News
A 5-Step Roadmap for Unstructured Data Security
Unstructured data is sprawling across clouds and devices -- and it's putting your organization at risk. But with the right roadmap, you can turn chaos into control.
Joey D'Antoni provided such a ready-made roadmap for organizations to get a handle on the problem in today's online summit presented by Virtualization & Cloud Review, titled "Unstructured and Unsecured: Tackling the Problem of Unstructured Data Assets," now available for on-demand replay. Everyone can benefit from tons of front-line expert advice in Joey's session, "Finding and Securing Unstructured Data Before It's Too Late."
While he touched on many subjects, including the explosive growth of machine telemetry data, the unique challenges of cloud object storage security, the risks of shadow IT deployments, the compliance implications of mismanaged data, and the historical lack of backup solutions for newer storage technologies, the ready-made roadmap provides a quick, handy takeaway that capsulizes the issue with related advice.
Joey first took time to frame for the audience the problem at hand.
 "We just don't know what we have, right? So some of this could be maybe a business unit picks up a SaaS tool that you didn't know about, like they started using ... a new solution from Salesforce that it wasn't aware about, and then you all of a sudden had data out there and you didn't know what you have."
"We just don't know what we have, right? So some of this could be maybe a business unit picks up a SaaS tool that you didn't know about, like they started using ... a new solution from Salesforce that it wasn't aware about, and then you all of a sudden had data out there and you didn't know what you have."
Joey D'Antoni, Principal Cloud Architect at 3Cloud
As he explained, "We just don't know what we have, right? So some of this could be maybe a business unit picks up a SaaS tool that you didn't know about, like they started using ... a new solution from Salesforce that it wasn't aware about, and then you all of a sudden had data out there and you didn't know what you have."
Joey emphasized that unstructured data isn't just growing -- it's multiplying in ways that traditional IT teams struggle to keep up with. He pointed out that "data you're getting from all these other places, like files, logs, images, machine data can grow a lot more rapidly than you can inherently have transactions and database." This surge isn't just about volume; it's about complexity, as data sprawls across multiple clouds, endpoints, and third-party services, making it harder to track, secure, and manage.
He also highlighted the persistent risks of misconfiguration and human error, especially as organizations rush to adopt new technologies. "Somebody who doesn't have experience with the service is going to be, like, I can't get the security to work on this correctly. I'm just going to open it to the internet, and then they forget about it, or they did it with sample data, and then it gets used for production. These are the kind of things that happen," Joey said. Compounding these risks are compliance requirements -- such as GDPR and HIPAA -- that can turn a simple oversight into a major incident if sensitive data is exposed or lost.
With these mounting challenges in mind, Joey laid out a practical framework for organizations to regain control over their unstructured data. His five-step roadmap isn't just theory -- it's a set of actionable priorities designed to help IT teams systematically identify, secure, and govern their sprawling data assets before they become tomorrow's headline breach.
Which leads to a central takeaway from the presentation, the roadmap for organizations to follow.
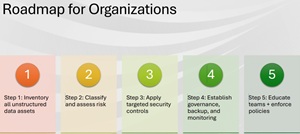 [Click on image for larger view.] Roadmap for Organizations (source: Joey D'Antoni).
[Click on image for larger view.] Roadmap for Organizations (source: Joey D'Antoni).
Joey's roadmap offers a clear sequence of steps to help organizations systematically address the sprawling and often hidden risks of unstructured data. Each step builds on the previous one, moving from discovery to risk assessment, targeted protection, governance, and finally, people and process improvements.
- Inventory all unstructured data assets: The foundation of any data security effort is knowing what data exists and where it resides. Joey highlighted the challenge of visibility at scale, saying, "We don't have inventory tools that manage this for us. This is a common problem." Deploying cloud data discovery tools is essential to gain this insight.
- Classify and assess risk: Understanding the sensitivity and compliance implications of different data types allows organizations to prioritize their security efforts. As Joey explained, "Even if, at least you understand what those compliance risks are, you can better manage that data and put some attention to it."
- Apply targeted security controls: Simply knowing what data you have isn't enough; applying the right security measures is crucial. Joey warned of common missteps: "Somebody who doesn't have experience with the service is going to be, like, I can't get the security to work on this correctly. I'm just going to open it to the internet, and then they forget about it." Proper configuration and controls are key.
- Establish governance, backup, and monitoring: Many organizations are still catching up on governance frameworks and backup capabilities for unstructured data, especially in object storage. Joey noted, "A lot of this is dating back to object stores. When they first were developed, [they] didn't have backup and recovery, so there was no backup for S3 or Azure Blob at first."
- Educate teams and enforce policies: The human factor remains a critical vulnerability. Joey stressed, "Somebody who doesn't have experience with the service is going to be, like, I can't get the security to work on this correctly... These are the kind of things that happen." Training and policy enforcement help mitigate these risks.
Those are all concise summaries, of course, and you need to watch the on-demand replay to get the individual items fleshed out in detail, but this gives you the overall idea of this part of Joey's presentation.
And, although replays are fine -- this was just today, after all, so timeliness isn't an issue -- there are benefits of attending such summits and webcasts from Virtualization & Cloud Review and sister sites in person. Paramount among these is the ability to ask questions of the presenters, a rare chance to get one-on-one advice from bona fide subject matter experts (not to mention the chance to win free prizes -- in this case $5 Starbucks gift cards for the first 300 attendees provided by sponsor Rubrik, a leader in cloud data management and enterprise data protection which also presented at the summit).
With all that in mind, here are some upcoming summits and webcasts coming up through June from our parent company:
About the Author
David Ramel is an editor and writer at Converge 360.