News
Report Details COVID-19 Threat to Enterprise Cybersecurity
As if the enterprise cybersecurity situation wasn't bad enough already, it's worse amid the ongoing COVID-19 pandemic, says VMware Carbon Black's latest security threat report, which warns of overloaded security teams, a sea of distracted new remote workers exposing more vulnerabilities and new attack vectors to worry about.
"The fear and paranoia coursing through the world left organizations particularly vulnerable to cyberattacks -- which shot up by an estimated 66 percent" after the pandemic hit, says the fifth installment of VMware Carbon Black's semiannual Global Incident Response Threat Report.
Targeting enterprise incident response (IR) professionals, the report series seeks to provide a clearer picture of the evolving threat landscape along with actionable guidance to meet current and future challenges.
"COVID-19 has been accompanied by a surge in cyberattacks: more than half (53 percent) of all respondents encountered or observed an increase related to the pandemic," says the report, referencing a survey of 49 IR pros from around the world who were polled in April.
That finding jives with similar reports, such as a recent U.S. enterprise cybersecurity survey commissioned by VMware Carbon Black that found 89 percent of respondents were attacked by COVID-19-related malware.
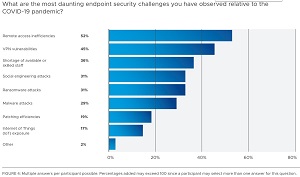 [Click on image for larger view.] Endpoint Security Threats (source: VMware Carbon Black).
[Click on image for larger view.] Endpoint Security Threats (source: VMware Carbon Black).
Highlights of the report as listed by the company include:
- With COVID-19 comes a surge in cyberattacks. Security teams are struggling to keep up. 53 percent of IR professionals we surveyed encountered or observed an increase in cyberattacks exploiting COVID-19. They pointed to remote access inefficiencies (52 percent), VPN vulnerabilities (45 percent) and staff shortages (36 percent) as the most daunting endpoint security challenges in this regard.
- Counter IR explodes as adversaries fight for persistent attacks on systems. A third of respondents (33 percent) encountered instances of attempted counter IR in the 90 days before they took our survey -- a 10 percent increase from our previous report. The forms of counter IR used -- mostly destruction of logs (50 percent) and diversion (44 percent) -- signal attackers' increasingly punitive nature and the rise of destructive attacks more broadly.
- The financial industry is under siege. More than half of attacks (51 percent) in the 90 days prior to this survey have been on the financial sector, followed by healthcare (35 percent), professional services (35 percent) and retail (31 percent). This correlates with the finding that 59 percent of those surveyed said attackers' end goal was financial gain -- by far the leading motivation.
- One in three attacks shows signs of lateral movement -- and as common tools like PowerShell bolster their defenses, this movement is being facilitated increasingly by the misuse of WMI, Google Drive and process hollowing. Cyberthreats from China are increasing. Over half of respondents (51 percent) saw attacks from China in the 90 days before this survey was held, followed by North America (40 percent) and Russia (38 percent). As Kellermann notes, “The Chinese have exhibited a dramatic evolution in operational security and attack sophistication. It can now be argued that their cyber capabilities rival those of Russia.”
The report also lists five steps for organizations to take in order to fight back, summarized thusly:
- Gain better visibility into system endpoints
- Establish digital distancing practices
- Enable real-time updates, policies and configurations across the network
- Remember to communicate
- Enhance collaboration between IT and security teams -- and make IT teams more cybersecurity savvy
"As the initial shock of COVID-19 subsides, we should expect organizations to firm up their defenses against new vulnerabilities -- whether it's addressing staff shortages, integrating endpoint technologies, aligning IT and security teams or adapting networks and employees to remote work," the report said.
About the Author
David Ramel is an editor and writer at Converge 360.