News
Security Exec Predicts Systemic Ransomware Launched from Hijacked Public Cloud
"Regrettably, we should expect a public cloud to be commandeered to launch a systemic ransomware attack this fall."
Cloud-jacking, in which an organization's cloud account is stolen or hijacked by an attacker, is on the rise and predicted to go mainstream, according to the seventh installment of VMware Carbon Black's Global Incident Response Threat Report.
The sweeping security report last year focused on the effects of the COVID-19 pandemic and another attack technique called "island hopping," in which attackers, in a variety of ways, first go after an organization's supply chain companies or partners as a way to penetrate the final target's cyber defenses. This year, the pandemic's effects are still being felt, but in different ways.
Emphasis on Cloud Security Tools
For one thing, the pandemic sparked a rush to cloud technology, and cybercriminals have continued to exploit these environments such that cloud security remains a top priority among organizations. Nearly half (43 percent) of respondents polled by VMware said more than a third of attacks were targeted at cloud workloads, with almost a quarter (22 percent) saying more than half were. For this reason, 6 in 10 respondents said cloud security tools are their top priority to implement.
And while the cloud remains a top attack vector, specific tactics have changed somewhat for various types of attacks, including the increasingly popular ransomware scheme in which an organization's cyber resources are locked down by an intruder, preventing corporate business until a ransom is paid to get them back.
 [Click on image for larger view.] Cloud Threats (source: VMware).
[Click on image for larger view.] Cloud Threats (source: VMware).
Cloud-Jacking and Lateral Movement
"If 2020 was the year of island hopping, where cybercriminals infiltrate large company networks by targeting third parties with lower levels of protection, then we should expect cloud-jacking through public clouds to go mainstream in 2021, particularly with the mass migrations to public clouds to support distributed workforces," said Tom Kellermann, head of cybersecurity strategy, VMware. "Regrettably, we should expect a public cloud to be commandeered to launch a systemic ransomware attack this fall."
The new report associates cloud-jacking with new "lateral movement" techniques used to facilitate destructive attacks via the ability to move around within an organization's cyber environment, from cloud to cloud, system to system, platform to platform, and so on in order to set up infrastructures to help launch attacks.
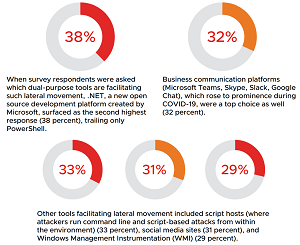
The report said 61 percent of respondents witnessed attempted lateral movement during the past 12 months, prompting Kellerman to say: "Lateral movement has modernized, allowing attackers to launch systemic destructive attacks as evidenced by the attack on Kaseya and its customers. Business communication platforms also pose real risks when it comes to facilitating lateral movement. Defenders have limited visibility, and traditional network security is inadequate to prevent adversaries from infiltrating them."
Those business communications platforms that foster lateral movement include popular offerings like Skype, Slack and Microsoft Teams. In fact, regarding that latter item, Microsoft is identified as also providing other means to foster ill-will lateral movement through other products like .NET and PowerShell:
 [Click on image for larger view.] Lateral Movement (source: VMware).
[Click on image for larger view.] Lateral Movement (source: VMware).
Key Findings
Thus cloud-jacking accounts for one of the key findings of the report, with the full list including:
- With cloud-jacking on the rise, cloud security remains a top priority. Following the rush to cloud technology amid the pandemic, cybercriminals have continued to exploit these environments to deliver integrity and destructive attacks. Nearly half (43 percent) of respondents said more than one-third of attacks were targeted at cloud workloads, with almost one-quarter (22 percent) saying more than half were. Increasingly, attackers are using the cloud to island hop along the victim's supply chain: 49 percent of all attacks targeted the victim via island hopping. This is compared to the 53 percent of all attacks our respondents witnessed that target the victim directly.
- BCC is fast becoming the new business email compromise (BEC). Catalyzed by the shift to a remote-work environment during COVID-19, adversaries are increasingly leveraging business communication platforms (e.g., Microsoft Teams, Skype, Slack, Google Chat) to move around a given environment and launch sophisticated attacks. When asked which dual-purpose tools are facilitating lateral movement (or living off the land), 32 percent of respondents chose such platforms, trailing only PowerShell and Microsoft's .NET.
- The nexus between nation-states and e-crime continues to heighten the threat landscape and exploit vulnerabilities. Among those who encountered ransomware attacks in the past year, 64 percent witnessed affiliate programs and/or partnerships between ransomware groups -- groups harbored by nation-states such as Russia. The unprecedented collaboration of cybercriminals is being used to exploit vulnerabilities more effectively than ever before (e.g., zero-day attacks), often through the use of custom malware, which was observed by respondents in more than half (52 percent) of attempted attacks.
- Half (51 percent) of defenders experienced symptoms of extreme stress or burnout, with 65 percent of respondents saying they've considered leaving their job because of it. Defenders are also looking for new ways to fight back: 81 percent said they are willing to leverage active defense in the next 12 months.
Best Practices for Security
VMware also listed best practices to address the findings above, including:
- Increase situational awareness. It is critical that organizations take a proactive and comprehensive approach to security, regardless of sector or size. Telemetry is fundamental in achieving this situational awareness and is most effective when the organization's network detection and response platform is integrated with its endpoint protection platform.
- Expand cloud security. Migration to the cloud (and cloud-jacking) shows no sign of slowing down, which must result in security that extends across workloads, containers, and Kubernetes environments.
-
Track identities on the move. Today's attacks do not have a distinct beginning or end. Instead, adversaries conduct reconnaissance to learn as much as they can about organizations and often move covertly throughout a target's network. To ensure adequate protection, security teams need the ability to accurately track identities as they move. That means:
- Implementing just-in-time administration and multifactor authentication on all external assets
- Leveraging a single sign-on (SSO) provider to allow for centralized and seamless authentication across the vastly distributed work environment
- Applying the principle of least privilege
- Operationalize hardening and patching. With attackers continuing to exploit vulnerabilities, it's critical to leverage industry best practices for hardening and patching. Ensure IT operations and security are on the same page with vulnerability data. Maintain agreed-on service-level agreements (SLAs) for patching.
- Apply micro-segmentation. Limit an adversary's ability to move laterally within the organization. For instance, forcing intruders to cross trust boundaries provides better opportunities for detection and prevention.
- Activate your threat hunting program. Prepare for the worst, hope for the best. Security teams should assume attackers have multiple avenues into their organization. Threat hunting on all devices can help security teams detect behavioral anomalies, as adversaries can maintain clandestine persistence in an organization's system. Threat hunting should be conducted on a weekly basis.
Published early this month, the report is based on an online survey of 123 cybersecurity and incident response (IR) professionals held between May and June 2021.
About the Author
David Ramel is an editor and writer at Converge 360.