In-Depth
Take a Spin with Azure Sentinel -- a SIEM in the Cloud
Paul Schnackenburg takes a look at the public preview of the new Microsoft cloud-based Security Information and Event Management service.
In February 2019 Microsoft announced a new service called Azure Sentinel. It's a cloud-based Security Information and Event Management (SIEM), which is a centralized location for all security log information from endpoints, network devices, cloud services and servers. The SIEM then analyzes this data and presents correlated information for analysts to act upon.
Interestingly (showing how important security is to the big cloud players), security-focused Chronicle (a company from Google's public holding company Alphabet) announced its cloud-based SIEM product called Backstory a little later.
In this article I take the public preview of Sentinel for a spin to see how it works and how easy it is to get useful information from it, as well as contrast it with Chronicle's Backstory.
 [Click on image for larger view.]
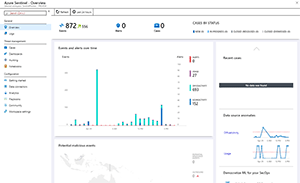
Figure 1. The Azure Sentinel overview page.
[Click on image for larger view.]
Figure 1. The Azure Sentinel overview page.
Building Blocks
One thing I really like about Azure Sentinel is how it's built on existing services in Azure (Figure 1). The analytics component is provided by Log Analytics, a mature service that's now part of the overall Azure Monitor platform. The data exploration is provided through Data Explorer and the query language is the same language that's used in Log Analytics -- Kusto Query Language (KQL), which is SQL-like, but simpler. Pluralsight offers a free 4.5-hour course if you need to get up to speed on Kusto.
Data ingestion is through syslog along with a good number (for a preview) of prebuilt data connectors. The usual Microsoft suspects are there, of course, like Office 365, Azure Active Directory (AAD), AAD Identity Protection and Azure Advanced Threat Protection, Cloud App Security and Azure Security Center, Azure Activity and Azure Information Protection and the Azure Web Application Firewall (WAF), along with Azure DNS. But out of the gate third-party platforms such as Amazon Web Services (AWS), Palo Alto Networks, Cisco ASA, Check Point, Fortinet, F5, Barracuda and Symantec ICDX are supported. You can also ingest raw syslog data and Common Event Format (CEF) data, along with Threat Intelligence (Figure 2).
 [Click on image for larger view.]
Figure 2. Data connectors in Azure Sentinel.
[Click on image for larger view.]
Figure 2. Data connectors in Azure Sentinel.
Machine Learning (ML) is one of the important foundations of Azure Sentinel, the goal of any capable SIEM today is to have the system correlate low-fidelity signals into high-confidence alerts so that analysts are only presented with issues that truly demand a human's insight. Many SIEMs are built on the premise of "find an anomaly -- alert a human." The problem is that there are only so many humans to go around in a Security Operations Center (SOC) and a SIEM must automate as much of the correlation. Another component of ML in Azure Sentinel is Fusion, which uses graph-powered ML algorithms to correlate low-fidelity anomalous activities in Cloud App Security and Azure AD Identity Protection, specifically to reduce alert fatigue. Currently, you have to enable this manually -- I assume this will be enabled by default in the GA product.
You can keep the data between seven days and two years, with data export options coming.
Using Azure Sentinel
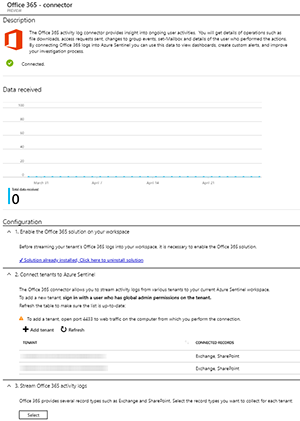
I logged on to the Azure Portal, searched for Azure Sentinel, created a new Log Analytics workspace and clicked on Data connectors under Configuration where I added two Office 365 tenants (Figure 3). A guided experience first enabled the Office 365 Log Analytics solution, then let me log in to each tenant (as Global Administrator) and prompted me for permission to access the data. This was followed by defining if I wanted only Exchange or SharePoint data, or both. Finally, several suggested dashboards were offered. The experience to connect Azure activity data was similar but even simpler.
 [Click on image for larger view.]
Figure 3. Connecting Office 365 tenants to Azure Sentinel.
[Click on image for larger view.]
Figure 3. Connecting Office 365 tenants to Azure Sentinel.
