News
Study IDs Permissions Risks in Major Cloud Platforms
A new report published by CloudKnox dives into the "cloud permissions gap crisis" on major cloud platforms, identifying risks caused by improper Identity and Access Management (IAM).
The company says its CloudKnox Security offering is the only cloud permissions management platform provider for hybrid and multi-cloud environments. Its Threat Labs research uses risk assessment data from 150 global organizations in the State of Cloud Entitlements Report (free PDF download upon providing registration information).
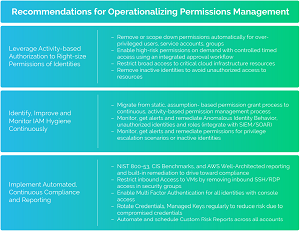 [Click on image for larger view.] Recommendations (source: CloudKnox).
[Click on image for larger view.] Recommendations (source: CloudKnox).
In addition to the usual "Big 3" cloud computing providers Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP), the report also covers VMware's vSphere.
Here's how the company's April 13 news release summarized findings for all of the above:
-
AWS:
- More than 95 percent of identities are using less than 2 percent of permissions granted.
- Two-thirds of most enterprises have Elastic Compute Cloud (EC2) instances with access to all Simple Storage Service (S3) buckets.
- More than 50 percent of enterprises have identities with privilege escalations ability to elevate to super admin roles.
-
Azure:
- More than 90 percent of identities are using less than 2 percent of permissions granted.
- More than 85 percent of enterprises have over-permissive identities left orphaned after projects are terminated.
- 65 percent of all enterprises have anonymous public read access enabled for blob containers in production environments.
-
GCP:
- More than 90 percent of identities are using less than 5 percent of permissions granted.
- More than 80 percent of projects have service accounts (including Google managed) with over-permissive Owner/Editor roles either directly attached or inherited from a folder or organization.
- More than 85 percent of enterprises have user managed keys for service accounts that are not rotated.
- More than 50 percent of enterprises have project-wide Secure Shell (SSH) keys enabled for virtual machine (VM) instances.
-
vSphere:
- More than 95 percent of identities are using less than 5 percent of permissions granted.
- More than 60 percent of groups and identities accessing the vSphere infrastructure are inactive and have high-risk permissions.
- Highly over-provisioned "Destroy," "Remove" and "Reset" functions for compute, storage and network across poorly defined roles.
"As organizations modernize IT and adopt hybrid and multi-cloud infrastructures to support evolving business processes involving human and non-human identities, it's increasingly difficult to know who has access to what data, across which platforms," the report's summary states. "This lack of visibility leads to over-permissioned and high-risk identities, which causes a myriad of problems, including accidental or malicious insider threats."
Recommended steps to reduce organizational risk include:
- Continuously monitor, remediate and enforce security controls to ensure compliance
- Automate policy enforcement, enforce least privilege and deliver permissions on demand
"The Cloud Permissions Gap is a contributing factor to the rise of both accidental and malicious insider threats as attackers are able to exploit an identity with misconfigured permissions and access your critical cloud infrastructure," the report states. "This delta is a key factor leading to identities becoming the new security perimeter and the emerging attack vector to exfiltrate business-critical data. The best way to reduce this gap and protect cloud environments is through implementing least privilege policies and working towards a Zero Trust model."
About the Author
David Ramel is an editor and writer at Converge 360.