How-To
How To Access Group Policy Settings in an AWS Directory Service Environment
While not completely comprehensive, there are a number of different policy settings that are exposed through the Active Directory Administrative Center.
In many ways, working in an Amazon Web Services (AWS) Directory Service environment is similar to working with on-premises Active Directory. For instance, you can join EC2 instances to the directory service, and you can use tools such as the Active Directory Users and Computers console in basically the same way that you would normally use them. However, when it comes to Group Policy management, things work a little differently.
The reason why you can't manage Group Policy settings in the usual way is because, according to AWS, "In order to deliver a managed-service experience, AWS Microsoft AD must disallow operations by customers that would interfere with managing the service." This means that there are a few things that admins won't be able to do. This includes accessing the directory service from PowerShell, or performing any low-level administrative AD task that requires administrative privileges. You may have noticed that although the Directory Service environment is based on the use of EC2 instances that function as domain controllers, you don't actually get access to those instances. You may also have noticed that Directory Service administration is handled using an Admin account rather than the usual Administrator account. Both of these measures are related to the way in which AWS restricts low-level access to the Directory Service.
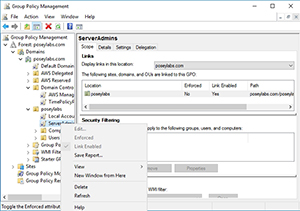
The problem with this, of course, is that domain-level Group Policy management is a low-level administrative activity. If you install the Group Policy Management Tool onto a domain-joined EC2 instance, you'll find that you're able to view the default Group Policy settings, but not modify them. As you can see in Figure 1, for example, the Edit option is grayed out.
 [Click on image for larger view.]
Figure 1. The Edit option for Group Policy objects is grayed out.
[Click on image for larger view.]
Figure 1. The Edit option for Group Policy objects is grayed out.
Thankfully, there's a partial workaround. From a domain-joined EC2 instance, open Server Manager and install the AD DS and AD LDS Tools. These tools are found among the Remote Administration Tools, and can be installed through the Features portion of the Add Roles and Features wizard. When you install the AD DS and AD LDS Tools, one of the tools that will be installed is the Active Directory Administration Center (AD AC). Go ahead and launch this tool by selecting the Active Directory Administrative Feature option from the Server Manager Tools menu.
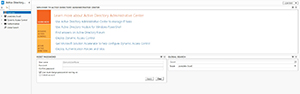
When the console opens, you'll find an icon in the upper-left portion of the display that allows you to switch the console to use Tree View. If you look at Figure 2, you can see what Tree View looks like. The Tree View icon is the icon that is located just above the Overview container.
 [Click on image for larger view.]
Figure 2. Switch the console into Tree View.
[Click on image for larger view.]
Figure 2. Switch the console into Tree View.
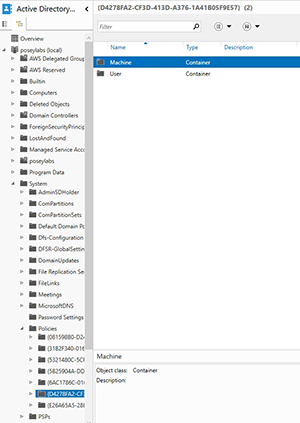
You can access various Group Policy settings by navigating through the console tree to | System. As you can see in Figure 3, there's a Policies container that stores several policies, each of which includes a Machine and a User container.
 [Click on image for larger view.]
Figure 3. Policy settings are scattered throughout the console tree.
[Click on image for larger view.]
Figure 3. Policy settings are scattered throughout the console tree.
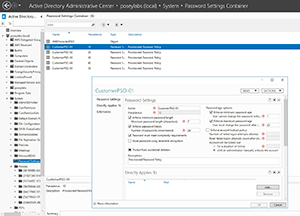
Typically, you'll find that the Machine and Users containers are empty. You may end up having to look elsewhere for specific policy settings. For example, if you're interested in modifying the password policy, then you can use the Password Settings container. You won't be able to modify the AWS protected password policy, but you can modify settings within higher-level policies. You can see an example of such a policy, and the password related settings within it, shown in Figure 4.
 [Click on image for larger view.]
Figure 4. This is where you go to modify password-related policy settings.
[Click on image for larger view.]
Figure 4. This is where you go to modify password-related policy settings.
Unfortunately, the native AWS Directory Service prevents you from using the Group Policy Object Editor to modify anything other than a local security policy. Even so, you'll find that while not completely comprehensive, there are a number of different policy settings that are exposed through the Active Directory Administrative Center. The trick is to simply take the time to explore this tool so that you can discover the policy settings that are available to you.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.