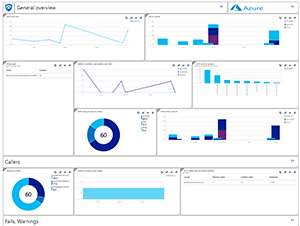
The dashboards (Figure 4) provide useful overviews of what's going on and when you click on a data point, you're taken to the Logs area where you can customize the query that generated the data. Suspicious events are automatically grouped into cases and you can add Playbooks (really just Logic Apps workflows) to automate responses or connections to external systems such as a ticketing system. You can also create alerts, although emailing them isn't supported yet.
 [Click on image for larger view.]
Figure 4. The Office 365 activity dashboard.
[Click on image for larger view.]
Figure 4. The Office 365 activity dashboard.
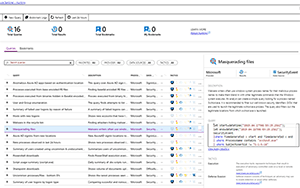
The Hunting tab provides prebuilt queries (with more provided in the GitHub repository) to trawl through your data looking for anomalies and potential attacks (Figure 5). The Notebook tab lets you access Azure Notebooks that are hosted Jupyter canvases for holding data, graphics, visualizations and executable code, used for hunting and investigations.
 [Click on image for larger view.]
Figure 5. Hunting queries in Azure Sentintel.
[Click on image for larger view.]
Figure 5. Hunting queries in Azure Sentintel.
One concern I had is that the data can sometimes take a few minutes to show up, although cloud-based events are meant to be fetched directly (O365, Azure and AWS). I assume this will be improved as Azure Sentinel becomes more polished.
Azure Sentinel also supports Security Orchestration, Automation and Response (SOAR) to further reduce the number of times an analyst needs to intervene.
On the Horizon
It's early days yet and there will be changes to Azure Sentinel as it transitions from preview to GA (perhaps at the Build conference in early May 2019) and beyond, based on feedback.
One feature that's been promised is a centralized console for Managed Security Service Providers (MSSPs) where they can monitor many clients in a single workspace.
Azure Sentinel also ties in with a new service, Microsoft Threat Experts (MTE), essentially security experts that you can call on demand when you have an incident or breach, or you need to augment your current SOC capabilities. Currently you can access the preview of MTE through your Windows Defender ATP Security Center and you need to have rolled out Windows (recently renamed to "Microsoft") Advanced Threat Protection to your endpoints.
Backstory
Just as Azure Sentinel grew out of internal tools developed inside Microsoft, Backstory is based on an internal tool that Chronicle's sister company Google uses. The focus here is that rather than paying for the amount of data you're processing (Azure Sentinel is rumoured to use a per-GB structure, although final pricing hasn't been announced), you pay based on the size of the organization. This means that rather than keeping a few weeks/months of data because you don't have the budget for longer-term storage in your cloud SIEM or disk space in your on-premises deployment you can keep data for years. The big benefit here is that if a domain, for instance, is identified as malicious, Backstory looks through your historical data to see if any devices accessed that domain in the past when it wasn't flagged as bad. Another strength of Backstory is the speed of ingestion and indexing -- building on Google's strengths in this area, logs are available for searching within "seconds" (I didn't test this).
Backstory was launched at the RSA conference and many companies expressed interest in building plug-ins to allow their data to be ingested easily and that's obviously an important part of evaluating a SIEM for your company -- does it work with the technologies you have in your business?
Wrapping Up
I think Azure Sentinel is a very interesting solution and I think it's further proof of where Microsoft is heading as a security company. While pricing hasn't been announced at the time of writing, I hope that Microsoft adopts Chronicle's approach, rather than charging per gigabyte, as this will limit the data the companies choose to store.
It's a bit early to compare the two cloud-based SIEMs, but I think Azure Sentinel will find a good home among companies that are heavily invested in Microsoft 365 and Azure, although the learning curve for Kusto might be a bit steep for smaller shops. Another strong point of Azure Sentinel is the link to Microsoft's Intelligent Security Graph -- a centralized database of all security signals that Microsoft collects from all its services. So, if Microsoft identifies a particular IP address as malicious, not only Azure Sentinel, but Cloud App Security, for instance, will be aware of this. This huge dataset (6.5 trillion signals a day) is a huge asset in Microsoft continuing to establish itself as a security company.
Backstory, on the other hand, has fewer connectors today and seems more focused on DNS logs and speed, but that'll change as it matures.
It will also be interesting to see how the incumbents such as AlienVault and others that already offer cloud-based SIEMs respond to Azure Sentinel and Backstory.