News
Death Knell for the VPN?
Industry analysts, pundits and IT pros are sounding a death knell for virtual private networks (VPNs) in the enterprise -- or at least an obsolete knell.
Although VPN use surged early on during the COVID-19 pandemic in a remote-work explosion, VPNs were soon found to be lacking in the security department. As we reported in August 2020, a VMware Carbon Black Global Incident Response Threat Report found VPNs to be a weak spot: "With COVID-19 comes a surge in cyberattacks. Security teams are struggling to keep up. 53 percent of IR professionals we surveyed encountered or observed an increase in cyberattacks exploiting COVID-19. They pointed to remote access inefficiencies (52 percent), VPN vulnerabilities (45 percent) and staff shortages (36 percent) as the most daunting endpoint security challenges in this regard."
 "I think that the conversation around VPN obsolescence points to the idea that things will become increasingly decentralized and we need something that can handle that decentralization better than a VPN can."
"I think that the conversation around VPN obsolescence points to the idea that things will become increasingly decentralized and we need something that can handle that decentralization better than a VPN can."
Brien Posey, Freelance Author, 20x Microsoft MVP, Commercial Astronaut Candidate
Virtualization & Cloud Review writer Paul Schnackenburg noted the remote work upsurge and potential security concerns in an article earlier that year, "Securing Remote Work Setups in the Age of COVID-19."
"Many businesses still use VPN technology for Work from Home (WFH) scenarios, particularly where a lot of company data still exists on-premises," he said. "But these VPN systems may have had to be scaled up from a small subset of staff that access them regularly to a much larger group of people. Make sure you pay particular attention to logging and reviewing this access as this could be a vector for attack."
VPN security vulnerabilities were further called out in a Teradaci study in November 2020, as detailed in the article, "Cybersecurity Study Sees Zero Trust Replacing VPNs."
"The pandemic has caused a fundamental shift in how people work, and the 'office' will never be the same," said exec Ziad Lammam at the time. "As a result of the enormous security concerns associated with unmanaged devices, as well as BYOD, organizations are changing how they think about securing their corporate assets. Expect to see companies move away from traditional VPNs to Zero Trust architectures to shore up their endpoints and protect their data."
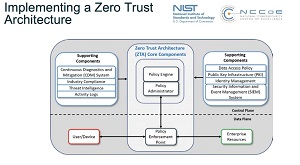 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
However, while many other studies and blog posts have echoed similar thoughts lately, the demise of the VPN approach in favor of Zero Trust was heralded way back in 2019 by analyst firm Gartner, which predicted (pre-pandemic): "By 2023, 60 percent of enterprises will phase out most of their remote access virtual private networks (VPNs) in favor of ZTNA [Zero Trust Network Access]." With pandemic concerns kicking in since then, that estimate might have increased.
Certainly analysts, experts and pundits have since then picked up the pace on their VPN warnings, as evidenced by just a few examples:
- Why VPNs Will Be Obsolete in 2021 -- Decmber 2020: "Virtual private networks (VPNs) are becoming more obsolete, largely due to web applications being internet accessible and as powerful as their thick client predecessors that required VPNs. Plus, they are already encrypted with strong and robust cryptographic protocols like TLS."
- Is the VPN obsolete? -- October 2021: "Traditional remote access VPN is increasingly out of step with the distributed world of the cloud."
- The VPN Is Obsolete. Here's What to Do Instead. -- July 2020: "Businesses that transition to a zero-trust security architecture find they have little use for their old virtual private networks."
To get expert opinions on all of this from IT pros on the front lines, I asked Virtualization & Cloud Review writers about their thoughts.
One of those writers is Brien Posey, a 20-time Microsoft MVP, former CIO, author and presenter, who said he had also heard about the purported demise of VPNs and wondered if it was true. "Even if user VPNs were to go away though, I suspect that point-to-point VPNs may remain in place for some time to come simply because they provide a secure, private tunnel between networks," he said.
"This can be really helpful when you have services running in different clouds and using something like TLS isn't an option. In any case, I think that the conversation around VPN obsolescence points to the idea that things will become increasingly decentralized and we need something that can handle that decentralization better than a VPN can."
Another writer, the aforementioned Paul Schnackenburg, also differentiated between different types of VPN connections: site-to-site and point-to-site. He has been working in IT for nearly 30 years and has been teaching for over 20 years, also running Expert IT Solutions, an IT consultancy in Australia.
He said site-to-site (or permanent) VPNs are still heavily used to connect sites over the internet from router to router. However, point-to-site (P2S) VPNs, which are client-to-corporate network connections, "are definitely in decline."
Schnackenburg shared his thoughts on that: "Main reason -- 10-15 years ago everything you needed was on-premises. SharePoint, Exchange servers, file shares and all LOB applications were all on-prem -- only way to get to them was to VPN back into the office network" he said. "Today, most of those applications are SaaS and you connect to them over the internet. Additional reason is capacity -- at the beginning of Covid lock-downs two years ago, many businesses sent staff home only to find that they were all connecting over links/systems only designed for ~10% of staff (traveling salespeople, executives etc.) and as a result, no one could work until capacity was added. Another reason is security -- when you do a client-to-corp office VPN, you have established a connection from network to network so malware/attackers on the home network can connect into the full corporate network (subject to network segmentation). Final reason is that many VPN devices have [poor] security (yes, major brands like Cisco and others) and are routinely exploited by attackers -- again if you can breach a VPN device you're 'on the network' and have full access to continue to move laterally."
See the Q&A sidebar with Schnackenburg for his other thoughts on the matter.
With Zero Trust often mentioned as the optimal replacement for VPNs more information on that is available in the on-demand webcast Moving the Endpoint from VPN to Zero Trust, which discusses:
- Why Zero Trust demands more than a VPN when enabling the remote workforce
- Where the VPN falls down as a security measure
- How modern Cloud-based desktops transform the traditional endpoint into a productive workspace that meets Zero Trust needs
A simple internet search shows a ton more guidance is available on the same subject, from a variety of sources.
About the Author
David Ramel is an editor and writer at Converge 360.