News
Security Team Contradicts Microsoft Claim of Windows 10 Security
CERT says Windows 10 should still run the Enhanced Mitigation Experience Toolkit.
A software security organization is contending that Windows 10 isn't as secure, by default, as it could be.
Software security research organization CERT is disputing Microsoft's recent claim that Windows 10 has good enough security protections without using the Enhanced Mitigation Experience Toolkit (EMET).
Microsoft had announced earlier this month that it plans to deprecate its own EMET solution, a free software tool that wards off common software exploit attacks for Windows systems. EMET provides system-wide protections, as well as application-specific protections. It was first developed as project at Microsoft, but it later became a full-fledged Microsoft-supported tool. It's currently at version 5.5.
EMET will hit its product end-of-support phase on July 31, 2018. Microsoft indicated that EMET is being discontinued because it just wasn't up to the task of halting "zero-day" attacks, or attacks carried out on software flaws that are not understood by software publishers. Instead, Microsoft suggested that Windows 10 had some of EMET's capabilities built into the operating system, and organizations should move to using it, although some of those protections require using the Enterprise or Education editions of Windows 10.
CERT mostly contradicted Microsoft's Windows 10 security claims this month. "Windows 10 does not provide the additional protections that EMET does," the organization stated in a Nov. 21 blog post.
The well-known research organization, which works with the U.S. Department of Homeland Security and industry organizations to address software security issues, published the following table, which shows the protections afforded for Windows systems, both with and without EMET:
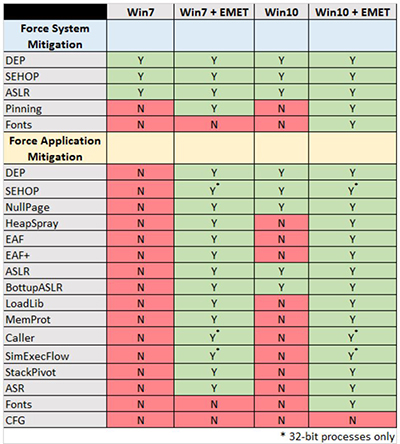 [Click on image for larger view.]
Security protections with and without EMET. Source: November CERT blog post.
[Click on image for larger view.]
Security protections with and without EMET. Source: November CERT blog post.
Specifically, EMET has security benefits for organizations because it adds protections against application-specific exploits, CERT argued.
Windows 10 version 1607, released this week for business use, does have some application protections, but not as many as EMET. The application protections in Windows 10 include Data Execution Prevention (DEP), Structured Exception Handler Overwrite Protection (SEHOP), Mandatory Address Space Layout Randomization (ASLR) and Bottom-Up Randomization (BottomupASLR), according to CERT's announcement. However, CERT's post noted that organizations have to make Group Policy changes to enable those Windows 10 application protections.
"Setting these application-specific mitigations requires calculating and setting a bit field value in the Windows registry for each process name that you would like to protect," CERT noted. "Please see Override Process Mitigation Options to help enforce app-related security policies for more details."
In essence, organizations running Windows 10 will still need to use EMET, according to CERT.
"Microsoft strongly implies that if you are running Windows 10, there is no need for EMET anymore," the CERT blog stated. "This implication is not true. The reason it's not true is that Windows 10 does not provide the application-specific mitigations that EMET does."
EMET's end-of-support in 2018 implies that organizations have a timeline to ensure that the shields are up for the applications they use. CERT recommended that organizations should "investigate all of the software that is currently outside of the support window before July 31, 2018."
EMET's end will happen 1.5 years before the end of Windows 7 Service Pack 1. The end of "extended support" for Windows 7 SP1 is set to occur on Jan. 14, 2020. Consequently, EMET's early end might persuade some organizations to move to Windows 10 sooner than they might have planned.
So far, Microsoft has offered no response to CERT's claims about Windows 10 protections being inadequate without EMET. While many software security vendors raise alarming claims about Windows security on a regular basis, CERT is a division of the Software Engineering Institute, part of Carnegie Mellon University. It doesn't tend to ring the bell except when there's broad agreement on security issues.
Microsoft, though, appears to be sticking with its original EMET deprecation announcement, and offered no comment on CERT's claims when contacted on Wednesday.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.