How-To
How Microsoft 365 Defender Integrates Security Services
Paul Schnackenburg takes a look at how Microsoft 365 Defender integrates several different security technologies into a single console.
There's a change coming to selecting security solutions for your organization and it has to do with integration. For many years, most businesses picked applications that were "best in breed" for a particular risk mitigation, but as many are realizing now, this results in siloed products that don't give you a holistic view of attacks. Attackers move from system to system whenever they can, and if the point solutions that protect each of those systems aren't communicating, you can easily miss the attack.
There are two approaches to fixing this issue. One is Security Orchestration, Automation and Response (SOAR) where the Orchestration part refers to the integration of different security solutions using APIs and scripting. The second is deploying an already integrated system (at least for part of your stack). In this article I'll look at Microsoft 365 Defender and how it marries several different technologies into a single console. This is known as eXtended Detection and Response (XDR), an extension of Endpoint Detection and Response (EDR) to indicate that not only endpoints but all systems are included in the protection and response.
What's in a Name?
The services we'll discuss here changed names towards the end of 2020 so you may know them as Office 365 Advanced Threat Protection (ATP), now Microsoft Defender for Office 365 (MDO), Microsoft Defender Advanced Threat Protection, now Microsoft Defender for Endpoint (MDE), Azure Advanced Threat Protection, now Microsoft Defender for Identity (MDI). Add Azure Defender, Azure Sentinel and Microsoft Cloud App Security (MCAS) to the mix and there's a strong case that you've got most of your bases covered.
Should I Be Paying for This?
Before I go into how each of these services work and how they integrate, let's look at a common bugbear many IT pros have with Microsoft (including myself). There's no doubt that there's some cutting-edge tech in these security services, and if configured correctly and customized to your business they'll vastly improve your organization's security posture. But there's a case to be made that you shouldn't have to pay extra for something that should have been part of the platform in the first place. It's a bit like selling you the car at one price and then asking you to pay extra for the brakes.
It's a grey area and when Satya publicly says that security is a $10 billion-a-year business for Microsoft you have to wonder how much of a calculated risk that statement is. No matter where you land in this debate, the cost you're paying for any security solution, from any vendor, is minor compared to the cost of a large-scale successful attack, such as ransomware bringing your business to a standstill for days.
Defender for Identity
Let's make sure you don't have to find out how costly a major attack can be, starting with Active Directory (AD) on-premises. Most medium to large organizations still rely on AD to manage identity for their internal networks and it's a favorite target of criminals. MDI is a cloud service that's laser focused on AD but will catch most attackers, simply because they move laterally from system to system and that necessitates interacting with AD.
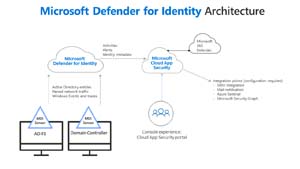 [Click on image for larger view.] MDI Architecture (source: Microsoft).
[Click on image for larger view.] MDI Architecture (source: Microsoft).
MDI is deployed by putting an agent on every DC, or if your security team really can't swallow that pill, a proxy agent on member servers, which uploads select network capture data, a set of event log entries and AD information to the cloud service. MDI used to have its own web portal, was then integrated into the MCAS portal (no MCAS licensing required) and will eventually be integrated into the Microsoft 365 Defender portal.
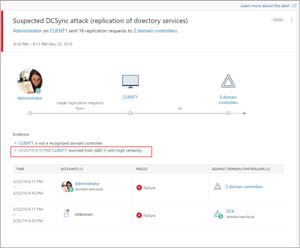 [Click on image for larger view.] MDI Alert DC Sync Attack (source: Microsoft).
[Click on image for larger view.] MDI Alert DC Sync Attack (source: Microsoft).
MDI catches attacks during the reconnaissance, compromised credentials, lateral movement, domain dominance and exfiltration phase of the kill chain. It uses User and Entity Behavior Analytics (UEBA) to "learn" about your user and computer accounts normal behavior so some of the detections take a few weeks before they become active.
The forebear of MDI is Advanced Threat Analytics (ATA), now in extended support, which does essentially the same thing as MDI but as an on-premises server. The benefit of MDI is that as a cloud service it can be updated with detections for novel attacks much quicker. A recent addition to MDI is the ability to monitor your AD Federation Services (ADFS) infrastructure, a result of the Solarwinds attack.
Defender for Office 365
This is probably the one that most people think should be built into the basic Microsoft 365 plans rather than only available in the higher SKUs (plan 1 is included in Microsoft 365 Business Premium, plan 2 is included in Office 365 E5 and Microsoft 365 E5/E5 Security).
