How-To
My Attempt to Destroy a Secure Storage Device
Tom Fenton puts "crush-proof" ruggedness claims to the test with a fall, a truck, a snow ski, water and ice.
After having reviewed few different iStorage devices over the past few years (articles located here and here), I was going to pass when they asked if I wanted to review their latest drive, the M2 -- until I read this blurb about it in their marketing packet:
The diskAshur M² is lightweight, dust and waterproof (IP68 certified), shock proof (survives a drop of 4m on to a concrete surface) and crush-proof (withstands the weight of a 2.7-ton vehicle), making it extremely rugged and ultra-portable.
I know that the other iStorage devices that I have reviewed are very secure, but I was intrigued by the supposed extreme ruggedness of this one. In this article, I will give you an overview of the M2 device, tell you about my attempt to destroy it to test its true ruggedness, and then provide my final thoughts on it.
The device that I received was the iStorage diskAshur M2 1TB drive (IS DAM2-256-1000). The package contains a case, USB type A and C cables, a warranty and a Quick Start Guide (in English, German, French, Spanish and Italian).
 [Click on image for larger view.]
[Click on image for larger view.]
The device itself comes in a metal sleeve and has a chrome metal top with a rubber gasket. On the front of the device is a numerical keyboard, and on the bottom is a USB cable connector. Its security certifications include (but are not limited to): NCSC CPA, FIPS 140-2 Level 3, NLNCSA BSPA and NATO restricted level.
The drive is 45mm wide, 106mm long, and 12mm thick. It weighs 86 grams. The USB 3.1 cord is 12cm long and is permanently affixed to the device. The street price of a 1TB M2 is around $275. It also comes in 120Gb, 240GB, 500GB and 2TB capacities.
Security Features
Data on the drive is encrypted using AES-XTS 256-bit hardware encryption, which is performed by a hardware encryption module certified to the FIPS 140-2 standard (meeting the US government security standard for data encryption). It has hardware safeguards to defend against external tampering, and if it detects any attempt to get into the case or tinker with the USB, it will trigger a deadlock frozen state -- at which point the data on it will become inaccessible.
The device supports PIN numbers for four different modes: admin, user, self-destruct and one-time recovery. The admin PIN allows you to change the device's settings on the drive or do a factory reset. The user PIN allows you access the information on the device. If you enter the self-destruct PIN, the data will be wiped from the drive. If a user has forgotten their PIN, they can use the one-time recovery PIN and set a new user PIN.
 [Click on image for larger view.]
[Click on image for larger view.]
The device can be set up with write protection after files have been written to it. This allows the files on it to be read but not modified, and new files cannot be added.
After connecting the drive to a computer, a user has 10 attempts to enter the PIN number correctly via the keyboard; if they enter the wrong PIN ten times, the user PIN will be deleted but the data, admin PIN and recovery PIN will remain intact. If an incorrect recovery PIN is entered five consecutive times, the recovery PIN will be deleted, but the data and admin PIN remain intact and accessible. Finally, if an incorrect admin PIN is entered 10 consecutive times, the drive will factory reset (i.e., all PINs and current data will be deleted forever).
General Usage
Unlike most drives, you absolutely must read the user's manual for the M2 in order to understand how to use this device since all functions, such as resetting the passwords, are accomplished using the keypad. The user guide has a diagram that indicates what the keys are used for and what the LED lights signify.
After plugging the device into my laptop, I set the admin and user PIN numbers as it does not have any default PINs.
I pressed the shift and key button, and then entered the user PIN and the key button to unlock the device. The green LED signaled that the device was unlocked. I formatted the drive and transferred 100GB of files to and then from it. iStorage claims it has read and write speeds of up to 370MB/s, and my transfers were slightly under that.
On the laptop that the device was connected to, I used the Windows System Information utility to view the drive, which identified it as a 1 TB external hard disk drive. I unplugged the device from the laptop and plugged it back in. My laptop did not show it as being attached to the laptop.
