News
Survey Shows Limits of Ransomware Insurance, Payoffs
A new report from data protection specialist Veeam shows the limits of ransomware insurance and payoffs.
Specifically, the company's 2022 Ransomware Trends Report found that many victimized organizations paid ransoms and recovered their data. However, nearly as many either recovered their data without paying the ransom or paid the ransom and still didn't recover their data.
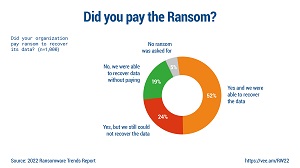 [Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
[Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
"One of the more notable statistics in the survey is that half (52 percent) of those with encrypted data paid the ransom and were successful in recovery," Veeam said. "However, one in four organizations paid the ransom but were still unable to recover their data, while nearly as many were able to recover without paying a ransom.
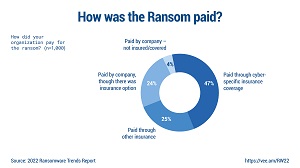 [Click on image for larger view.] How Was Ransom Paid? (source: Veeam).
[Click on image for larger view.] How Was Ransom Paid? (source: Veeam).
"This final element is why data protection companies are so focused on ransomware scenarios. That said, when ransoms were paid, the majority (72 percent) of organizations used some form of insurance. Beating ransomware by utilizing insurance could be harder for organizations moving forward, based on how they responded when asked about cyber insurance:
- 57 percent have cyber insurance that includes ransomware coverage
- 30 percent have cyber insurance, but ransomware is excluded from coverage
- 13 percent do not have cyber insurance
Those findings led Danny Allan, CTO at Veeam, to conclude that paying the ransom is not the way to go. "Ransomware has democratized data theft and requires a collaborative doubling down from organizations across every industry to maximize their ability to remediate and recover without paying the ransom," Allan said. "Paying cybercriminals to restore data is not a data protection strategy. There is no guarantee of recovering data, the risks of reputational damage and loss of customer confidence are high, and most importantly, this feeds a self-fulfilling prophecy that rewards criminal activity."
Indeed, Allan's point about reputational damage and loss of customer confidence was echoed in another report by Forrester Research, as explained in the Virtualization & Cloud Review article "Cybersecurity Incident Responders Help 'Rebuild Trust' After Attack."
"Initiating incident response actions is often just the beginning of a protracted effort to rebuild brand and reputation," Forrester said in that report. "The work of rebuilding trust -- with customers, employees, partners, insurers and regulators -- begins in earnest after an organization recovers operations post-breach."
Veeam's report jives with that observation, noting that remediation takes longer than organizations might think.
"While many organizations were able to start their remediation activities in the same or following day, those respondents cited that their recovery journey took (on average) 18 days to complete," Veeam said. "This is presumably due to not only the scale issues of addressing what was affected, but also the necessary diligence to confirm that restored systems were 'clean' before being put back into production."
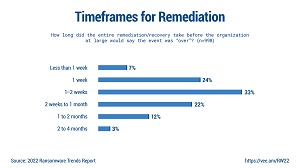 [Click on image for larger view.] Remediation Timeframes (source: Veeam).
[Click on image for larger view.] Remediation Timeframes (source: Veeam).
The Veeam report covers ransomware pervasivenes, remediation methods, immutability/air gap, organizational alignment and more.
Other key findings from the report as presented by the company include:
- Orchestration matters: To proactively ensure recoverability of their systems, one in six (16 percent) IT teams automate the validation and recoverability of their backups to ensure their servers are restorable. Then, during remediation of a ransomware attack, 46 percent of respondents use an isolated “sandbox" or staging/test area to ensure their restored data is clean prior to reintroducing the systems into production.
- Organization alignment must unify: 81 percent believe their organizations' cyber and business continuity/disaster recovery strategies are aligned. However, 52 percent of respondents believe the interactions between these teams requires improvement.
- Diversifying the repositories holds the key: Nearly all (95 percent) organizations have at least one immutable or air-gapped data protection tier, 74 percent use cloud repositories that offer immutability; 67 percent use on-premises disk repositories with immutability or locking; and 22 percent use tape that is air-gapped. Immutable or not, organizations noted that in addition to disk repositories, 45 percent of production data is still stored on tape and 62 percent goes into a cloud at some point in their data lifecycle.
As far as methodology of the report, Veeam commissioned independent market research company, Vanson Bourne, to conduct a survey of 1,000 unbiased IT leaders regarding the impact of ransomware within their environments, as well as their IT strategies and data protection initiatives moving forward. Respondents represented organizations of all sizes from 16 different countries in APJ, EMEA and the Americas.
About the Author
David Ramel is an editor and writer at Converge 360.