News
Ransomware Protection: Use MFA and 'Don't Trust Anyone or Anything'
Two key ways to protect cloud data from ransomware and other attacks are to use Multi-Factor Authentication (MFA) and "don't trust anyone or anything."
That's according to Joey D'Antoni, a cloud data protection expert and principal consultant at Denny Cherry and Associates Consulting. His security tips came in a recent, three-part online Ransomware & Cloud Data Protection Summit produced by Virtualization & Cloud Review, specifically in a session titled "Cloud Data Protection Best Practices for AWS & Azure."
 "One of the things you need to do is limit your trust -- your blast radius -- for a data breach or an application failure."
"One of the things you need to do is limit your trust -- your blast radius -- for a data breach or an application failure."
Joey D'Antoni, Principal Consultant, Denny Cherry and Associates Consulting
While D'Antoni covered a wide range of topics in his presentation -- including perimeter security, encryption, backups, high availability and more -- his remarks on MFA were concise and direct, accompanied by a slide that virtually SHOUTED at the audience to hammer home his point on this crucial security technology.
 [Click on image for larger view.] MFA GOOD! (source: Virtualization & Cloud Review).
[Click on image for larger view.] MFA GOOD! (source: Virtualization & Cloud Review).
"This is going to be pretty short," he began. "And let's say this slide, I did make this slide in ALL CAPS. And the slide is a reminder for you to use Multi-Factor Authentication if you aren't already. Yes, you should use it for any account that supports it. Yes, I am yelling at you. Good security is harder. And this is one of those things you kind of just have to blame the bad guys for, right?"
D'Antoni isn't the first Virtualization & Cloud Review security speaker to emphasize the importance of MFA. It's emerging along with best practice techniques like Zero Trust and regular system backups in the fight against ransomware, which is regularly making headline news as one attack (and corresponding ransom payout) after another are reported in the press.
In fact, MFA figured prominently in a recent presentation by Dale Meredith, a cyber-security trainer and Pluralsight author, titled "Ransomware Recovery: What to do if You're Hit and You Didn't Have a Plan."
Meredith said: "We need to enforce our MFA. Enabling Multi-factor Authentication for everybody is going to save you so much time." People understand MFA, which is being enforced by social media and other companies now, he said. People are doing it right now with banking apps and such, so it's not a new concept and users can readily adapt to it.
Also, MFA was the subject of a recent article written by Virtualization & Cloud Review contributor Brien Posey titled "Enabling Virtual Multi-Factor Authentication for AWS."
 "One of the most important things that you can do to ensure the security of your AWS accounts is to enable Multi-Factor Authentication."
"One of the most important things that you can do to ensure the security of your AWS accounts is to enable Multi-Factor Authentication."
Brien Posey, 19-Time Microsoft MVP, Freelance Writer
"One of the most important things that you can do to ensure the security of your AWS accounts is to enable Multi-Factor Authentication," said Posey, who explains how to set it up for an AWS user in a way that allows them to use their smartphone as an access key.
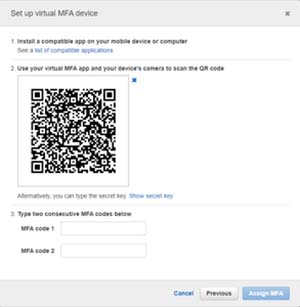 [Click on image for larger view.]MFA on AWS: Users Install an App and then Scan the QR Code.
[Click on image for larger view.]MFA on AWS: Users Install an App and then Scan the QR Code.
Seeing as how both D'Antoni and Posey discussed MFA as implemented on the AWS cloud platform, here's what AWS has to say about its use of MFA:
AWS Multi-Factor Authentication (MFA) is a simple best practice that adds an extra layer of protection on top of your user name and password. With MFA enabled, when a user signs in to an AWS Management Console, they will be prompted for their user name and password (the first factor -- what they know), as well as for an authentication code from their AWS MFA device (the second factor -- what they have). Taken together, these multiple factors provide increased security for your AWS account settings and resources.
