News
Cloud Native Security Survey: Kubernetes Defaults 'Too Open'
Respondents to a cloud native security survey said default settings for the Kubernetes container orchestration platform are "too open." That problem hinders secure production deployments and will require effort and maturity to solve, according to a new post from the Cloud Native Computing Foundation (CNCF).
The post, published this week during the KubeCon + CloudNativeCon North America 2021 online tech event, actually focused on another "microsurvey" of more than 125 respondents, conducted with the help of the CNCF Security Technical Advisory Group (Security TAG) aiming to see how organizations are managing cloud native security. The Kubernetes problem cited above actually came in another recent retrospective Security TAG survey that was cited in the post. It was conducted following the publication of a Cloud Native Security Whitepaper.
In anecdotal feedback, participants in that retrospective survey said the cloud native security community should address the aforementioned "too open" Kubernetes default settings problem in the following ways:
- Work on providing production-ready recipes like network policies and OPA Gatekeeper constraint templates.
- Push for more buttoned-up defaults like disabling auto-mounting service account tokens and enabling audit logging.
- Introduce friendlier docs on how to increase observability and use OPA Gatekeeper.
- New open source tools to identify image vulnerabilities effortlessly (both at runtime and in the registry).
Turning back to the main CNCF microsurvey announced in the post, it indicated more than 80 percent of organizations want to build modern security systems with open source software.
However, doing that comes with many challenges.
For example, one key takeaway from the new CNCF microsurvey report is that while respondents take cloud security seriously, few are taking appropriate steps to achieve it. Specifically, findings indicate that while 85 percent of respondents indicated that modernizing security is very important to their organization's cloud native deployment, only 9 percent had a fully documented set of procedures that are implemented automatically for their teams.
"So, while organizations recognize the importance of having these policies in place, there is still a very long way to go as a community to increase adoption and develop tooling to ease the burden of implementation," the CNCF said in the Oct. 12 blog post announcing the survey results.
One common problem faced by users of open source software in today's cloud-native cloudscape is the use of third-party code that could be insecure, containing vulnerabilities or even malware, and the new report shows 12 percent of organizations said their processes and policies for securing third-party software were non-existent. "Many organizations are leaving themselves vulnerable," the report said. "In these cases, employees are likely overworked, burned out, dealing with fires, and playing catch-up before another incident happens. They are much less likely to proactively improve security or innovate in that space."
Another takeaway repeats a familiar refrain: a top challenge in running cloud-native environments is a lack of technical expertise, reported by 58 percent of the respondents.
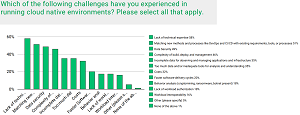 [Click on image for larger view.] Top Challenges (source: CNCF).
[Click on image for larger view.] Top Challenges (source: CNCF).
"This is not surprising as talent shortages have been reported in many other areas of software development," the survey said. "Also, cloud native security is a broad field, so the demand for security professional talent is high."
It's also not surprising because this the same exact problem that's often mentioned in cloud computing surveys -- including those about Kubernetes -- as Virtualization & Cloud Review reported in the articles:
Other highlights of the two surveys as listed by the CNCF include:
- Because of the recent focus on supply chain security, participants noted vulnerability management and secrets management as the top two cloud native security-related concerns.
- 47 percent of participants preferred not to disclose security-related incidents. For those that were will, the top two incidents were vulnerabilities being exploited or cryptocurrency miners. Interestingly, only 4 percent of participants noted that they had witnessed a ransomware attack.
- 85 percent of participants requested the community to focus on secure defaults, with 60 percent of participants requesting more focus on automated tooling and reference guides each.
- 35 percent of respondents indicated their organizations use a combination of manual with automated processes to enact policies and procedures. Another 22 percent said they do it as they have time and focus on the really important ones but were leaving a lot on the table. This indicates too much noise in tooling to drive these processes and not enough signal to make automation possible. As a result, organizations have to work by trial and error to find the tools that provide value and context to drive policy decisions.
- Even though very few organizations reported having processes and policies firmly in place, 82 percent of respondents said it's important that the security systems they implement are built using open source software. No one indicated that they felt open source was too risky to trust, a sign that Linus' Law is well understood.
- Looking at the next two to five years, organizations have big plans for security. Nearly 73 percent of respondents said their organizations intend to focus efforts on enforcing organizational policies such as no "critical vulnerabilities "or only allowing signed artifacts. More 68 percent said they would focus on improving monitoring and actionable detection of runtime workloads in the same timeframe. Three-fifths (60 percent) said their organization intends to execute container isolation for multi-tenant deployments and third-party cloud providers.
The CNCF said that the Security TAG is working on several key efforts based on the responses of the retrospective survey and community-driven discussions.
"The Cloud Native 8 is a first attempt to provide the community with clear guidance on secure defaults. There is currently a public comment open on the topic, closing on October 31st," it said.
"The group is also working on a supply chain security reference architecture designed to show organizations how to stack cloud native projects to solve a growing problem space: supply chain security. It has also launched its first version of the Cloud Native Security Map (CNSMap) and have begun working on 2.0. The goal of the CNSMap is to provide more actionable information about how to secure an organization's cloud native ecosystem."
About the Author
David Ramel is an editor and writer at Converge 360.