How-To
How To Implement Mobile Application Management with Citrix XenMobile
Stepping through MAM is quick, easy. Here's how.
- By Natalie Lambert
- 08/07/2013
Consumer apps are quickly moving into the enterprise. Furthermore, enterprises are developing and adopting in-house mobile apps that change the way they do business. These apps range from productivity apps such as Evernote, QuickOffice, and Cisco Jabber to purpose-built ones to optimize the guest check-in process at restaurants, control the logistics of pilot scheduling at air freight companies or reduce customer wait times through quicker valet vehicle retrievals at luxury hotels. The mobile information management capabilities afforded by such enterprise apps are giving businesses new ways to take advantage of corporate data and achieve greater operational efficiencies.
The MDX mobile application management capabilities in Citrix XenMobile enable complete management, security and control over native mobile apps and their associated data. With MDX, corporate apps and data reside in a container, separated from personal apps and data on the user's mobile device. This allows IT to secure any custom developed, third-party or BYO mobile app with comprehensive policy-based controls, including mobile DLP and the ability to remote lock, wipe and encrypt apps and data.
Here's how it works:
App Wrapping
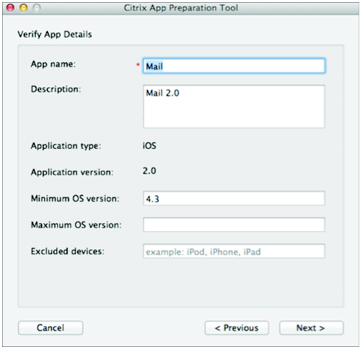
In order to add a native application to the list of applications managed by XenMobile, the application must be first prepared by the Citrix App Preparation Tool (see Fig. 1). This tool adds an application library wrapper that assists in applying managed policies. The native application is inputted as an .ipa file (or .apk for Android) and the resultant wrapped application is returned as a .cma file (“Citrix Mobile Application”). The .cma file contains the contents of the original .ipa, along with a manifest file that is used by XenMobile in the mobile app publishing workflow (i.e. when the prepared app is uploaded). The tool also allows entry of a few metadata fields, including a descriptive summary of the application and excluded device list.
 |
|
Figure 1. Citrix App Preparation Tool.
|
 |
|
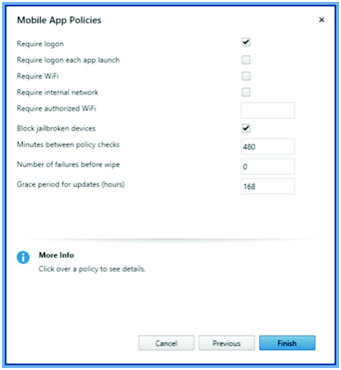
Figure 2. An application library wrapper assists in applying managed policies.
|
Enterprise Certificate
A key part of the preparation process is re-signing by a customer-provided enterprise distribution profile. This is a necessary step to ensure the integrity of the modified application and works with Apple's existing security restrictions.
XenMobile Distribution
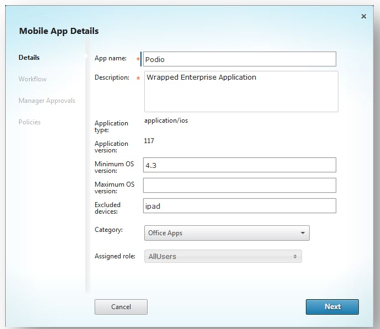
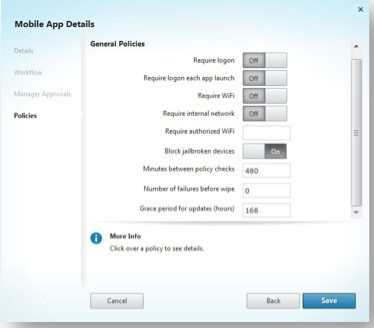
Once the application is wrapped and has the required enterprise certificate, it is now ready to be imported into XenMobile for distribution. As part of the distribution process, administrators can set the approved OS and devices an app can run on (see Fig. 3) as well as many different policies regarding the use of the app (see Fig. 4). Once policies are set, the application can be distributed down to mobile devices for local installation.
