News
Microsoft: Russian Nation-State Actor Behind SolarWinds Attack Changes Tactics
Microsoft blamed Russia for new attacks against U.S. supply chain infrastructure, saying the Russia-backed nation-state actor Nobelium has changed its tactics this time.
Those tactics last year resulted in the highly publicized SolarWinds attack, of which Wikipedia says: "The attackers accessed the build system belonging to the software company SolarWinds, possibly via SolarWinds's Microsoft Office 365 account, which had also been compromised at some point." Officials and experts have clearly stated that Russia backs the hacker group.
Microsoft pulled no punches in placing blame in announcing the renewed supply chain attacks, saying Nobelium has been "identified as being part of Russia's foreign intelligence service known as the SVR."
The company said it first noticed the new campaign in May, this time focusing on a different part of the supply chain: resellers and technology service providers. Microsoft warned more than 140 targets but believes at least 14 of those targets have been compromised. Furthermore, the new attacks are part of a larger summer wave the company noticed, which prompted warnings to more than 600 customers. Microsoft believes the Russian government is trying to set up surveillance of important supply chain targets.
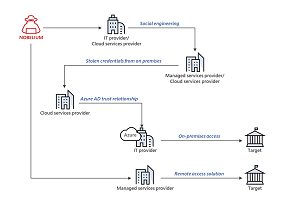 [Click on image for larger view.] Example Intrusion Conducted by NOBELIUM Demonstrating Nested Access Across Variety of Methods (source: Microsoft).
[Click on image for larger view.] Example Intrusion Conducted by NOBELIUM Demonstrating Nested Access Across Variety of Methods (source: Microsoft).
While the Russia-backed Nobelium has switched gears to target different supply chain components, it's using the same well-known attack techniques -- password spray and phishing -- that enabled the theft of legitimate credentials in order to gain privileged access.
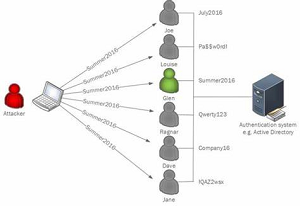 [Click on image for larger view.] Password Spray Using One Password Across Multiple Accounts (source: Microsoft).
[Click on image for larger view.] Password Spray Using One Password Across Multiple Accounts (source: Microsoft).
"We believe Nobelium ultimately hopes to piggyback on any direct access that resellers may have to their customers' IT systems and more easily impersonate an organization's trusted technology partner to gain access to their downstream customers," Microsoft said in an Oct. 24 post.
It further said it has been working with the security community and U.S. and European agencies on the matter, which is difficult to combat in view of who's behind it. "While we are clear-eyed that nation-states, including Russia, will not stop attacks like these overnight, we believe steps like the cybersecurity executive order in the U.S., and the greater coordination and information sharing we've seen between industry and government in the past two years, have put us all in a much better position to defend against them."
To help, the company published technical guidance (NOBELIUM targeting delegated administrative privileges to facilitate broader attacks) and Guidance for partners on Nobelium targeted attacks.
As for itself, Microsoft said it has been working on these improvements:
- As noted above, in September 2020, we rolled out MFA to access Partner Center and to use delegated administrative privilege (DAP) to manage a customer environment
- On October 15, we launched a program to provide two years of an Azure Active Directory Premium plan for free that provides extended access to additional premium features to strengthen security controls
- Microsoft threat protection and security operations tools such as Microsoft Cloud App Security (MCAS), M365 Defender, Azure Defender and Azure Sentinel have added detections to help organizations identify and respond to these attacks
- We are currently piloting new and more granular features for organizations that want to provide privileged access to resellers
- We are piloting improved monitoring to empower partners and customers to manage and audit their delegated privileged accounts and remove unnecessary authority
- We are auditing unused privileged accounts and working with partners to assess and remove unnecessary privilege and access
The company's recently published Microsoft Digital Defense Report highlights continued attacks from other nation-state actors and cybercriminals.
About the Author
David Ramel is an editor and writer at Converge 360.