News
Ransomware: What To Do If You Don't Have a Plan
Nothing vaults ransomware into the IT discussion like a $4.4 million payout accompanied by a crippling gas shortage and $7-per-gallon gas gouging. That, of course, is what happened with the recent Colonial Pipeline attack.
Ransomware is becoming one of the pre-eminent cyber-attacks because of the continued vulnerabilities discovered and exploited by Russian or other groups, who just keep succeeding in netting hefty payments from organizations desperate to get back in business when all their operational data is stolen.
There's nothing quite like a massive business disruption solvable only by a multi-million payout to prompt an urgent call from the CEO, putting an IT administrator's job one the line.
That's why it has become a popular topic among a continuing series of webcasts put on by Virtualization & Cloud Review. One example is the recent Responding to Ransomware Virtual Summit, a three-part event now available on demand.
This reporter moderated one of the sessions, Ransomware Recovery: What to do if You're Hit and You Didn't Have a Plan. The presenter was Dale Meredith, a cyber-security trainer and Pluralsight author who detailed the critical steps every organization should actually take before a data breach, because they're much more complicated and can just be the-horse-is-out-of-the-barn ineffective
Paramount, of course, is having a disaster recovery/business continuity plan.
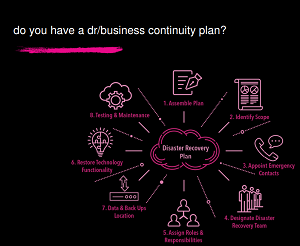 [Click on image for larger view.] DR/Business Continuity Plan
[Click on image for larger view.] DR/Business Continuity Plan
Not everybody has such a plan, though, and Meredith discussed several scenarios on the being-prepared spectrum. Here's a checklist he used in the presentation:
 [Click on image for larger view.] What to do if You don't Have a Plan
[Click on image for larger view.] What to do if You don't Have a Plan
Following are some of his comments about those items.
Stop talking and start doing!
"Remember what I told you before? What do we do?" he said, jokingly continuing, "Well, uh, update our resume, Dale, and get those letters of recommendations." Joking aside, that's what just may happen if a $5 million ransomware attack occurs on your watch. He then detailed exactly what to do if no plan is in place, starting with the basics, including an admonition to stop talking and start doing. "What we mean by that is that you can accept risks forever, but the day's going to come to you and it's going to bite you. And you're going to end up doing the work in the end." What's more, it's going to be a lot harder because you'll be under tremendous pressure, so you should get started right away. So, following are descriptions of some of that work that should be done before an attack.
Enforce MFA
"We need to enforce our MFA [Multi-factor Authentication, in which users must provide two or more verification factors in order to access to a resource]. Enabling Multi-factor Authentication for everybody is going to save you so much time." People understand MFA, which is being enforced by social media and other companies now, he said. People are doing it right now with banking apps and such, so it's not a new concept and users can readily adapt to it.
Stop with the common password issue
"We've got to stop allowing users to do that." One example of what damage that practice can cause is the famed SolarWinds attack, which was helped by someone using the password "solarwinds123. "We've got to stop that. We have technology in place that allows us to make sure people aren't using common words."
Use authentication ... correctly!
"We need to make sure we're doing authentication the right way." Techniques include password hashing, used to verify the integrity of a password. Another one is Azure AD SSO, which Microsoft says can help "unburden users of having to memorize credentials for different apps or reusing weak passwords, increasing the risk of data breach." Another one is Azure AD device registration to support the Bring Your Own Device (BYOD) or mobile device scenarios.
Protect identities
Meredith said one example of this is using the "wonderful" Microsoft 365 identify protection feature used to:
- Automate the detection and remediation of identity-based risks.
- Investigate risks using data in the portal.
- Export risk detection data to third-party utilities for further analysis.
Get a privileged access baseline in place
"We need to make sure that admin and service and application accounts are used exclusively for workstations or servers or domain controllers." Also key is removing things like default settings and policies, which can be more easily exploited. "Defaults will kill you all the time." Admin group policies should also be enforced. "If you don't set the rules you're going to have all kinds of interesting things going on an you're going to be at significant risk."
Make a list of mission-critical apps
It's important to list them by priority "so when it comes to what we need to bring back up or what is the most important to bring back first, we can do that."
Update/replace out-of-support OSes
This can be complicated, with Meredith noting that during the notorious Norsk Hydro attack, the company was in the middle of upgrading from Windows 7 to Windows 10, so obviously Windows 7 wasn't brought back. "When we decide to make a change to an operating system, we need to make sure the budget is there" as well as support to get it done as quickly as possible, because the more out-of-support systems that are in place, the greater the risk for organizational systems.
Patches/updates
"I think I've mentioned to you about patching and updates and I'm not going to just focus on operating systems. I want to make sure you understand doing that all of our applications as well as plug-ins for applications. When's the last time you updated a BIOS on a router? That should always be a priority."
Stop recycling service accounts
Here he used the example of a SharePoint deployment. "When I deploy SharePoint, I don't create one service account that handles all the bells and whistles of SharePoint. I create four different ones and each one has their own limitations on what they can do with SharePoint. And I don't recycle them." An example of the latter is re-using an SQL service account for SharePoint. "You have to stop doing that."
And more
While the above represent the top 10 items on Meredith's checklist, he went on to address many more items including:
- End user accounts shouldn't be used as admin accounts
- Server admin account should not have admin rights on workstation
- Produce a clear line of leadership
- Create a risk assessment of your recourses
- Inventory resources and assessments
- Organize an incident event log
He also addressed many other issues in his presentation, which was paired with two others, including one by Allan Liska, titled Ransomware 2021: What to Expect in the Year Ahead, from Malware Families to Payout Trends.
As noted, the three-part online summit is now available for free on demand.
Also there are upcoming events sure to be even more timely in the aftermath of the Colonial Pipeline fiasco, such as Enterprise Ransomware & Recovery Summit, a half-day event on June 4.
Other recent on-demand events available for free include:
All Virtualization & Cloud Review webcasts can be seen here.
About the Author
David Ramel is an editor and writer at Converge 360.