News
The Other Side of the BYOD Problem: Orgs Spying on Users
We are often warned of the dangers of bring-your-own-device (BYOD) policies in hybrid workforce scenarios: data leakage, exposure of sensitive information and so on. But what about the other side of that coin: organizations spying on workers through their personal devices?
"The big question, is the organization spying on that user? What rights does the user have? What rights does the organization have?" said Brian Posey, a freelance technology author and 22-time Microsoft MVP, in a recent presentation. "And I gotta tell you, when I was putting this presentation together, I came across some really eye-opening information."
That presentation is titled "The Security Do's and Don'ts with BYOD and Endpoint Management," and it's part of a half-day summit titled "Crash Course: Hybrid Workforce Security," which is now available for replay.
Posey discussed the spying issue while discussing various stakeholders in the BYOD security equation, including the organization's IT department, the end user, HR/legal and third parties including app publishers, web sites and so on.
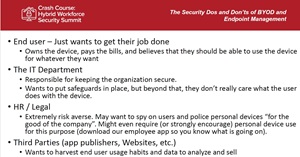 [Click on image for larger view.] BYOD Stakeholders (source: Brien Posey).
[Click on image for larger view.] BYOD Stakeholders (source: Brien Posey).
"And if there is spying going on through the end users' devices, it's very often the HR department or the legal department that is either doing it or has signed off on that," he said. "And sometimes this happens even if an end user isn't actually using their device for work. Because maybe a user hadn't actually gone through the trouble of enrolling their device in an MDM portal, and began running applications and accessing data. But how many situations have you seen where an organization has built their own app, and they've told their employees, 'Hey, we want you to install this app on your personal device so that you'll know what's going on?' Well, maybe that app is totally innocent, maybe it's exactly what it seems to be. Or maybe it contains some sort of mechanism that allows the organization to spy on the user, even though they aren't necessarily using that particular device for work. Just something to think about."
Later, in discussing device security, Posey revisited the spying issue.
"Also, it's worth noting that there are stories of employees being fired for uninstalling what amounts to spyware that was put on by the organizations that they work for," he said.
He recalled one instance involving a user who removed a company-installed GPS tracker, resulting in a lawsuit.
While he doesn't remember the outcome of the lawsuit, the case illustrates the fact that organizations will use mobile devices, particularly BYOD devices, to spy on their employees.
"So a few more things to consider," he said. "One -- and this is really important -- is make it clear what the user is agreeing to by using the device for work.
"So are you going to forcibly uninstall apps? Maybe there are certain applications that your IT team has deemed to be a security risk. And you don't want those apps running on the end users devices alongside work stuff. So maybe you've got a policy of looking for those particular apps and uninstalling them? If so that's fine, but that's something that you need to be super clear about with regard to telling your users upfront, so they'll know to expect that. And then they can opt out of using that device for work if that app is something that they depend on.
"Another thing to consider is that users need to know that their personal data could potentially be exposed, even if you're not spying on them or anything like that, should the organization become subject to litigation. Because if the organization is subject to litigation, then there may be a subpoena of that device and all of the data that's on it, including personal data."
In addition to his own experience and expertise, Posey pointed attendees to online resources to learn more about the issue, including "41 most asked questions on U.S. employee monitoring laws" from WorkTime and "How Your Boss Can Use Your Remote-Work Tools to Spy on You" from The New York Times.
Perhaps surprising to some attendees, that first source indicates (with caveats, special circumstances and other factors applying) that:
- Employers can monitor employees' personal devices
- Employers can monitor employees' personal computers
- Employers can require employees to install monitoring software on personal devices
- Employers can monitor screen contents and keystrokes
- Employers can track employee locations using GPS
- Employers can track a company car using GPS
Remember, none of those assertions are necessarily set in stone for all circumstances, with all kinds of considerations coming into play.
Points for organizations to consider, Posey said, include:
- Be transparent about what the company is and is not monitoring on personal devices. There are stories of employees being fired for personal messages on personal devices.
- There are also stories of employees being fired (and subsequently filing a lawsuit) for uninstalling what amounts to spyware installed by the organization.
- Users tend to be especially concerned about their web browsing history and personal messages.
- Make it clear what the user is agreeing to by using the device for work, such as the company forcibly removing apps or outlawing some apps.
- A user's personal data may be exposed if the organization be to litigation.
- A user can lose everything on the device (photos, messages, organization initiates a remote wipe (which has been known accident).
- BYOD laws can vary from one state to the next.
The spying issue was obviously important to attendees, as it came up again in the question-and-answer period following Posey's presentation.
Posey was asked if employers were required to tell employees about any BYOD monitoring.
He replied: "It really depends on what it is that they're trying to do. There are some things such as tracking an employee's location outside of work hours, that yes, they're required to tell them about. There are other types of monitoring that no, they're not required to tell them. At least, that's my understanding, based on reading all of those laws. Again, I'm not a lawyer or anything."
Another question was: "Is it super common for organizations to spy on users to their personal devices, essentially turning their own devices against them?"
"Yes, it is," Posey replied. "But I think the real question is, to what extent do they spy on the end users. And as a general rule, and again, nothing's ever absolute, but as a general rule, the larger the company, the more intrusive you can expect them to be. Oftentimes, the smaller companies either just don't have the resources to do really intricate device level spying. Or maybe they just don't even have the interest in doing that."
Another question asked: "What are some signs that an organization is spying on its employees through their personal devices?"
"Oh, that's a good question," Posey replied. "One of the signs would be Terms of Service, or Acceptable Use policies that are super long and written in a way that only a lawyer can understand it. In my mind that says that the organization has something to hide. But another thing that could be a sign is people within your organization knowing things that they shouldn't otherwise know. Maybe your boss dropped some little detail from something that was in a personal email that maybe they didn't even realize they said, but they shouldn't know that unless they've been reading your mail."
There's plenty more BYOD expertise beyond the spying issue that was shared in last week's half-day summit, which, again, is available for replay here.
Coming up, some more such events being held later this month by Virtualization & Cloud Review and sister sites include:
About the Author
David Ramel is an editor and writer at Converge 360.