 |
|
Figure 3. Admins can approve OS and devices that the app will be able to run on.
|
 |
|
Figure 4. As well as devices, admins can set up security policies as well.
|
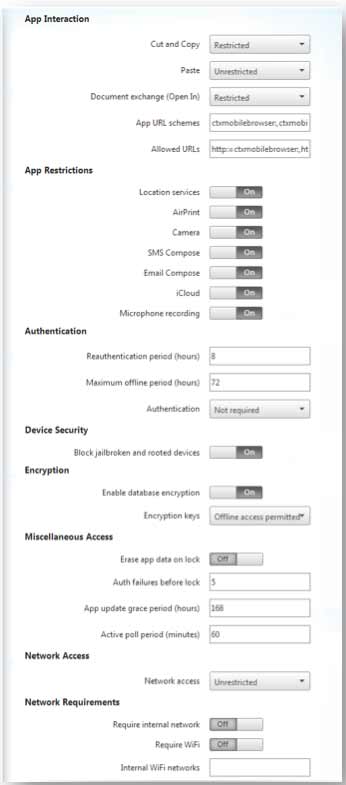
Table 1 shows just a sample of the types of policies that can be applied to an app and a few examples:
| Table 1. Policies that can be applied to apps, as shown in Fig. 5. |
| Policy |
Setting |
| App Interaction |
Cut and Copy: Blocks, permits, or restricts clipboard cut/copy operations for this application. When set to Restricted, the copied clipboard data is placed in a private clipboard that is only available to MDX apps.
Paste: Blocks, permits, or restricts clipboard paste operations for this application. When set to Restricted, the pasted clipboard data is sourced from a private clipboard that is only available to MDX applications.
|
| App Restrictions |
Location services: When set to On, this policy prevents an application from utilizing the location services components (GPS or network)
Camera: When set to On, this policy prevents an application from directly utilizing the camera hardware.
|
| Authentication |
Re-authentication period (hours): Defines the period before a user is challenged to authenticate again. If set to zero, the user is prompted for authentication each time app is started or activated.
Maximum offline period (hours): Defines the maximum period an application can run offline without requiring a network logon for the purpose of reconfirming entitlement and refreshing policies.
Device Security: Black jailbroken and rooted devices. When set to On, the application is locked when the device is jailbroken or rooted. If Off, the application can run even if the device is jailbroken or rooted.
|
| Encryption |
Enable database encryption: When set to On, this policy ensures that the data held in local database files is encrypted. When set to Off, the data held in local databases is not encrypted. |
| Miscellaneous Access |
Erase app data on lock: When set to On, when an application is locked, any persistent data maintained by the app is erased, effectively resetting the app to its just installed state. If Off, then application data is not erased when the app is locked. |
| Network Access |
Network Access: Prevents, permits or redirects application network activity. If "Unrestricted" is selected, no restrictions are placed on the network access. If "Blocked", all network access is blocked. If "Tunneled to the internal network" is selected, a per-application VPN tunnel back to the internal network is used for all network access. |
| Network Requirements |
Require internal network: When set to On, the app is allowed to run only from inside the company network. If Off, the app can run from an external network.
Require Wifi: When set to On, the app is locked when the device is not connected to a Wifi network. If Off, the app can run even if the device does not have an active Wifi connection such as 4G/3G or LAN connection.
|
|
|
 |
|
Figure 5. Setting policies.
|
App Use
Once the application is installed on the device, the application library wrapper we discussed above now intercepts key application events and applies the necessary policies created above before the app can be launched by the user. For example, when the application is first run, the wrapper will kick off the authentication process to make sure the end-user is entitled to app and then check to make sure the device is not jailbroken before allowing access.
These mobile application management capabilities are part of the MDX technologies delivered in XenMobile. MDX was designed to meet the needs of organizations that are pushing forward with their mobility initiatives as they will now have the tools they need to distribute mobile apps and enforce app policy on mobile devices. At Citrix, we believe these app policies are one of the keys to enabling secure mobility to employees who are bringing in their own mobile devices and require a way to be productive. If organizations can control the use of the app and the environments in which it can run, controlling the device no longer matters.