"This is something we have to do now," D'Antoni emphasized. "And just to take this a couple of steps further -- because we've seen a recent attack or somebody's cellphone got hijacked too -- if you have the option on any of your accounts to not use SMS or calling for your Multi-Factor Authentication, do that, because app-based authentication is more secure. And I implore you: Anywhere you can try an MFA, do this, even in your personal life through your bank account, through your cable provider purchase, or your thermostat. Any of those places, it's a good idea to turn on MFA. And like I say, you probably want to avoid the text message thing. It's better than nothing, but the app-based authentication -- it's just kind of easier to deal with anyway. But it's also way more secure."
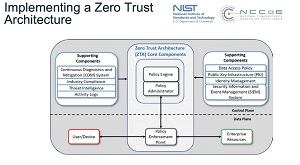 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
As mentioned, Zero Trust works right along with MFA and other cloud security best practices.
Zero Trust eschews the standard security approach of walling off networks and systems behind a secure perimeter. It's one of the latest security darlings in an industry that has seen the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, Zero Trust assumes that such fortress security approaches are destined to fail and that systems have already been penetrated, seeking to lessen the damage that can be caused.
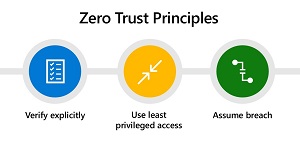 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
As we reported a couple weeks ago, Microsoft is backing Zero Trust to fight ransomware. The company's guidance associates Zero Trust with MFA and other tools and techniques used to drive Zero Trust implementations:
- Strong authentication. Ensure strong Multi-Factor Authentication and session risk detection as the backbone of your access strategy to minimize the risk of identity compromise.
- Policy-based adaptive access. Define acceptable access policies for your resources and enforce them with a consistent security policy engine that provides both governance and insight into variances.
- Micro-segmentation. Move beyond simple centralized network-based perimeter to comprehensive and distributed segmentation using software-defined micro-perimeters.
- Automation. Invest in automated alerting and remediation to reduce your mean time to respond (MTTR) to attacks.
- Intelligence and AI. Utilize cloud intelligence and all available signals to detect and respond to access anomalies in real time.
- Data classification and protection. Discover, classify, protect, and monitor sensitive data to minimize exposure from malicious or accidental exfiltration.
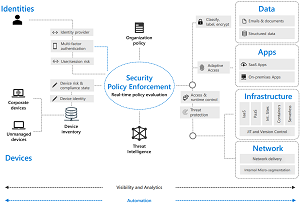 [Click on image for larger view.] Zero Trust Model (source: Microsoft).
[Click on image for larger view.] Zero Trust Model (source: Microsoft).
D'Antoni, as shown in the following graphic from his presentation, discussed trust with a focus on four main pieces of advice:
 [Click on image for larger view.] Trust Topics (source: Virtualization & Cloud Review).
[Click on image for larger view.] Trust Topics (source: Virtualization & Cloud Review).
"So, trust: Don't trust anyone or anything," D'Antoni said. "One of the things you need to do is limit your trust -- your blast radius -- for a data breach or an application failure. So you want to limit how one system can impact another. And that's by doing network network segregation, moving these limiting roles, only using privileged identity management, so you're heavily automating administrative stuff.
"And you want to take advantage of cloud tools, and recommended best practices -- similar security tools that will tell you the good things to do. Those are important. And you should understand what you need to do, versus what you need to buy. So there are certain things you can just do to build a strong security posture. And there may be other things you can devise to help accelerate that, and classic build-versus-buy decisions, but they come at you a little bit faster in the modern world."
As stated, there's much more to be learned from D'Antoni's hour-long presentation, which is now available for on-demand viewing free of charge -- along with slides and other resources -- from the Virtualization & Cloud Review webcast site. Along with many on-demand presentations, some upcoming events related to security in general and ransomware in particular include:
Stay tuned for more articles and presentations about keeping enterprise IT systems safe from ransomware and other cybersecurity attacks.