News
Microsoft Backs Zero Trust Security Model to Combat Ransomware, Invests in Rubrik
Microsoft is increasingly banking on the Zero Trust security model to combat an exploding ransomware threat.
To that end, the Redmond, Wash., software giant has invested in Zero Trust specialist Rubrik, which describes itself as a Zero Trust data management company, with the goal of delivering integrated Zero Trust data protection solutions built on the Microsoft Azure cloud.
Zero Trust is emerging along with best practice techniques like regular system backups and using Multi-factor Authentication (MFA) in the fight against ransomware, which is regularly making headline news as one attack (and corresponding ransom payout) after another are reported. In fact, Rubrik says, ransomware attacks have jumped by 700 percent in 2021 after growing 150 percent annually.
Zero Trust eschews the standard security approach of walling off networks and systems behind a secure perimeter. It's one of the latest security darlings in an industry that has seen the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, ZT assumes that such fortress security approaches are destined to fail and that systems have already been penetrated, seeking to lessen the damage that can be caused.
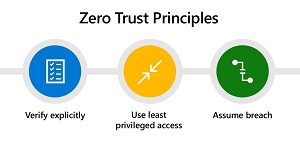 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
Microsoft says tools used to drive Zero Trust implementations include:
- Strong authentication. Ensure strong Multi-factor Authentication and session risk detection as the backbone of your access strategy to minimize the risk of identity compromise.
- Policy-based adaptive access. Define acceptable access policies for your resources and enforce them with a consistent security policy engine that provides both governance and insight into variances.
- Micro-segmentation. Move beyond simple centralized network-based perimeter to comprehensive and distributed segmentation using software-defined micro-perimeters.
- Automation. Invest in automated alerting and remediation to reduce your mean time to respond (MTTR) to attacks.
- Intelligence and AI. Utilize cloud intelligence and all available signals to detect and respond to access anomalies in real time.
- Data classification and protection. Discover, classify, protect, and monitor sensitive data to minimize exposure from malicious or accidental exfiltration.
"The evidence is clear -- the old security paradigm of building an impenetrable fortress around your resources and data is simply not viable against today's challenges," Microsoft says. "Remote and hybrid work realities mean people move fluidly between work and personal lives, across multiple devices, and with increased collaboration both inside and outside of organizational boundaries. Entry points for attacks -- identities, devices, apps, networks, infrastructure, and data -- live outside the protections of traditional perimeters. The modern digital estate is distributed, diverse, and complex."
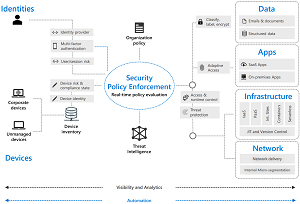 [Click on image for larger view.] Zero Trust Model (source: Microsoft).
[Click on image for larger view.] Zero Trust Model (source: Microsoft).
Meanwhile Rubrik, an early Zero Trust advocate, says:
The Zero Trust (ZT) model of security is showing a great deal of promise.... While Zero Trust has traditionally been used as a network security model, the principles also apply to data security and security architecture in general. ZT extends the principle of "least privilege" to its ultimate conclusion: Trust no one and grant the least privilege, so that once a user's identity is verified, they only get access for the role they're assigned -- nothing more. It is the opposite of the prevailing "trust but verify" model of access control that allows users with basic credentials to have broad access to digital assets. Instead, ZT takes a "verify but trust" approach that closes off access until the user's identity is confirmed, and then only grants the minimal access privileges to complete the assigned task.
The just-announced strategic agreement between the two companies sees Microsoft investing in Rubrik in a deal said by Bloomberg to total in the low tens of millions. The pact is meant to provide Zero Trust data protection in hybrid cloud environments that span datacenters, edge and cloud, specifically protecting flagship softwares like Microsoft 365.
"Customers, across industries, are migrating to the cloud to drive business transformation and realize growth," said Microsoft exec Nick Parker. "End-to-end application and data management is critical to business success, and we believe that integrating Rubrik's Zero Trust Data Management solutions with Microsoft Azure and Microsoft 365 will make it easy for customers to advance their Zero Trust journey and increase their digital resilience."
The new Rubrik pact reflects just one recent Zero Trust initiative from Microsoft. On the same day the Rubrik deal was announced (Aug. 17), Microsoft also announced it's collaborating with the National Institute of Standards and Technology (NIST) to use Zero Trust in addressing a Presidential Executive Order to improve U.S. cybersecurity. NIST publishes principles of Zero Trust for enterprises interacting with data.
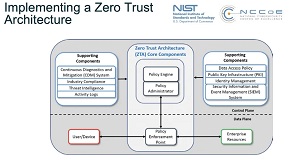 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
NIST and other agencies were chartered to create the cybersecurity standards and requirements outlined in Executive Order 14028, which was issued in May. "Microsoft is working with NIST's National Cybersecurity Center of Excellence (NCCoE) on the Implementing a Zero Trust Architecture Project to develop practical, interoperable approaches to designing and building Zero Trust architectures that align with the tenets and principles documented in NIST SP 800-207, Zero Trust Architecture, Microsoft said. "The NCCoE public-private partnership applies standards and best practices to develop modular, easily adaptable examples of cybersecurity solutions by using commercially available technology."
About the Author
David Ramel is an editor and writer at Converge 360.