News
Cloud Security Alliance Sheds Light on 'Shadow Access' IAM Problem
The Cloud Security Alliance is talking up a new security concern for IT pros to worry about, "Shadow Access," or the unintended access to organizational applications and data.
"The consequences of Shadow Access are massive and threaten to impact any organization that has an evolving cloud," the nonprofit CSA said this week in announcing its new report, "Defining Shadow Access: The Emerging IAM Security Challenge."
The CSA boasts more than 90,000 individual members and 500 corporate members that constitute a who's who of important cloud vendors, including cloud giants AWS, Google and Microsoft. The organization said the new document was published to summarize the background, causes, impact and path forward to regain the benefits of a dynamic and secure cloud environment.
As far as that definition mentioned in the title: "Shadow Access is the unintended and/or undesired access to resources, such as applications, networks and data. This new problem has arisen with the growth of cloud computing, DevOps velocity, cloud native architectures and data sharing."
And, as that title indicates, it's an Identity and Access Management (IAM) issue, or rather the new concept of "Cloud IAM" that arrived along with cloud computing itself. CSA notes that Cloud IAM is now used to provision and control access and entitlements to resources, applications and data that reside in public clouds like AWS, Google Cloud and Azure Cloud, along with private clouds powered by Kubernetes.
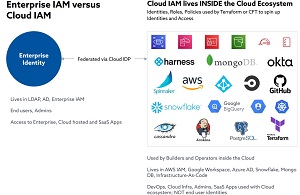 [Click on image for larger view.] Enterprise IAM vs. Cloud IAM (source: Cloud Security Alliance).
[Click on image for larger view.] Enterprise IAM vs. Cloud IAM (source: Cloud Security Alliance).
"Shadow Access is increasingly a cloud issue, resulting from increased use of access and entitlements that connect cloud services together, coupled with automated infrastructure and software development, resulting in incorrectly or unexpectedly permissioned accounts and resources," the report said. "Organizations from small to large often find out the hard way that what was once a secure starting point has silently evolved into an unsecure one. The above problem, combined with the common practice of cloning accounts and permissions (typically during onboarding or account creation) have multiplied the shadow access problem by providing access that is not truly not required."
After defining and explaining the problem in the specific context of the cloud, the CSA listed its impacts:
- Existing tools are blind to the multitude of cloud identities and access pathways.
- Governance and visibility gaps make it very difficult to implement IAM guard rails.
- Unrecognized access pathways allow vulnerabilities to be exploited to breach cloud data.
- Threat actors can weaponize programmable access to cause harm far beyond breach of data.
- Third-party and SaaS Applications that connect to cloud ecosystems introduce lateral movement risks.
- The existence of Shadow Access creates data security, audit and compliance exposures and creates policy and governance gaps.
As far as how organizations can address the Shadow Access problem, the CSA said ... nothing. That will apparently come in subsequent reports that might go beyond a definition and explanations of how the problem arose.
"The work on understanding Shadow Access is just beginning," the CSA said. "The broader trends of automation, AI, and data creates a fertile environment for Shadow Access to thrive. It impacts just not access, but also broader aspects, such as Zero Trust. The relationship between Shadow Access and Zero Trust and many other areas will be discussed in more detail in future documents."
About the Author
David Ramel is an editor and writer at Converge 360.