News
Top Linux Malware? Not Ransomware, but Coinminers
"Given that the cloud holds a seemingly endless amount of computing power, hackers have a clear motive in stealing computing resources to run their cryptocurrency mining activities."
With ransomware wreaking havoc on the malware scene these days in a barrage of high-profile attacks, a new study on Linux security shows it's only third on the list of top threat types.
Taking the top two spots are malware threat types that don't get near as much attention as does ransomware: coinminers and web shells. That perhaps surprising finding comes in the new Linux Threat Report 2021 1H: Linux Threats in the Cloud and Security Recommendations report published Aug. 23 by cybersecurity specialist Trend Micro.
But to Trend Micro, the high ranking for coinminers -- malware that puts infected devices to work generating crytpocurrencies like Bitcoin -- isn't so surprising.
"The high prevalence of cryptocurrency miners is of little surprise given the clear motive of the seemingly endless amount of computing power the cloud holds, making it the perfect environment," the company said.
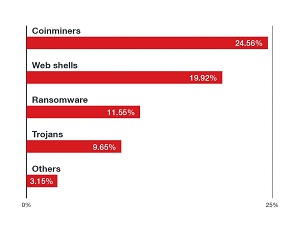 [Click on image for larger view.] Top 10 Malware Families Detected by Threat Types in the First Half of 2021. (source: Trend Micro).
[Click on image for larger view.] Top 10 Malware Families Detected by Threat Types in the First Half of 2021. (source: Trend Micro).
In releasing new research on the state of Linux security in the first half of 2021, the firm said it aimed to deliver insight into how Linux OSes are being targeted in a time when organizations are increasing their digital footprints in the cloud. Linux is the subject because of its dominant position in the cloud, with various reports indicating:
- All of the world's top 500 supercomputers run on Linux
- Slightly more than half of the top 1,000 web sites in the world use Linux (and out of the top 25 web sites in the world, only two aren't using Linux)
- Linux reportedly ran 90 percent of public cloud workloads in 2017
The above ranking of top threat types affecting Linux servers from Jan. 1, 2021, to June 30, 2021, is based on data from Trend Micro security products. Some Windows-based malware families made the list because attackers sometimes use Linux servers as storage or command-and-control (C&C) servers for Windows malware.
Web shells, No. 2 on the list, refers to shell-like interfaces that can be used to remotely access a server, often for cyberattacks. "The recent Microsoft Exchange Attack, which leveraged web shells, showed the importance of patching against this type of malware," Trend Micro said. As far as ransomware, which an increasing number of organizations are learning about firsthand, the company said the most prevalent threat detected was the DoppelPaymer, described as "a modern ransomware family," with some other notable ransomware families seen targeting Linux systems include RansomExx, DarkRadiation and the DarkSide.
Summarizing the threats in general, the report said: "Given that the cloud holds a seemingly endless amount of computing power, hackers have a clear motive in stealing computing resources to run their cryptocurrency mining activities. It's also important to note that cryptocurrency miners have been plaguing container environments in recent years. We also saw ransomware as a prevalent Linux threat, and DoppelPaymer, a modern ransomware family that utilized double extortion tactics, is the most prevalent ransomware family based on our data. In our monitoring of the ransomware landscape, we have also recently seen other ransomware variants that were targeting Linux systems such as RansomExx, DarkRadiation and even DarkSide."
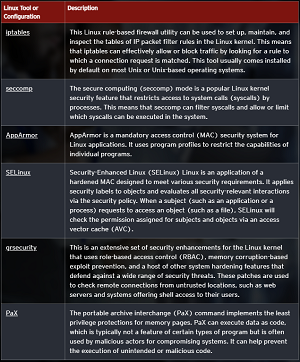 [Click on image for larger view.] Native Linux Tools or Configurations. (source: Trend Micro).
[Click on image for larger view.] Native Linux Tools or Configurations. (source: Trend Micro).
The report also covers many other topics in addition to malware, discussing other vulnerabilities, container security, web-based attacks as viewed under the Open Web Application Security Project (OWASP) lens, open source security (OSS) and software supply chain attacks (SSCA) and much more. As far as advice on securing Linux servers, Trend Micro touted its own security products, third-party tools/controls and native Linux tools and configurations, with the latter depicted in the graphic above. The report also provides guidance on securing containers and securing code via application security and testing.
"Given how deeply Linux is rooted in daily life, especially as an integral part of cloud infrastructure and the internet of things (IoT), the security of Linux and Linux workloads must be treated at par with that of Windows and other operating systems," Trend Micro concluded. "Users and organizations should always apply security best practices, which include utilizing the security by design approach, deploying multilayered virtual patching or vulnerability shielding, employing the principle of least privilege, and adhering to the shared responsibility model."
Data backing the report primarily comes from the Trend Micro Smart Protection Network (SPN), which serves as a data lake for all detections across all of the company's products. The firm also collected data from honeypots, sensors, anonymized telemetry and other backend services.
About the Author
David Ramel is an editor and writer at Converge 360.