How-To
Tracking AWS Activities with CloudTrail, Part 1
While you can enable logging through EC2 instance guest OSes and through various other tools and applications running in the AWS cloud, you can also enable centralized logging through CloudTrail, which is designed to show you the administrative actions that have been performed across the various AWS services.
Audit logging has been an important part of IT since nearly the beginning. After all, it's impossible to keep the infrastructure secure if you don't know what the administrative staff is doing. Logging administrative activities is also a requirement for most regulatory compliance initiatives.
Not surprisingly, the AWS cloud gives organizations the tools needed to track administrative activities. While its true that you can enable logging through EC2 instance guest operating systems, and through various other tools and applications running in the AWS cloud, you can also enable centralized logging through CloudTrail.
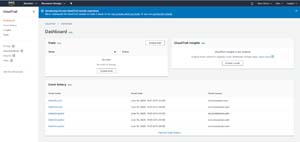
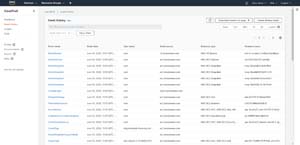
CloudTrail is designed to show you the administrative actions that have been performed across the various AWS services. If you look at Figure 1 for example, you can see that an S3 bucket was deleted within my organization. There were also several deletions made within EC2. Of course CloudTrail tracks more than just deletions. The deletions shown in the figure just happen to be the most recent administrative activities performed within my account. There is a link at the bottom of the event history that you can click in order to see the full event history. As you can see in the full event history shown in Figure 2, CloudTrail logs all of your AWS related administrative activities.
 [Click on image for larger view.]
Figure 1: The most recent administrative activities are shown on the CloudTrail Dashboard.
[Click on image for larger view.]
Figure 1: The most recent administrative activities are shown on the CloudTrail Dashboard.
 [Click on image for larger view.]
Figure 2: CloudTrail has logged a variety of administrative events.
[Click on image for larger view.]
Figure 2: CloudTrail has logged a variety of administrative events.
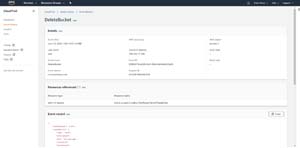
It is worth noting that the information that is shown in the screen capture above is just a summary of the recent administrative activities. If you want to examine a particular event in greater detail, just click on the event. When you do, you will be taken to a screen like the one that is shown in Figure 3. As you can see in the figure, AWS provides you with some additional details such as the AWS access key associated with the event, the event ID, the request ID, the region, and any error code that might have been returned.
 [Click on image for larger view.]
Figure 3: Clicking on an event causes the console to reveal additional details.
[Click on image for larger view.]
Figure 3: Clicking on an event causes the console to reveal additional details.
If you look at the very bottom of the figure above, you will notice the Event Record section. The Event Record section contains an even greater amount of detail about the event. For example, you can see the account ID, the user agent, and even the authentication method that was used.
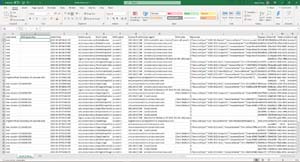
If you look back at Figure 2, you will notice that AWS provides an option to download the events either in CSV format or in JSON format. You can see a portion of a recently downloaded CSV file in Figure 4. I have cleared the AWS Access Key column's contents for security reasons, and there are some additional columns that extend beyond the screen boundaries, but the figure should at least give you a sense of the type of information that you can capture by creating a CSV or JSON file.
 [Click on image for larger view.]
Figure 4: You can download the logging data to a CSV file or to a JSON file.
[Click on image for larger view.]
Figure 4: You can download the logging data to a CSV file or to a JSON file.
The console also includes a filter that you can use to track down specific events. If you click on the filter, you are given the opportunity to filter events based on various event attributes such as Event ID, Event Name, User Name, AWS Access Key, Read Only, Event Source, Resource Name, and Resource Type (see Figure 5).
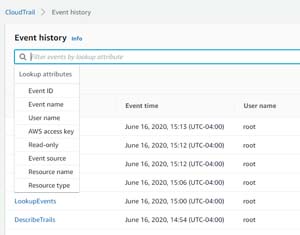 [Click on image for larger view.]
Figure 5: These are the filters that you can use to filter the event list.
[Click on image for larger view.]
Figure 5: These are the filters that you can use to filter the event list.
Imagine for example, that you wanted to see recent events related to AWS S3. To do so, you could click on the Event History filter, choose the Event Source option, and then choose S3.amazonaws.com from the list of sources. This causes the Event History page to display a detailed list of S3 related events that have occurred. As you look at Figure 6, you will notice that these events go well beyond the simple creating and deleting of buckets. Even relatively mundane events such as listing the available buckets is included on the list.
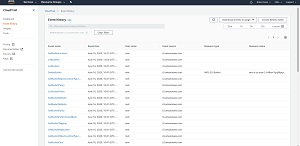 [Click on image for larger view.]
Figure 6: This list of events was filtered based on the Event Source (S3.amazonaws.com).
[Click on image for larger view.]
Figure 6: This list of events was filtered based on the Event Source (S3.amazonaws.com).
As you can see, CloudTrail is a useful tool for tracking the administrative activities that have occurred in your AWS environment. Even so, CloudTrail has two additional features that I want to discuss in Part 2 of this series.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.