News
Cloud Firms Team Up to Fight Record-Breaking DDoS Attacks
Major industry players including cloud giants Google and Amazon Web Services (AWS) yesterday publicized an ongoing series of distributed denial-of-service (DDoS) attacks that are increasing in size and frequency.
Such brute-force attacks seek to flood internet servers and networks with HTTP traffic to interrupt services. The wave of attacks using a new technique involving the HTTP/2 protocol has resulted in cloud infrastructure companies fighting off the largest DDoS attacks ever recorded while maintaining their cloud/internet services.
Google is at the forefront of the DDoS wars, noting in a blog post yesterday that the firm last year blocked the largest DDoS attack yet recorded, only to stop a much larger attack a couple months ago, 7-1/2 times larger than the previous record.
"This new series of DDoS attacks reached a peak of 398 million requests per second (rps), and relied on a novel HTTP/2 'Rapid Reset' technique based on stream multiplexing that has affected multiple Internet infrastructure companies," Google said. "By contrast, last year's largest-recorded DDoS attack peaked at 46 million rps."
Google's graphic below illustrates the size of the record-breaking, two-minute attack, which the company said generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023.
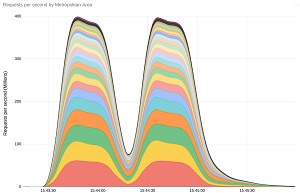 [Click on image for larger view.] Google mitigated a DDoS attack which peaked at 398 million requests per second (source: Google).
[Click on image for larger view.] Google mitigated a DDoS attack which peaked at 398 million requests per second (source: Google).
The cloud giant said its global load-balancing and DDoS mitigation infrastructure helped keep its services running and prompted the firm to team up with industry partners to gain a better understanding of the attack mechanics and collaborate on mitigation techniques.
To aid in the effort to understand the mechanics, Google published another post, "How it works: The novel HTTP/2 'Rapid Reset' DDoS attack."
That post explains the company reserved CVE-2023-44487 in the National Vulnerability Database to track fixes to various HTTP/2 implementations.
Internet services company Cloudflare, meanwhile, helped with mitigation guidance, noting that its infrastructure thwarted a recent barrage of attacks that included a new record-breaker exceeding 201 rps.
"This zero-day provided threat actors with a critical new tool in their Swiss Army knife of vulnerabilities to exploit and attack their victims at a magnitude that has never been seen before," Cloudflare said yesterday in its own blog post. "While at times complex and challenging to combat, these attacks allowed Cloudflare the opportunity to develop purpose-built technology to mitigate the effects of the zero-day vulnerability."
Cloudflare also joined in on that industry collaboration, entering conversations with industry peers to see how they could work together on the DDoS issue.
The post also provided recommendations for chief security officers (CSOs) to implement immediately:
- Understand your external and partner network's external connectivity to remediate any Internet facing systems with the mitigations below.
- Understand your existing security protection and capabilities you have to protect, detect and respond to an attack and immediately remediate any issues you have in your network.
- Ensure your DDoS Protection resides outside of your data center because if the traffic gets to your datacenter, it will be difficult to mitigate the DDoS attack.
- Ensure you have DDoS protection for Applications (Layer 7) and ensure you have Web Application Firewalls. Additionally as a best practice, ensure you have complete DDoS protection for DNS, Network Traffic (Layer 3) and API Firewalls
- Ensure web server and operating system patches are deployed across all Internet Facing Web Servers. Also, ensure all automation like Terraform builds and images are fully patched so older versions of web servers are not deployed into production over the secure images by accident.
- As a last resort, consider turning off HTTP/2 and HTTP/3 (likely also vulnerable) to mitigate the threat. This is a last resort only, because there will be a significant performance issues if you downgrade to HTTP/1.1
- Consider a secondary, cloud-based DDoS L7 provider at perimeter for resilience.
AWS, meanwhile, yesterday posted a security bulletin about CVE-2023-44487 - HTTP/2 Rapid Reset Attack:
Publication Date: 2023/10/10 05:00 AM PDT
AWS is aware of CVE-2023-44487, also known as "HTTP/2 Rapid Reset Attack," related to HTTP/2 capable web servers where rapid stream generation and cancellation can result in additional load which could lead to a Denial of Service. AWS infrastructure is designed with various protections to address Layer 7 request floods, however, we have implemented additional mitigations to address this issue. AWS also recommends customers who operate their own HTTP/2 capable web servers verify with their web server vendor to determine if they are affected and, if so, install the latest patches from their respective vendors to address this issue.
Customers can learn more about this in the AWS Security blog post, titled "How AWS Protects Customers from DDoS Events".
Security-related questions or concerns can be brought to our attention via [email protected].
The referenced blog post says: "Since late August 2023, AWS has detected and been protecting customer applications from a new type of distributed denial of service (DDoS) event. DDoS events attempt to disrupt the availability of a targeted system, such as a website or application, reducing the performance for legitimate users. Examples of DDoS events include HTTP request floods, reflection/amplification attacks, and packet floods. The DDoS events AWS detected were a type of HTTP/2 request flood, which occurs when a high volume of illegitimate web requests overwhelms a web server's ability to respond to legitimate client requests."
Like the other firms, AWS noted its infrastructure and services were up to the task of protecting customers and maintaining their services.
Google noted that the cross-industry collaboration around the recent spate of DDoS attacks paid off in the form of patches and other mitigation techniques used by big infrastructure providers. ,Furthermore, the company said, "The collaboration helped to pave the way for today's coordinated responsible disclosure of the new attack methodology and potential susceptibility across a multitude of common open source and commercial proxies, application servers and load balancers."
About the Author
David Ramel is an editor and writer at Converge 360.