News
Ransomware vs. AWS S3: Smarter Defenses You Might Be Missing
Ransomware threats continue to evolve, with cloud environments and object storage like Amazon S3 becoming an increasingly frequent target. In a recent online summit titled "Real-World Ransomware Protection Strategies for S3 That You Haven't Considered," consultant Steven Smiley of ScaleSec explored the state of ransomware in the cloud and offered actionable defense techniques that go beyond the basics. The webcast was moderated by this writer and sponsored by Rubrik, a leader in cloud data management and enterprise data protection.
 "The average ransom last year was $1.5 million -- and about half of organizations are paying it."
"The average ransom last year was $1.5 million -- and about half of organizations are paying it."
Steven Smiley, Consulting Director, ScaleSec
Smiley's presentation was wide-ranging and densely packed with advice, so this article will focus on three key topics out of many: how attackers are commonly getting in, how an actual S3 ransomware attack unfolds, and how to build ransomware-resilient AWS backups.
How Attackers Are Getting In
"If you want to cover 80% of your risk, it's going to be coming from stolen credentials, phishing and those kinds of simpler attack vectors," Smiley said .
 [Click on image for larger view.](source: Smiley).
[Click on image for larger view.](source: Smiley).
While zero-day exploits and advanced techniques capture headlines, the reality is that most ransomware intrusions begin with very basic missteps. According to Smiley, the primary ways attackers gain entry include:
- Phishing
- Stolen credentials
- Vulnerable APIs
- Unintentional data exposure (e.g., public S3 buckets)
- Supply chain risks
- Exploitation of vulnerabilities (rare compared to other vectors)
Once inside, attackers often leverage widely available tools to scan for misconfigured assets. For example, Smiley highlighted how services like Greyhat Warfare index public S3 buckets, allowing bad actors to search for exposed sensitive data .
He emphasized that many organizations still struggle with "cloud security basics," including open firewall policies, exposed databases, missing multi-factor authentication (MFA) on privileged accounts, slow incident response times, and the proliferation of sensitive data across environments. "The first step to protecting your S3 data is just getting these cloud security basics right in your organization," Smiley said .
Anatomy of an S3 Ransomware Attack
Smiley provided a detailed walkthrough of an actual S3 ransomware attack investigated by the Halcyon RISE team. The sequence of events was as follows:
 [Click on image for larger view.](source: Smiley).
[Click on image for larger view.](source: Smiley).
- Attackers obtained stolen AWS credentials.
- Using those credentials, they listed all objects in targeted S3 buckets.
- They generated their own encryption key and re-encrypted the S3 objects using Server-Side Encryption with Customer-Provided Keys (SSE-C).
- They applied a 7-day S3 lifecycle deletion policy to the affected buckets.
- Finally, they uploaded a ransom note to the bucket.
Once this process completes, the original data is inaccessible without the attacker's encryption key. Smiley pointed out that "it's impossible to decrypt this without that key" and noted that lifecycle policies make deletion more scalable for large buckets than individual delete commands.
He also discussed related trends: "Exfiltration is kind of a necessary step" in these attacks, especially since in-cloud encryption often requires downloading, re-encrypting, and uploading objects .
How to Build Ransomware-Resilient AWS Backups
One of the most actionable portions of Smiley's talk involved practical guidance for building ransomware-resilient backup architectures in AWS. He recommended an approach that combines separation of duties, service control policies, immutable storage, and automation.
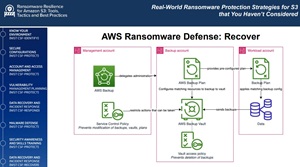 [Click on image for larger view.](source: Smiley).
[Click on image for larger view.](source: Smiley).
His reference architecture includes three distinct accounts:
| Account |
Primary Purpose |
| Management Account |
Delegates backup administration and applies restrictive Service Control Policies (SCPs) to subordinate accounts. |
| Backup Account |
Holds the immutable backup vault and enforces access controls to prevent tampering. |
| Workload Accounts |
Tag resources to be backed up according to predefined backup plans. |
Key recommendations included:
- Use AWS Backup with Vault Lock to enforce immutability.
- Apply restrictive SCPs to prevent backup tampering, even by backup administrators.
- Require developers only to tag resources appropriately; automation handles backup creation.
- Maintain "golden images" or deterministic infrastructure-as-code definitions to enable rapid rebuilds if needed.
"Even if someone gets into your backup account and they have admin permission on it, they won't be able to tamper with the backup vault," Smiley stressed.
Conclusion
While ransomware targeting AWS S3 may sound advanced, the root cause is often basic mistakes. "Most of this comes from cloud security basics that organizations just continue to struggle with," Smiley said.
By addressing foundational weaknesses, understanding real-world attack techniques, and implementing layered, resilient backup strategies, cloud teams can significantly strengthen their defenses against this evolving threat.
And More
For those who missed the live event, as noted above the session will be available for replay available on-demand.
Beyond those top three topics discussed above, Smiley also covered a range of other key ransomware defense techniques, including using Service Control Policies to block cryptoshredding, enabling advanced threat detection with Amazon GuardDuty, deploying honey tokens to detect credential misuse, alerting on risky AWS events, leveraging S3 Object Lock for immutability, implementing phishing-resistant multi-factor authentication, and improving incident response planning and log visibility. You can learn all about those in the replay.
And, although replays are fine -- this was just today, after all, so timeliness isn't an issue -- there are benefits of attending such summits and webcasts from Virtualization & Cloud Review and sister sites in person. Paramount among these is the ability to ask questions of the presenters, a rare chance to get one-on-one advice from bona fide subject matter experts (not to mention the chance to win free prizes -- in this case $5 Starbucks vouchers for the first 300 attendees of the full summit, which also featured Rubrik presenting).
With all that in mind, here are some upcoming summits and webcasts coming up through the rest of June from our parent company:
About the Author
David Ramel is an editor and writer at Converge 360.