News
A New Ransomware Threat: Compromised Identities
Cloud security specialist Ermetic published research that found compromised identities can lead to risky AWS S3 storage buckets in certain situations, resulting in ransomware vulnerabilities.
The AWS cloud many years ago was plagued by user-misconfigured, wide-open S3 buckets that led to expensive and highly publicized data breaches, leading security companies to probe for weaknesses and then trumpet their findings, which seemed to happen at least every single month.
However, that problem was finally solved, mostly, and Ermetic's research -- AWS S3 Ransomware Exposure in the Wild -- only investigated combinations of specific situations that could result in vulnerabilities. The company used its analytics engine to probe real environments in order to identify dangerous scenarios that included all of these factors:
- An identity has a permissions combination that enables it to perform ransomware
- Proper mitigation features are not enabled on the S3 buckets to which the identity has access
- The identity is exposed to one or more additional risk factors that could lead to compromise, such as public exposure to the internet
The three AWS bucket mechanisms that can help mitigate the identified attack vectors include:
- MFA Delete: AWS helps make the task of permanently deleting an object extremely difficult by enabling you to require that the bucket owner "include two forms of authentication in any request to delete a version or change the versioning state of the bucket."
- Object Locking: Simply put, object locks store objects in a Write-Once-Read-Many (WORM).
- Bucket Versioning: AWS offers a versioning mechanism that allows you to configure a bucket to maintain versions of the objects stored in it. When a bucket has versioning enabled, a deleted/written over object will not be removed permanently; rather, the bucket retains the old version of the object and simply presents/serves the new object version.
The study from Ermetic -- which offers an "identity-first security solution" -- found a lot of situations that fit the bill. In fact, more than 70 percent of the environments in the study included publicly exposed machines that were linked to identities whose permissions could be exploited to enable the machines to perform ransomware.
"Very few companies are aware that data stored in cloud infrastructures like AWS is at risk from ransomware attacks, so we conducted this research to investigate how often the right conditions exist for Amazon S3 buckets to be compromised," said Shai Morag, CEO of Ermetic. "We found that in every single account we tested, nearly all of an organization's S3 buckets were vulnerable to ransomware. Therefore, we can conclude that it's not a matter of if, but when, a major ransomware attack on AWS will occur."
The report also details various attack execution vectors, including: access and destroy; resource-based policy denial of service for KMS keys; and bucket privilege escalation via access control lists (ACLs); bucket privilege escalation via bucket policy; and privilege escalation to admin.
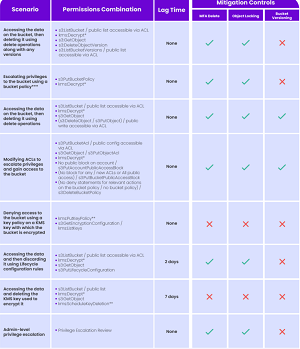 [Click on image for larger view.] Summarizing S3 Attack Methods and Scenario Factors
(source: Ermetic).
[Click on image for larger view.] Summarizing S3 Attack Methods and Scenario Factors
(source: Ermetic).
The above graphic summarizes the S3 attack methods discussed discussed in the report, the toxic permissions combinations required to implement them, if an attack has a lag time and if using MFA delete, object locking or bucket versioning would be effective mitigating actions.
Specific key findings of the report include:
- Overall, in every enterprise environment sampled, we found identities with a risk factor as well as permissions that enabled them to perform ransomware on at least 90 percent of the buckets in an AWS account
- Over 70 percent of environments had machines publicly exposed to the internet that were linked to identities whose permissions could be exploited to allow the machines to perform ransomware
- Over 45 percent of environments had third-party identities with the ability to perform ransomware by elevating their privileges to admin level (an astounding finding with potentially harmful implications far beyond ransomware that we will explore another time
- Almost 80 percent of environments had Identity and Access Management (IAM) users with enabled access keys that had not been used for 180 days or more and that had permissions that enabled them to perform ransomware
- Almost 60 percent of environments had IAM users that had the risk factor of console access without a requirement for MFA at login and that had permissions that enabled them to perform ransomware
And to address those findings, Ermetic offered up the following list of mitigation steps that organizations can take to reduce the exposure of their AWS S3 buckets to ransomware:
- Implement Least Privilege: enforce a permission strategy that only allows the bare minimum of entitlements necessary for identities to perform their business function, which will dramatically reduce the exposure of buckets to ransomware
- Eliminate Risk Factors: apply best practices to avoid/remove common misconfigurations that can be exploited by ransomware to compromise identities and use their entitlements to execute malware
- Use Logging and Monitoring: use tools such as CloudTrail and CloudWatch to identify sensitive actions which can provide early detection and response if a ransomware attack in is progress
Delete Prevention: use existing out-of-the-box features and configurations available for S3 buckets such as MFA-Delete or Object Locks to prevent malicious deletions
- Bucket Replication: configure sensitive buckets to automatically back up their contents to a separate, secure and dedicated bucket for restore
"It's important to note that these findings focus on single, compromised identities," the company said. "In many ransomware campaigns, bad actors often move laterally to compromise multiple identities and use their combined permissions, greatly increasing their ability to access resources."
About the Author
David Ramel is an editor and writer at Converge 360.