MDO plan 1 adds the following protections on top of the standard Exchange Online Protection (EOP) that protects every Office 365 account:
- Safe Attachments (for Exchange, SharePoint, OneDrive and Teams)
- Safe Links
- Anti-phishing
On top of those, plan 2 adds:
- Threat Trackers
- Threat Explorer
- Automated investigation and response (AIR)
- Attack simulation training
- Campaign views
Every attachment to an incoming email to Exchange online is scanned by three anti-malware engines, but Safe Attachment will (provided the scans come up clean and the attached file has never been seen before) also open it in a sandbox VM to ensure it's safe. Safe Attachments can now also be configured to scan files in SharePoint, OneDrive and Teams.
Safe Links will rewrite URLs in emails (whilst still showing the original URL when you hoover over it so that users who have been trained to spot weird ones still can) so that the webpage or file is assessed for safety at the time the user clicks the link.
Anti-phishing adds impersonation protection and more aggressive phishing thresholds on top of the spoof protection and mailbox intelligence that all users have access to. Mailbox intelligence is interesting (but a bit creepy). Essentially it uses machine learning (ML) to identify normal emailing patterns between users, and unusual emails raise the suspicion level of the system.
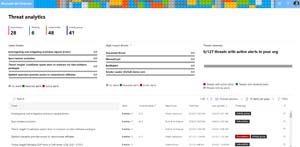 [Click on image for larger view.] Microsoft 365 Defender Threat Analytics.
[Click on image for larger view.] Microsoft 365 Defender Threat Analytics.
For larger businesses with E5 licensing Threat Trackers, Threat Explorer and Threat analytics gives you information about current malware and cybersecurity trends that may affect your business as well as the ability to explore current phishing and malware attacks against your business. AIR, on the other hand, is Microsoft's way of relieving the alert fatigue for your analysts by taking alerts -- automatically investigating recipients, files and URLs -- and related alerts and then recommending actions that your security staff can then approve or reject.
Attack simulation is a way to test your user's security awareness with benign phishing emails and other attacks. If they fail the test, you can automatically schedule short, web-based training sessions for them. Campaign views gives you the big picture of distributed attacks against your enterprise which you may not see (quickly enough) based on individual alerts.
Defender for Endpoint
If you think Windows Defender is just a basic AV protection, think again, it's now a very capable anti-malware solution built into every Windows 10 PC. MDE adds full EDR capabilities to Windows and macOS plus basic protection to Android and iOS devices. Because MDE is essentially built into every Windows 10 PC, there's no agent to deploy. You simply run a script (or use Configuration Manager, Endpoint Manager or GPOs at scale) to enrol the device in your tenant.
MDE provides AIR for endpoint investigations, a complete software inventory for all devices and a comprehensive Threat and Vulnerability solution that lets you know how many devices have a vulnerable software package installed. Based on the severity of the risk, it will give you a prioritized list of updates. MDE also integrates with Endpoint Manager so if the security team can't deploy the upgrades because they don't have permissions, a task with all the details can be created in Endpoint Manager (Intune) for the desktop team.
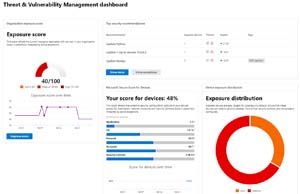 [Click on image for larger view.] Threat and Vulnerability Management Dashboard.
[Click on image for larger view.] Threat and Vulnerability Management Dashboard.
Microsoft 365 Defender
These tools used to have separate portals, but MDO is now integrated into the central Microsoft 365 Defender (https://security.microsoft.com) UI and MDE's portal is only available if you haven't completed the migration. MDI as mentioned will take a little longer to integrate. A single UI is important, but the exchange of alerts and threat information is even more crucial and that's just a single click in these solutions.
This gives you a single alerts queue, a single page to view all user information from each system, a single investigation experience and threat analytics that'll light up if a particular threat is detected in your environment.
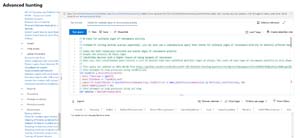 [Click on image for larger view.] Advanced Hunting in Microsoft 365 Defender.
[Click on image for larger view.] Advanced Hunting in Microsoft 365 Defender.
The Advanced hunting interface will be particularly useful to advanced analysts where you can run queries against Office 365 email/file, endpoint software and processes, network and cloud traffic and AD security data in a single location.
MCAS also feeds information into Microsoft 365 Defender, and if you're also using MDE it acts as an agent for MCAS so even if your users are working from home, you can control access to cloud services securely.
Conclusion
The integration of all these security services in one central place gives you great protection if your business lives in the Microsoft 365 ecosystem. Most businesses are heterogeneous however, and this is where Azure Sentinel comes in as the glue that connects to more than 100 different third-party security and service solutions for a single SIEM view across your enterprise, whilst still integrating closely with Microsoft 365 Defender.