Vanover's Virtual Space
Advanced Virtual Conversion Flowchart
Procedural approach for conversions can aid conversions of any type.
- By Rick Vanover
- 06/30/2009
Recently, I had the privilege to be one of the presenters at TechMentor in Orlando. This year's TechMentor is a collection of two main categories, virtualizing and managing your IT environment. The virtualization track has an all-star list including Chris Wolf, Edward Haletky, Hal Rottenberg and others. During the show, Chris, Edward, Hal and I all agreed that one of TechMentor's strongest points is that it is not a sales pitch. We work hard to bring you relevant information from the field from all perspectives.
One session I gave was on advanced conversions for virtual environments. Today, this can include virtual-to-virtual conversions, as well as the traditional physical-to-virtual conversion. In the session, I had a lot of positive feedback for this flowchart resource. I encourage you to download it and customize it for your environment. This is based on real-world issues that I and others have gone through to assist you in any of your conversion adventures. This is more detail than you would need for the typical conversion, but is helpful when you have difficult systems that you haven't converted for any reason yet. In customizing the flowchart, go ahead and implement your specific site information, host or vCenter server characteristics, security requirements or location considerations.
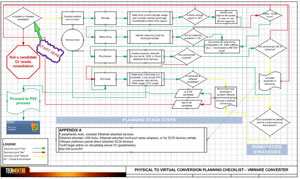 |
| Figure 1.This advanced P2V flowchart can aid you in your conversion processes. (Click on image to view larger version. Click here to download the Visio .vsd file; click here to download Visio Viewer.) |
This material is focused on converting physical machines to VMware virtual machines using vCenter Converter and uses Visio 2007.
One important point in the conversion process is to ensure that you are aware of the security zones you are using (or crossing) during a conversion. In the example of VMware conversions, the conversion process uses the service console on the host and the requisite connectivity is required to the host. Some network situations may require transient storage to make the conversion so that specified security zones are not crossed.
When it comes to conversions, new builds are always cleaner. But the use cases for conversions are still out there and an important part of the arsenal of today's virtual administrator.
About the Author
Rick Vanover (Cisco Champion, Microsoft MVP, VMware vExpert) is based in Columbus, Ohio. Vanover's experience includes systems administration and IT management, with virtualization, cloud and storage technologies being the central theme of his career recently. Follow him on Twitter @RickVanover.