News
Cybersecurity Threatscape: Ransomware Reigns, Accounting for 63% of Malware
You need only look at recent news headlines to see how costly ransomware attacks are plaguing enterprises these days, but a new report puts some data behind the troubling accounts.
Positive Technologies this week published its Cybersecurity Threatscape Q1 2021 research report, revealing a continuing rise in cyber incidents, with ransomware accounting for nearly two-thirds of all malware attacks.
The report indicates that ransomware is still the most common malware, with its share, among other malware used in attacks on organizations, increasing by seven percentage points compared to Q4 2020, so it now accounts for 63 percent of all malware.
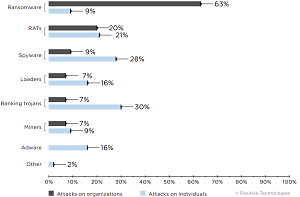 [Click on image for larger view.] Types of malware (percentage of malware attacks) (source: Positive Technologies).
[Click on image for larger view.] Types of malware (percentage of malware attacks) (source: Positive Technologies).
"Ransomware is still the malware that is most often used by attackers," the report says. "In Q1, they demanded astronomical ransoms and refined their arsenal, including adding new ways to hide from security tools." Those new ways to hide from security tools include using unpopular programming languages, such as Nim, D and Golang.
Email remains the prevailing attack vector, as the bad guys used it in six out of 10 malware attacks on organizations. Individuals, however, are still most often attacked by other means, including banking trojans, spyware and malware that provides remote access to devices.
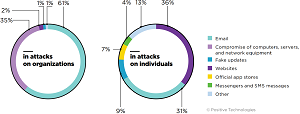 [Click on image for larger view.] Methods used for malware distribution (source: Positive Technologies).
[Click on image for larger view.] Methods used for malware distribution (source: Positive Technologies).
The five most active ransomware programs used in Q1 2021 were:
- REvil
- Clop
- Conti (Ryuk)
- Babuk Locker
- DoppelPaymer
Anyone reading those aforementioned ransomware headlines may have heard of the Russian ransomware gang REvil, short for "Ransomware evil," and the report sheds more light on that threat:
In Q1 2021, REvil operators broke all records in ransom demands. They demanded $50 million after attacking the IT company Acer, and, after encrypting the network of the pan-Asian retail chain Dairy Farm Group, demanded 30 million in exchange for a decryptor and nondisclosure of the stolen data. Such large amounts are due to the ask-more-to-get-more tactic. The incident with the retailer FatFace speaks to the success of the campaign. In early January, Conti (Ryuk) operators penetrated the company's network by conducting a phishing attack, and after seven days of reconnaissance, extracted 200 GB of data and started the encryption process. Initially, the attackers demanded $8 million. However, during the negotiations, the amount was reduced to 2 million, which satisfied both parties.
Due to the fact that some companies refuse to pay the ransom, ransomware operators are forced to come up with new tactics. These days, if the company is refusing to pay, the attackers threaten to report the attack and the data theft to its customers. The fraudsters expect that the customers will persuade the company to pay a ransom to prevent the disclosure of their data.
REvil is also known for attacking meat supplier JBS Foods this spring and Kaseya, an IT software company, over the July 4 holiday weekend, but just lately the gang seems to have gone offline.
While REvil leads the list of known programs used in attacks in Q1, the report also finds that Q1 saw several new pieces of ransomware emerge -- for example, Cring, Humble, and Vovalex. "And WannaCry is reported to be running rampant again, which made a name for itself in 2017," the report says.
Other highlights of the report include:
- The number of attacks increased by 17 percent compared to Q1 2020, and compared to Q4 2020, the increase was 1.2 percent, with 77 percent being targeted attacks. Incidents involving individuals accounted for 12 percent of the total.
- The most popular vulnerabilities for attackers this quarter were breaches in the Microsoft Exchange Server software (ProxyLogon) and the outdated file sharing program Accellion FTA. Attackers used a zero-day vulnerability discovered in SonicWall VPN solutions not just to hack the company, but also to launch attacks on its customers. SonicWall presumably failed to notify its customers in time about the identified vulnerability or a need to implement protective measures. The incident supports the argument that software manufacturers should inform their customers as soon as possible about existing vulnerabilities and ways of protecting themselves until a patch is released.
- More and more cybercriminals are developing malware to conduct attacks on virtualization environments, and some are aggressively trying to exploit vulnerabilities already found in software for deploying virtual infrastructure.
- The number of attacks targeting IT companies has remained consistently high for a second quarter in a row. In 15 percent of cases during Q1 2021, hackers targeted IT companies to conduct an attack on their customers or to steal customer data. At the beginning of 2021, there were still reports in the media about new victims of the attack on SolarWinds: the company's customers claim that their networks have been compromised.
- Telecom companies were twice as likely to be attacked as in Q4 2020. In 71 percent of the attacks, hackers aimed at obtaining data, with a particular interest in the 5G technology. Nine out of 10 incidents saw attackers use malware -- most frequently, RATs, which accounted for 55 percent of all attacks.
"To protect from cyberattacks, follow our general recommendations for ensuring personal and corporate cybersecurity," concluded Positive Technologies, which sells enterprise security solutions. "Also, given the specifics of the attacks in the past quarter, we strongly recommend that you install security updates in a timely manner and pay special attention to protecting virtual infrastructure. You can strengthen security at the corporate perimeter by using modern security tools, for example, web application firewalls for protecting web resources. To prevent malware infection, we recommend using sandboxes to analyze the behavior of files in a virtual environment and detect malicious activity."
Data backing the report comes from Positive Technologies expertise and investigations, along with data from authoritative sources, the company said.
About the Author
David Ramel is an editor and writer at Converge 360.