In-Depth
The Definitive Ransomware Prevention & Recovery Checklist
"Ransomware is that ultimate punch in the mouth," says cybersecurity expert Allan Liska in recounting the familiar quote from champion boxer Mike Tyson, who once opined that when coming into the ring every opponent has a plan until they get punched in the mouth.
Many organizations think they are prepared to stop a ransomware attack, or at least they will be able to recover quickly.
Unfortunately, when it hits they find out just how unprepared they are.
Learning everything you need to prepare and recover from a ransomware attack is a daunting task. Luckily, Liska, an intelligence analyst at Recorded Future, has prepared a checklist to help orgs get started, shared during a recent online tech event in which he made the Tyson reference. The checklist is a valuable resource from a familiar face in the industry, as he is widely known as the "Ransomware Sommelier."
Liska's presentation was part of Converge360's "Leaders in Tech" series of online events and is now available for on-demand viewing.
Like a punch in the mouth, a ransomware attack can be sudden and devastating, said Liska, who recounted a conversation about a security pro who told leadership their org could probably recover in five days, based on a recent similar scenario. "Turned out it took them more than two months to recover because what they thought they had in place wasn't actually in place."
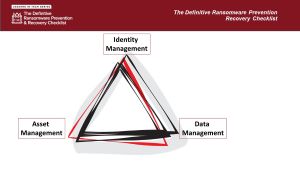
To make sure things that should be in place are in place, organizations should address three basic areas: good asset management, good identity management and good data management.
 [Click on image for larger view.]
[Click on image for larger view.]
"Those three things you're doing, those three things, you're going to be able to stop most ransomware attacks," he said, explaining each one:
- By asset management, I mean, you need to know what systems you have in your network and in your cloud, what software is running on them, where they're located, what's open and closed to the internet, etc.
- Identity management, you need to know who all the people in your network are, who, what systems they should be asking, what systems should be talking to each other and not talking to each other.
- And then data management, where is your data and how is it secured both in your network, in your cloud, in your partner's network, and in your partner's cloud.
Within those three areas, he discussed multi-factor authentication (MFA), network segmentation, patching, endpoint detection and response, backups and encryption, and table-top exercises to test all that. For full value, you need to watch the entire presentation, complete with Liska's answers to audience questions, but following is a summary of what he had to say about a few of those topics.
Note that throughout his discussion of all of those topics, Liska emphasized the point of focusing on the basics of cybersecurity, not the latest/greatest, whiz-bang, AI-powered darling gizmos of the moment.
Multi-Factor Authentication (MFA)
 [Click on image for larger view.]
[Click on image for larger view.]
"I think everybody at this point has heard of multi-factor authentication," Liska said. "It's been drilled into your head, but stolen identity is one of the most common ways for ransomware actors or their initial access brokers to gain access to networks.
"Simply put, there are millions of stolen credentials from from organizations around the world that are readily available. And while it's important to keep up whenever you do have credentials leaked, it's also just as important to make sure that you have multi-factor authentication enabled wherever you can, but especially on anything external facing.
"There are so many ransomware attacks that I see that start with a leaked credential that was used to get into a firewall or a VPN that didn't have multi-factor authentication enabled. So you've made it easier for the bad guy to basically walk into your network.
"And so anything that's external facing should have multi factor authentication enabled on it."
Further discussion about MFA involved the need to monitor for leaked and stolen credentials and recommended tools and services to help with that.
Network Segmentation
 [Click on image for larger view.]
[Click on image for larger view.]
"And again, this is one of those that is not a tool or a thing that you need to buy. It's just planning out your network. A lot of our networks grow organically. You started with small business, you get bigger and bigger, and you don't kind of plan out how you're doing that.
"But network segmentation can be really important because it can limit the scope and damage of a ransomware attack. So a ransomware attacker gets into one part of the network and they're not able to jump over to another part."
He noted that some things are complicated by Active Directory, whose domain controllers are prime targets. That's mitigated by setting up Active Directory "forests," which can be complicated.
"Again, this is something I see especially in ransomware attacks against local governments where the ransomware actor will land in like the finance department, but because it's a completely flat network, they're able to hit the police station, the fire station, the courts and encrypt everything across the board, and so effectively shutting down the whole government.
"Well, there's really no reason that the finance network should be able to see or talk to the court network or the police network or the fire department network. And so that needs to be better isolated and so you can so that you can limit the stroke of the attack. So if something does go wrong, your defenses fail, at least only part of your network is disrupted."
Patching
 [Click on image for larger view.]
[Click on image for larger view.]
"Patch systems, right, including maintaining the security of operating systems, application firmware in a timely manner. You want to consider, of course, using a centralized patch management system, but more importantly a risk-based strategy to drive your patch management program. I get that it is really hard to patch everything, and that's what everybody will tell you to do, right?"
In the real world, though, that's a lot of patching, and while experts and pundits will tell you to patch everything, that might not be realistic everywhere for time-strapped security pros, Liska noted.
"But the bad guys move very quickly in exploiting vulnerabilities. And so what you have to do is balance what the risk is to your organization and prioritize patching those systems that are the biggest risk."
For example, Liska noted that ransomware groups really love to exploit SSL VPNS, so when a new SSL VPN vulnerability is announced, especially a remote code executable one, one that has no touch, they can easily scan it and exploit it with tools like Python scripts within hours, while an org's time to patch is generally weeks, if not months.
"Well, there's a big disconnect there. And so what you want to look at is prioritizing patching those systems that are most likely to be exploited by ransomware actors and patching those quickly. And then for the things that are less of a risk of being used by ransomware actors or nation states or whatever your concern is, then you can put those on a more regular patch cadence so that you you have the time to do it because you protect it against the big things."
More On-Demand and Live
Again, the whole value of these presentations comes with actual attendance and the ability to ask experts questions, but on-demand replay is the next-best thing, where you can see what Liska had to say about endpoint detection and response, backups and encryption, and table-top testing exercises.
As for actual attendance, upcoming events presented by Converge360, the parent company of Virtualization & Cloud Review, can be found here.
About the Author
David Ramel is an editor and writer at Converge 360.