I entered Admin Mode and set a new user PIN and the requirements associated with that PIN. As the device does not have an alphanumerical screen, and only the three indicator lights, you can only manage the device using the keyboard and the instructions in the user's guide. I set a self-destruction and user PIN, and configured the device to automatically lock after 60 minutes.
Extreme care must be used with the self-destruction PIN as it will delete all data and PINs. If this occurs, and you'd like to use device again, you will need to set a new admin password. At that point, the device will need to be partitioned and formatted before any new data can be added to the drive.
To test the self-destruct mode, I unlocked the drive, copied files to the drive, locked the drive and entered the self-destruct code. After doing this, no information on the drive could be read; I then needed to create a new admin PIN and repartition and reformat the drive.
My Attempt to Destroy the Device
The real tests that I wanted to perform on the drive was to determine if I could destroy it.
The company states that it "survives a drop of 4m on to a concrete surface," so I accidentally knocked it off my deck, which I judged to be about four meters. I plugged the device back into my laptop and it performed flawlessly.
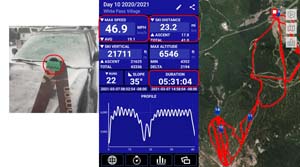
As I happened to be heading up to the mountains, so I accidentally taped the device to the tip of my ski and hit the slopes for some runs. After 5-and-a-half hours and 23.2 miles of skiing, I plugged the device back into my laptop and it performed flawlessly.
 [Click on image for larger view.]
[Click on image for larger view.]
Over the night we were expecting a cold front, so I accidentally placed the device in a glass of water and left it outside for two days to check its waterproofness (ice is water, right?). After thawing it out, I removed the device from the sleeve. I didn't find any water in it, and the rubber gasket worked well. I plugged the device back into my laptop and it performed flawlessly once again.
 [Click on image for larger view.]
[Click on image for larger view.]
iStorage claims that the M2 device is crush-proof and can withstand the weight of a 2.7-ton vehicle. I couldn't find a 2.7-ton vehicle, so I had my buddy Chris accidentally run it over with his RAM 2500 crew cab truck on an asphalt surface. The RAM spec sheet said that it weighs in at 7,414 or 3.8 US tons.
 [Click on image for larger view.]
[Click on image for larger view.]
\
I placed a tortilla chip next to the device for visibility, scale and proof of being run over.
 [Click on image for larger view.]
[Click on image for larger view.]
I then had him back over it again.
 [Click on image for larger view.]
[Click on image for larger view.]
The device's sleeve was slightly indented, and the chrome on the top of the device was slightly chipped.
 [Click on image for larger view.]
[Click on image for larger view.]
When I plugged the device back into my laptop, it performed flawlessly; however, the tortilla chip was unsalvageable.
 [Click on image for larger view.]
[Click on image for larger view.]
Conclusion
I knew that the iStorage diskAshur M2 would be very secure, and I do like the enhancements that they made it, such as coming out-of-box without a password and one-time-recovery password. You will need to read the manual before using the device, but it performed exactly as expected when I followed the instructions.
What I was interested in was testing how rugged the device really is based on iStorage's claims. In the end, I found that it was, in fact, very waterproof and could handle being run over by one of the heaviest pickup truck vehicles currently for sale. While this device isn't for everyone, if you have sensitive data that needs a high level of protection in a rugged package, this device is for you. Well done, iStorage!
In a sense, I did fail at my attempt to destroy this device, but I do plan on doing additional testing and an update on this article to keep you posted on my attempts to ruin it.
About the Author
Tom Fenton has a wealth of hands-on IT experience gained over the past 30 years in a variety of technologies, with the past 20 years focusing on virtualization and storage. He previously worked as a Technical Marketing Manager for ControlUp. He also previously worked at VMware in Staff and Senior level positions. He has also worked as a Senior Validation Engineer with The Taneja Group, where he headed the Validation Service Lab and was instrumental in starting up its vSphere Virtual Volumes practice. He's on X @vDoppler.