How-To
Running a Secure VM Using the iStorage diskAshur PRO2 Portable Hard Drive
Tom Fenton gives an overview of the iStorage diskAshur PRO2 portable hard drive and his attempt to store and run a virtual machine on it.
I recently received an iStorage diskAshur PRO2 to review. What makes this drive unique is that it has hardware encryption and is unlocked via a numerical keyboard on top of the drive. While examining the drive, I got the idea that it might be interesting to see if I could use it to store and run a virtual machine (VM). In this article, I will give you an overview of the device, tell you about my attempt to use it store my VM, and then provide my final thoughts.
The device that I received was the iStorage diskAshur Pro2 2TB drive (IS DAP2-255-2000-C-G). After opening the box, I found the device and case, a lifetime license for Nero BackItUp, a warranty, and a Quick Start Guide in English, German, French, Spanish, and Italian (see Figure 1).
 [Click on image for larger view.] Figure 1
[Click on image for larger view.] Figure 1
The device looks unlike any other portable hard drive I have seen yet with its numerical keyboard on the front and USB cable cleverly tucked into the side. To tamper-proof the device, it is covered with an epoxy resin. It has NCSC CPA, FIPS 140-2 Level 3, NLNCSA BSPA, and NATO restricted level certification.
The drive is 84mm wide, 124mm long, and 20mm thick (see Figure 2). The USB cord is 12cm long and is permanently affixed to the device, with USB 3.1 connectivity. The street price of the device is around $326.
 [Click on image for larger view.] Figure 2
[Click on image for larger view.] Figure 2
Security Features
All data on the drive is encrypted using 256-bit AES encryption, performed by a hardware encryption module certified to the FIPS 140-2 standard which meets the US government security standard for data encryption. It has hardware safeguards to defend against external tampering, and if it detects any attempt to get into the case or tinker with the USB, it will trigger a deadlock frozen state – at which point the data on it will become inaccessible.
The device supports three different PIN numbers: admin, user, and self-destruct. The admin PIN allows you to change settings on the drive and do a factory reset of the device. The user PIN allows you access the information on the device. If you enter the self-destruct PIN, the data will be wiped from the drive.
After connecting the drive to your computer, you have ten attempts to enter the PIN number correctly via the keyboard; if you enter the wrong PIN ten times, the drive will freeze and you will need to disconnect and reconnect to the USB port before it will allow you to try to enter the PIN again. At that point, you will be able to attempt to unlock the lock the drive five more times while holding down the shift key. If, after 15 unsuccessful attempts, you still haven't entered the correct PIN, the encryption key will be deleted, the unit will lock itself, and the device will need to be reset to be used again.
General Usage
Unlike most drives, you absolutely must read the user's manual in order to understand how to use this device as all functions, such as resetting the passwords, are accomplished using the keypad. The user guide has a diagram that indicates what the keys and LED lights are used for (see Figure 3).
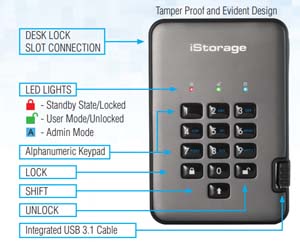 [Click on image for larger view.] Figure 3
[Click on image for larger view.] Figure 3
After plugging the device into my laptop, I entered the admin PIN number (the device comes out of the box with a default admin PIN of 11223344), and then pressed the button with the UNLOCK icon. When I did so, the unlock light turned green and I received a message that asked me what I would like to do with the drive (see Figure 4). I chose to open File Explorer, and the only file I found on the device was the user's manual.
 [Click on image for larger view.] Figure 4
[Click on image for larger view.] Figure 4
On the laptop that the device was connected to, I used the Windows System Information utility to view the drive, which identified the device as a 1.82 TB external hard disk (see Figure 5).
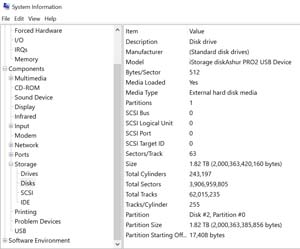 [Click on image for larger view.] Figure 5
[Click on image for larger view.] Figure 5
When I pressed the button with the LOCK icon on the device, File Explorer disappeared and the device was no longer seen by the computer; the device's locked light was red. When I reentered the admin PIN and pressed the unlock key, the device was again recognized by my laptop.
I entered Admin Mode by locking the device and holding down the “UNLOCK + 1” buttons, and then entering the admin PIN and pressing the UNLOCK button; the blue Admin Mode light was then on. From Admin Mode, I could change the admin PIN, set a new user PIN, and set the requirements for the user PIN. As the device does not have an alphanumerical screen and only the 3 indicator lights, you can only manage the device using the keyboard and the instructions in the user's guide. I set a self-destruction and user PIN, and set the device to automatically lock after 60 minutes.
Extreme care must be used with the self-destruction PIN as it will delete all data and admin/user PINs, and then unlock the drive. Self-destruction will cause the self-destruct PIN to become the new user PIN and the diskAshur PRO2 will need to be partitioned and formatted before any new data can be added to the drive. The self-destruct PIN becomes the user PIN, and no admin PIN exists after the self-destruct mechanism is activated. The drive will then need to be reset before it can be used again.
To test the self-destruct mode, I unlocked the drive, copied files to the drive, locked the drive, and entered the self-destruct code. After doing this, no information on the drive could be read; I then needed to create a new admin pin, and repartition and reformat the drive.
Using it for a VM
The real test that I wanted to perform on the drive was to see if I could use the device to store and run a VM. To do so, I connected the drive to my laptop and then unlocked the drive. I then used VMware Workstation Pro 15 to create an Ubuntu 18.04.3 LTS VM on the drive. The VM had 2 vCPUs, 4GB of RAM and a 64GB hard drive. I didn't have any issues creating the VM, and it took the same amount of time that it would have to create a VM on any other drive connected via a USB 3.1.
I then wanted to see how well the VM stored on the device performed, so I brought up a web browser, edited documents using LibreOffice, and used other utilities on the desktop. I didn't notice any difference when comparing its performance to the responsiveness of a VM stored on my laptop's drive.
After working with the VM, I locked the drive and entered an incorrect PIN number 10 times. The drive froze and I needed to disconnect and reconnect to the USB port. I tried to unlock the drive five more times while holding down the shift key and entering an incorrect PIN. After 15 total unsuccessful attempts, the unit locked itself and the device needed to be reset, re-partitioned, and re-formatted before I could use it again. I could not access any data on the drive after resetting it.
Conclusion
The iStorage diskAshur PRO2 is well-built, and the keys have a positive aesthetic feel to them as they click when pressed. I found the self-destruct key an interesting idea as it allows you to make the drive unreadable with a single PIN. You will need to read the manual before using the device, but the device performed exactly as expected when I followed the instructions. While this device isn't for everyone, if you have sensitive data or even a VM that needs a high level of protection, this device will be able to securely store and run them.
About the Author
Tom Fenton has a wealth of hands-on IT experience gained over the past 30 years in a variety of technologies, with the past 20 years focusing on virtualization and storage. He previously worked as a Technical Marketing Manager for ControlUp. He also previously worked at VMware in Staff and Senior level positions. He has also worked as a Senior Validation Engineer with The Taneja Group, where he headed the Validation Service Lab and was instrumental in starting up its vSphere Virtual Volumes practice. He's on X @vDoppler.