How-To
Enabling DNS Over HTTPS for Route 53 Resolver Endpoints
Some time ago, Amazon introduced the concept of using a resolver as a means for performing DNS queries across a hybrid network. Imagine for example, that you were to deploy AWS Route 53 within AWS. Route 53 would of course be able to perform DNS name resolution for those resources located within the Amazon Web Services (AWS) cloud, but it would know nothing about the resources residing in your on-premises environment or in other clouds. You can solve this problem by creating resolver endpoints. These resolver endpoints are relatively easy to set up, as I demonstrated in a recent blog post.
Recently, Amazon introduced the ability to use DNS over HTTPS (sometimes called DoH) for resolver endpoints. While there is no rule requiring the use of DNS over HTTPS, using it can improve security and privacy throughout your hybrid cloud since DNS queries are encrypted and therefore hidden from view. At the same time however, there are those who have been critical of DNS over HTTPS since using it can make it more difficult to detect certain types of security incidents. Malware that is designed to "phone home" for example, might perform a DNS query related to a web server that is known to be associated with malicious activity. Some security software is designed to detect such queries, thereby helping to locate the associated malware. Using DNS over HTTPS can hide these types of DNS queries from view.
All of this is to say that there are both advantages and potential disadvantages to using DNS over HTTPS. As such, you should carefully consider whether DNS over HTTPS is a good fit for your organization. Remember, there is no rule that says that you have to use DNS over HTTPS. You can continue using your resolver endpoints without enabling DNS over HTTPS if you so choose.
When it comes to general use of DNS over HTTPS, my opinion has always been that the benefits will usually outweigh the risks. When it comes to using DNS over HTTPS for communications between resolver endpoints however, it is almost always in your best interest to go ahead and enable it (especially since Amazon does not charge extra for its use).
While it is true that using DNS over HTTPS can make certain malicious activity more difficult to detect, keep in mind that there is an extremely narrow scope associated with this implementation. The only DNS queries that are being encrypted are those that are traversing the resolver endpoints. Other DNS traffic remains unencrypted unless you specifically choose to have it encrypted.
Enabling DNS Over HTTPS
Amazon makes it easy to enable DNS over HTTPS for Route 53 resolver endpoints. When creating a resolver endpoint, you are asked to choose the protocols that the endpoint will support. Figure 1 for example, shows the wizard used for creating an inbound endpoint. The DO53 protocol is the protocol that is normally used by the resolver. In case you are wondering about the name, it stems from the fact that DNS queries are being sent across TCP or UDP port number 53, which is also how the Route 53 service got its name.
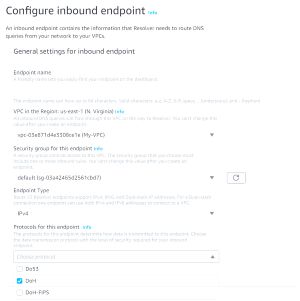 [Click on image for larger view.] Figure 1: You Have Three Protocol Choices for Route 53 Resolver Endpoints.
[Click on image for larger view.] Figure 1: You Have Three Protocol Choices for Route 53 Resolver Endpoints.
If you want to allow DNS over HTTPS, then you will need to select the DoH protocol. You will also notice in the figure, that there is a protocol called DoH-FIPS. This protocol is designed for use by organizations that want to use DNS over HTTPS, but that also need to maintain FIPS compliance. It is also worth noting that you can select multiple protocols if necessary.
The process for enabling DNS over HTTPS for an outbound endpoint is nearly identical to that of enabling the protocol for an inbound endpoint. Simply select the protocols that you want to use from the Protocols for this Endpoint drop down, as shown in Figure 2. As you look at the figure however, you will notice that the option for FIPS compliance is conspicuously absent.
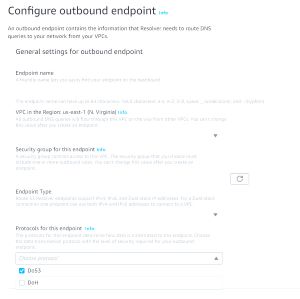 [Click on image for larger view.] Figure 2: To Enable DNS Over HTTPS for an Outbound Endpoint, Select the DoH Option from the Protocols for this Endpoint Drop Down.
[Click on image for larger view.] Figure 2: To Enable DNS Over HTTPS for an Outbound Endpoint, Select the DoH Option from the Protocols for this Endpoint Drop Down.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.