News
'Confidential Computing' Specialist Open Sources Runtime-Encrypted Kubernetes
Edgeless Systems, which believes "confidential computing" is the future of cloud computing, attested to that belief by open sourcing an encrypted Kubernetes offering.
Called Constellation, the new GitHub-based open source project is described as "Always Encrypted Kubernetes."
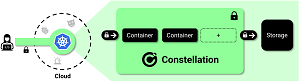 [Click on image for larger view.] Constellation (source: Edgeless Systems).
[Click on image for larger view.] Constellation (source: Edgeless Systems).
The GitHub README.md file says: "Constellation is a Kubernetes engine that aims to provide the best possible data security. It wraps your K8s cluster into a single confidential context that is shielded from the underlying cloud infrastructure. Everything inside is always encrypted, including at runtime in memory. For this, Constellation leverages confidential computing (see the whitepaper) and more specifically Confidential VMs."
That whitepaper published by the Germany-based cybersecurity startup explains its take on confidential computing: "Confidential computing is a technology that shields computer workloads from their environments and keeps data encrypted even during processing. The vast and previously unsolved problem that confidential computing addresses is the following: How to process data on a computer that is potentially compromised? This computer could be operated by yourself, your company, or a third party like a cloud provider." (For Microsoft's take on confidential computing, read Paul Schnackenburg's Virtualization & Cloud Review article "A Look at Azure Confidential Computing.")
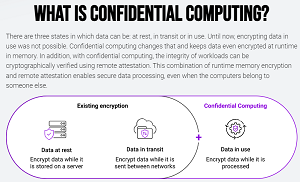 [Click on image for larger view.] Confidential Computing (source: Edgeless Systems).
[Click on image for larger view.] Confidential Computing (source: Edgeless Systems).
As far as those "Confidential VMs," they are explained in a Sept. 13 blog post: "Shortly put, with Constellation, all your nodes run inside Confidential Virtual Machines, enabling encryption during processing. In addition, Constellation automatically encrypts all data that is sent over the network or written to storage. The integrity of the nodes is verified by Constellation through a process of attestation, where only 'good' nodes, meaning the ones that are running a signed Constellation image and are in the expected state, get the cryptographic keys required to access the network and storage of a cluster."
While the company says Constellation works on all major clouds, specific documentation shows that support depends on the varying degrees to which Google Cloud Platform (GCP), Amazon Web Services (AWS) and Microsoft Azure support Confidential VMs (CVMs), with the latter platform said to provide "the best foundations for Constellation."
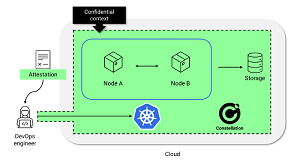 [Click on image for larger view.] Constellation's Confidential Context (source: Edgeless Systems).
[Click on image for larger view.] Constellation's Confidential Context (source: Edgeless Systems).
Security features of the approach, the company said, include:
- Runtime encryption: Constellation runs all Kubernetes nodes inside CVMs. This gives runtime encryption for the entire cluster.
-
Network and storage encryption: Constellation augments this with transparent encryption of the network and persistent storage. Thus, workloads and control plane are truly end-to-end encrypted: at rest, in transit, and at runtime.
- Transparent key management: Constellation manages the corresponding cryptographic keys inside CVMs.
- Node attestation & verification: Constellation verifies the integrity of each new CVM-based node using remote attestation. Only "good" nodes receive the cryptographic keys required to access the network and storage of a cluster.
- Confidential computing-optimized images: A node is "good" if it's running a signed Constellation node image inside a CVM and is in the expected state. (Node images are hardware-measured during boot and are reflected. The measurements are reflected in the attestation statements that are produced by nodes and verified by Constellation.)
- "Whole cluster" attestation: Towards the DevOps engineer, Constellation provides a single hardware-rooted certificate from which all of the above can be verified.
"Edgeless Systems is building the open source infrastructure for the Confidential Computing revolution," said company CEO Felix Schuster in a Sept. 13 news release. "The hardware and features required for Constellation mostly weren't even available in the cloud 12 months ago, but we started the necessary work to ensure Kubernetes users can secure all their data -- in rest, in transit and now in use. By making Constellation available to everyone, we can help accelerate the adoption of more secure cloud computing workloads."
About the Author
David Ramel is an editor and writer at Converge 360.