News
Expert Details How to Harden Microsoft Identity Without Slowing Down Business
At today's free online summit produced by sister pub RedmondMag, titled "Crash Course: Identity and Access Management in AD/Entra ID," Microsoft Certified Solutions Master and former five-time MVP Nathan O'Bryan shared new ways IT pros can strengthen Microsoft 365 security without throttling user productivity.
His session was the second in a three-part summit, and he presented on "Hardening Identity Without Slowing Down Business." The entire summit is being made available for on-demand replay by the sponsor, Netwrix.
 "You really have to understand how your organization is using these features and roll out those Secure Score recommendations slowly, make sure that they're tested well. You can be too secure -- to the point where nobody can work."
"You really have to understand how your organization is using these features and roll out those Secure Score recommendations slowly, make sure that they're tested well. You can be too secure -- to the point where nobody can work."
Nathan O'Bryan, Microsoft Certified Solutions Master: Messaging, and five time former Microsoft MVP
The session focused on emerging features in Entra, Intune, and Conditional Access that enable fine-grained identity protection, administrative safeguards, and endpoint compliance.
"I've picked out six kind of new features/functionalities within Microsoft 365 that I'm going to talk about for you all here today," O'Bryan said. "They are all around identity and security." He covered six items, but his first and deepest segment--on geo-blocking access to SharePoint Online sites--set the foundation of his session.
Controlling Access by Geography
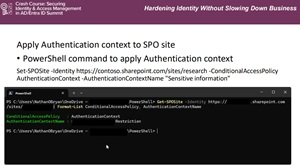 [Click on image for larger view.] Apply Authentication context to SPO Site (source: Nathan O'Bryan).
[Click on image for larger view.] Apply Authentication context to SPO Site (source: Nathan O'Bryan).
O'Bryan explained how Microsoft's Conditional Access platform now supports site-level control for SharePoint Online (SPO), allowing organizations to limit where users can access specific content--even if they otherwise have permission. "There are some new functionality within Conditional Access that's going to allow us to block access to specific SharePoint Online sites from specific locations, even if that user otherwise has permission to access that SharePoint site," he said.
He added that the system works in both directions. "You can use this same system to only allow access to specific SharePoint sites from specific locations," he explained. "If you have a specific SharePoint site that you only want people to access from, say, the office, you could use this same configuration to do that."
To build these controls, administrators start by creating an Authentication Context in Entra's Conditional Access portal. "All you have to put in is a name and a description," he said. "We're going to use that object to link a SharePoint Online site to a Conditional Access policy."
The next step is to define a Named Location--by country, IP range, or specific office network--and tie it to that Authentication Context. Then, through the Conditional Access Policy editor, admins can target a SharePoint resource and select the appropriate context. O'Bryan cautioned, "Be very careful with this. Don't include the account that you're using to set this up. You don't want to block yourself out."
Once the configuration is complete, the rule is applied to the SPO site via PowerShell using the Set-SPOSite command. "There is no GUI option for it currently," he said. "You'll want to use the Set SPO site commandlet, put in the SharePoint site that you want this to apply to, and then add the authentication context name." When working properly, blocked users receive a notice that their "sign-in was successful" but they "don't meet the criteria to access this resource."
O'Bryan noted that organizations might use this approach to meet compliance or regulatory requirements. "If there are specific geo locations that you don't want people to access a specific SharePoint site from, maybe your organization has export controls ... you don't want people to access a specific SharePoint site from China," he said. "Or again, you can use it in the reverse way, to ensure that people can only access a specific SharePoint site from the office or from specific locations like that."
Extending Conditional Access to Domain Controllers
 [Click on image for larger view.] Entra Private Access for Domain Controllers (source: Nathan O'Bryan).
[Click on image for larger view.] Entra Private Access for Domain Controllers (source: Nathan O'Bryan).
O'Bryan next highlighted a new hybrid security integration called Entra Private Access for Domain Controllers. "This is a brand new feature that will allow you to use Entra Conditional Access and Entra MFA on your Active Directory Domain Controllers on premises," he explained. "It installs a small agent on the domain controllers, and then it will intercept the Kerberos authentication process and inject Conditional Access and MFA from Entra."
He noted that the feature requires Microsoft's Global Secure Access licensing and said it could eventually increase adoption of that service. "I think that's a pretty powerful new feature," O'Bryan said. "Maybe the addition of this feature ... will encourage more organizations to use that feature."
Building Administrative Safeguards with Multi-Admin Approval
 [Click on image for larger view.] Apply Authentication context to SPO Site (source: Nathan O'Bryan).
[Click on image for larger view.] Apply Authentication context to SPO Site (source: Nathan O'Bryan).
O'Bryan also previewed what he believes is an early step in a broader shift across Microsoft 365 toward multi-party administrative controls. "This is a very new feature within Intune," he said. "Multi-Admin Approval showed up in Intune first, but I expect to see something like this working on more of the Microsoft 365 applications over time."
He explained that the feature requires a second administrator to approve certain protected changes before they take effect. "When an administrator makes those changes, it will just stage them, not actually import them into your environment," he said. "Then it will notify other administrators to approve that before the changes are applied." Covered resource types include app deployments, device actions like wipe or retire, role-based access control changes, and tenant configuration updates. "I think it's a really powerful tool," he concluded, adding that "we're going to see more of this across Microsoft 365 in general."
And More
Beyond the top identity-hardening features above, O'Bryan also discussed several related topics, including endpoint compliance checks in Intune and new remediation scripting techniques. The full session is available for replay through RedmondMag's webcast portal
While replays are convenient and informative -- especially up-to-date sessions that just concluded -- attending live events offers advantages, including the ability to ask specific implementation questions and receive guidance in real time (not to mention receive free prizes, in this instance a $300 Best Buy Gift Card provided by the sponsor, Netwrix, which also presented a session in the summit). With that in mind, here are some upcoming online summits and webcasts from RedmondMag:
About the Author
David Ramel is an editor and writer at Converge 360.