News
Gartner Predicts Big Zero Trust Uptake, but Most Won't Benefit
Research firm Gartner Inc. this week published eight cybersecurity predictions for the next few years, with Zero Trust figuring prominently.
The company predicted it will be widely embraced in the next few years, but most organizations won't realize full benefits because the approach requires a cultural shift in thinking and communication. Gartner said adopting organizations should "communicate business relevance of ZT by aligning resilience and agility."
Zero Trust eschews the standard security approach of walling off IT systems behind a secure network perimeter. It has grown in popularity with the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, Zero Trust assumes that such fortress security approaches will fail or have already been penetrated, seeking to lessen the damage that can be caused.
Gartner has said the term Zero Trust "is useful as a shorthand way of describing an approach where implicit trust is removed from all computing infrastructure. Instead, trust levels are explicitly and continuously calculated and adapted to allow just-in-time, just-enough access to enterprise resources." Gartner analyst Neil MacDonald has also said, "Zero trust is a way of thinking, not a specific technology or architecture. It's really about zero implicit trust, as that's what we want to get rid of."
 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
The Zero Trust prediction and others were made during a Security & Risk Management Summit held this week in Australia.
"60 percent of organizations will embrace Zero Trust as a starting point for security by 2025," Gartner said in a June 21 news release about the summit. "More than half will fail to realize the benefits. The term zero trust is now prevalent in security vendor marketing and in security guidance from governments. As a mindset -- replacing implicit trust with identity- and context-based risk appropriate trust -- it is extremely powerful. However, as zero trust is both a security principle and an organizational vision, it requires a cultural shift and clear communication that ties it to business outcomes to achieve the benefits."
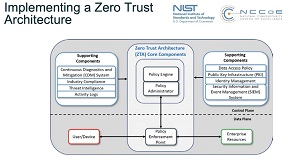 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
In a market guide, Gartner has listed many such benefits:
- When replacing legacy network-level VPN access, ZTNA [Zero Trust Network Access] provides contextual, risk-based and least privilege access to applications (not networks).
- When replacing applications exposed in DMZs with ZTNA, services are no longer visible on the public internet and are thus shielded from attackers.
- ZTNA brings significant benefits in user experience, agility, adaptability and ease of policy management.
- For cloud-based ZTNA offerings, scalability and ease of adoption are additional benefits.
- ZTNA enables digital business transformation scenarios that are ill-suited to legacy access approaches.
As noted, though, organizations will have to change things up to realize all of the above benefits and many others.
In its market guide, Gartner also made some recommendations that should be followed by security and risk management leaders responsible for infrastructure security:
- Establish a high-level zero trust strategy first and ensure that your identity and access management technologies and processes are well understood and mature before selecting and implementing a ZTNA solution.
- Assess your current VPN landscape if VPN replacement is the primary goal to quantify the capabilities of a ZTNA vendor -- and if there are sufficient benefits of implementing ZTNA to replace the VPN.
- Consolidate agent-based ZTNA selection with the choice of SSE provider as part of the wider SASE architecture decisions to avoid the complexity and potentially unsupported configurations of multiple agents on managed devices.
- Prioritize ZTNA vendor selection based on the desired end-user access use cases, as well as the endpoint and application architecture of the organization.
The firm's other seven predictions made this week include:
- Through 2023, government regulations requiring organizations to provide consumer privacy rights will cover 5 billion citizens and more than 70 percent of global GDP
- By 2025, 80 percent of enterprises will adopt a strategy to unify web, cloud services and private application access from a single vendor's SSE platform
- By 2025, 60 percent of organizations will use cybersecurity risk as a primary determinant in conducting third-party transactions and business engagements
- Through 2025, 30 percent of nation states will pass legislation that regulates ransomware payments, fines and negotiations, up from less than 1 percent in 2021
- By 2025, threat actors will have weaponized operational technology environments successfully to cause human casualties
- By 2025, 70 percent of CEOs will mandate a culture of organizational resilience to survive coinciding threats from cybercrime, severe weather events, civil unrest and political instabilities
- By 2026, 50 percent of C-level executives will have performance requirements related to risk built into their employment contracts
Gartner said cybersecurity leaders should build the predictions -- or "strategic planning assumptions" -- into their security strategies for the next two years.
"We can't fall into old habits and try to treat everything the same as we did in the past," said analyst Richard Addiscott in the summit keynote. "Most security and risk leaders now recognize that major disruption is only one crisis away. We can't control it, but we can evolve our thinking, our philosophy, our program and our architecture."
About the Author
David Ramel is an editor and writer at Converge 360.