of the stuff, the quick wins, are easily, easily configurable under modern systems. They, in fact, they almost demand that you do it."
As just one example, Thornton-Trump cited unused and unneeded printing and file-sharing services.
"Yeah, you know, and it breaks my heart, because every Windows machine that comes out of the box, and you install Windows 10, or Windows 11, it's got the spooler service running, by default. And then it's got the server service running, even if it will never share files. And then we've got all sorts of other services that we may or may not need. And I know like, if you're a hardcore gamer, you're turning off everything you can, so you can get more FPS (frames per second) for your DPS (damage per second), right.
 "But unless you're at that level, where you're tuning your computer for crazy performance, most people don't realize that there are gaping vulnerabilities on their system."
"But unless you're at that level, where you're tuning your computer for crazy performance, most people don't realize that there are gaping vulnerabilities on their system."
Ian Thornton-Trump, CISO at Cyjax
"But unless you're like at that level, where you're tuning your computer for crazy performance, most people don't realize that there are gaping vulnerabilities on their system, like when we talk about the spooler service, for instance. There's no reason why a spooler service should be running in a virtual environment. What are you going to print to, a virtual printer somewhere?"
His point was that Windows machines -- either in the enterprise or at home -- aren't hardened from the beginning so users and organizations have to learn to do that themselves.
He then addressed the corporate-only issues concerning endpoint security.
"So first is the vulnerability management program for the hardware, the operating system and the applications has to be extended to all the different hardware that we have out there. Now, it has to be a risk-based approach.
"The other issue is cradle-to-grave CMDB (Configuration Management Database) updates and an annual refresh program. Because what is the most difficult thing, is coming into an environment and realizing that the configuration management database, i.e., what is it? What does it do? What value does it have it to the business and who owns it are really important things to know. And this is where a lot of organizations are falling down on CMDB and asset discovery.
"There's also capabilities now when you're talking about endpoints. User and entity behavior analytics can be sucked in to give greater visibility on what that endpoint shouldn't be doing, versus what it's doing now. And that's about anomaly detection that can be easily put in once you have sort of a collective understanding, and some machine learning models about what what normal behavior looks like."
Addressing the No. 4 quick win, Role-Based Access Control (RBAC), he said organizations should only deploy the appropriate applications onto an endpoint for a particular role. So, for example, if an employee is not an accountant, they might not need access to accounting programs deployed on their machine, with such access being provided by automation only when the role changes.
He then turned to Security Assertion Markup Language (SAML) and Single Sign On (SSO).
"We talked about the dangers of SSO and SAML with third-party applications. If you've ceded control to the business on SaaS, and it's not SSO-integrated, you're going to have to have a levers policy that ensures that those accounts are terminated."
As far as SaaS, expired credentials can be a problem.
"Now, one of the great things about Office 365 is that you're financially incentivized to remove unneeded accounts and licensing, because it costs you money on a monthly basis. But in a lot of cases, you'll find older legacy SaaS things are sort of like, you buy it, and then you can add as many users as you want, and there's a whole bunch of users that are no longer with the organization. And guess what? They still have valid credentials, because a lot of a lot of SaaS applications don't have credential expiry at all."
Thornton-Trump then addressed quick win No. 6.
"And then, of course, the minimum security policies for managed and unmanaged devices that are requiring remote access. This is a fact of life that you're going to have to get used to in that a lot of your corporate data is not going to be on corporate-controlled assets. It's a fact of life. And by that I mean, if you look at the Teams application on your phone, you can get at things like OneDrive, you can get things like SharePoint, and that might be happening over a personal phone. So this is the reality of what we live in right now. And you're going to have to not only enforce minimum security policies, but adopt technologies in order to containerize your data, or be able to do things like remote wipe that remote wipe your data, not the person, not the user's data, and keep those things separate."
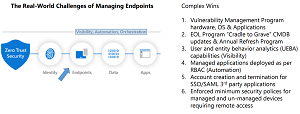 [Click on image for larger view.] Complex Wins
[Click on image for larger view.] Complex Wins
There was much more to the hour-long presentation, of course, including detailed discussion of the more complex measures that organizations can enact to boost endpoint security, pictured above.
Again, to tap into their expertise and learn best practices to follow in your organization, you can view the presentation on demand and access resources provided for this session and the companion session, Hottest Third-Party Solutions.
Tuning in live, of course, brings extra benefits, such as being able to ask questions of experts like Spinks and Thornton-Trump, not to mention the chance to win an expensive prize.
With that in mind, readers might be interested in (mostly three-session) summits coming up in March that address security as well as other issues like cloud computing, including:
About the Author
David Ramel is an editor and writer at Converge 360.